Hardware giant MSI confirms cyberattack after new ransomware group issues demand
Taiwanese hardware maker Micro-Star International (MSI) confirmed Friday that it was the victim of a cyberattack following reports that said a new ransomware group targeted the company.
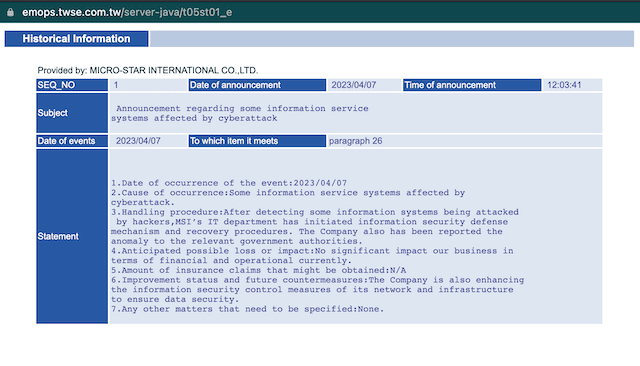
In its statement, MSI did not specify when the attack occurred but said the incident was reported to law enforcement agencies “promptly” and recovery measures have been initiated.
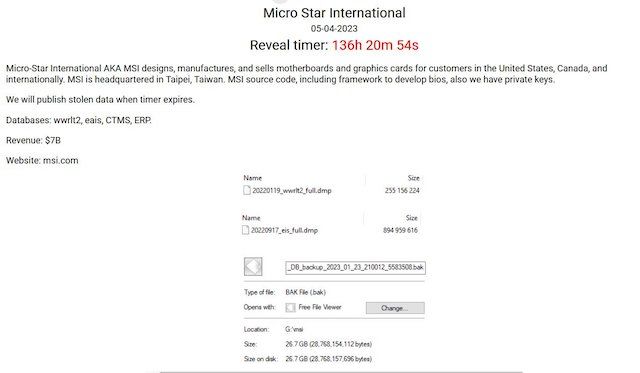
This week, the Money Message ransomware group added the company to its list of victims, claiming to have stolen source code, firmware, frameworks and more. Cybersecurity researchers said the group only emerged this week.
MSI, based in New Taipei City, brought in more than $6.6 billion in revenue in 2021 through its work designing and developing computer hardware, including laptops, desktops, motherboards and graphics cards.
“Currently, the affected systems have gradually resumed normal operations, with no significant impact on financial business. MSI urges users to obtain firmware/BIOS updates only from its official website, and not to use files from sources other than the official website,” the company explained.
“MSI is committed to protecting the data security and privacy of consumers, employees, and partners, and will continue to strengthen its cybersecurity architecture and management to maintain business continuity and network security in the future.”
 MSI's notice about the incident.
MSI's notice about the incident.
The company also submitted regulatory filings to The Taiwan Stock Exchange on Friday, writing that it did not expect any losses or impacts from the cyberattacks.
In messages seen by BleepingComputer, the group claimed to have taken 1.5TB of data and issued a ransom demand of $4 million. The ransomware gang appears to have emerged only in the last week, with at least one victim coming forward on the tech news site’s forum on March 28.
Zscaler's ThreatLabz also wrote March 29 on Twitter that it witnessed the group “performing double extortion attacks” — where groups demand ransoms for not only unlocking encrypted data but also for not leaking what was stolen.
Researchers at Cyble said on Thursday that the group “can encrypt network shares and targets both Windows and Linux operating systems.”
“Money Message was first observed in March 2023 and has already affected more than five publicly disclosed victims, with the majority of them being from the United States,” the researchers said.
“In a specific instance, the group demanded a ransom of $500,000, which may vary depending on the targeted organization’s revenue. Additionally, Money Message is capable of encrypting network shares, and its approach to target network shares resembles that of the Maze and Petya ransomware.”
 Ransomware group's notice to MSI.
Ransomware group's notice to MSI.
Several Taiwanese hardware vendors have faced ransomware attacks over the last three years, including QNAP, Delta Electronics, GIGABYTE, Acer, Quanta and more.
Multibillion-dollar corporation Applied Materials, which provides technology for the semiconductor industry, was also affected by a ransomware attack on a supplier that they predict will cost it $250 million in the next quarter.
Recorded Future, which owns The Record, released a report in September detailing how several of the world’s leading semiconductor companies faced ransomware attacks, extortion attempts and other malicious activity in 2022.
Correction (4/9/2023): An earlier version of this story said that the Money Message group shared information with BleepingComputer. The publication had seen the messages prior to their disclosure, but had never spoken to the group.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



