Semiconductor industry faced 8 attacks from ransomware groups, extortion gangs in 2022
Several of the world’s leading semiconductor companies have faced ransomware attacks, extortion attempts and other malicious activity in 2022 — right as the industry became critical to the world's technology sector.
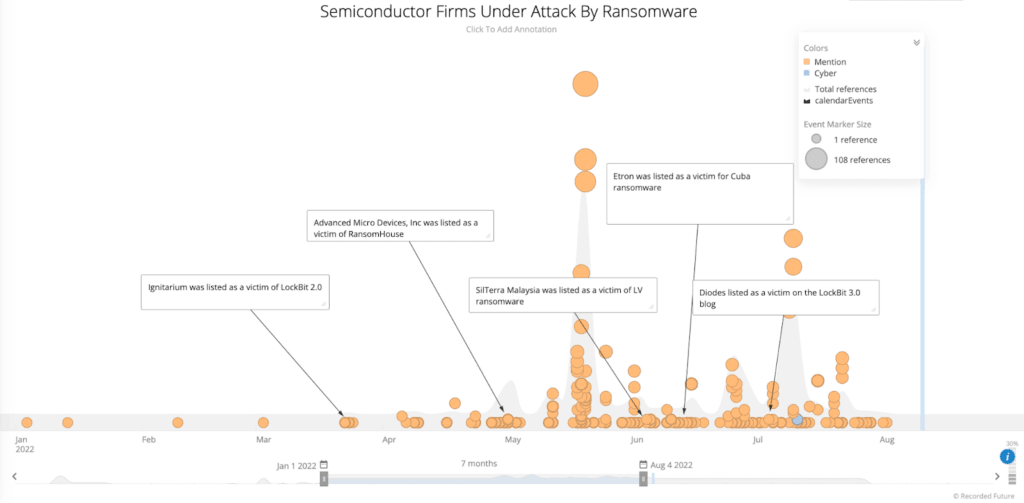
Recorded Future, which owns The Record, released a report on Thursday outlining eight different cyberattacks on semiconductor companies in 2022.
Five of the incidents involved ransomware from the LockBit, Cuba and LV gangs. The other three were done by extortion groups like Lapsus$ and RansomHouse.
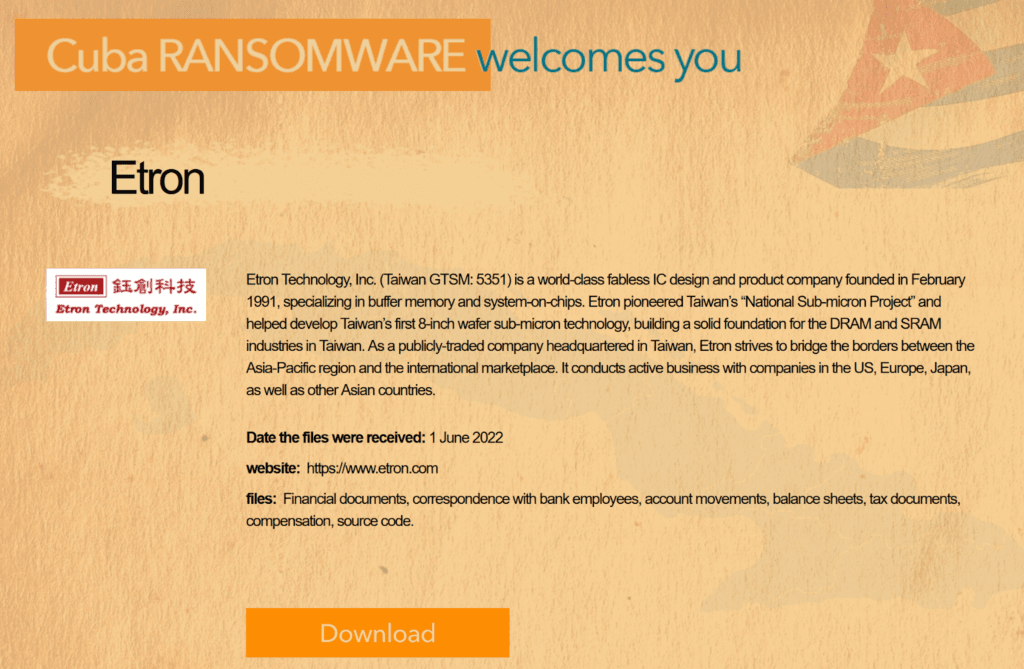
In 2022, Recorded Future researchers tracked attacks on semiconductor giants like NVIDIA, AMD and Samsung as well as others like Ignitarium, Diodes, SilTerra Malaysia Sdn. Bhd., Semikron and Etron Technology.
All of the attacks took place as the scramble for semiconductors became a national security concern for several countries including the United States, which signed a bill last month to invest $52.7 billion in domestic semiconductor manufacturing and science research.
The researchers noted that while none of the cyberattacks on semiconductor companies have “direct connections” to nation-state groups, several companies have found “state-sponsored threat actors masquerading as ransomware groups and using at least 5 ransomware variants — LockFile, AtomSilo, Rook, Night Sky, and Pandora — to conduct cyber espionage.”
The Recorded Future researchers also theorized that while the ransomware attacks on semiconductor companies in 2022 seemed mostly financially motivated, nation state actors “may have already become affiliates with RaaS [ransomware-as-a-service] operators and are using different ransomware families to conduct cyberattacks with the main objective of stealing IP from semiconductor companies.”
The tactic allegedly allows nation-state threat actors to make use of readily available ransomware to encrypt and steal information, and “make the cyberattacks look like attacks from ransomware groups.”
“As the competition for semiconductor supremacy is at the heart of the economic competition between China and Taiwan, we believe it is likely that cyberattacks and industrial espionage against semiconductor companies will continue,” they said, calling semiconductors the “hearts of electronic devices such as smartphones, computers, automobiles, appliances, televisions, and advanced medical diagnostic equipment.”
“Any disruption to the semiconductor sector would likely have an impact across all other manufacturing sectors. We believe that ransomware operators see semiconductor companies as high-value targets and leverage media coverage to apply pressure on the victim organization to negotiate and pay the ransom due to the importance of semiconductors to the global economy.”
Ransomware and extortion
Of the ransomware attacks on semiconductor companies, most involved the use of malware to encrypt data, extortion threats, the publishing of source code and other proprietary data.
Some groups threatened to sell company data and plans to competitors, rival nations and more while others used the code-signing certificates stolen from semiconductor companies to sign malware.
Most of the attacks were done by affiliates of the groups through the ransomware-as-a-service model.
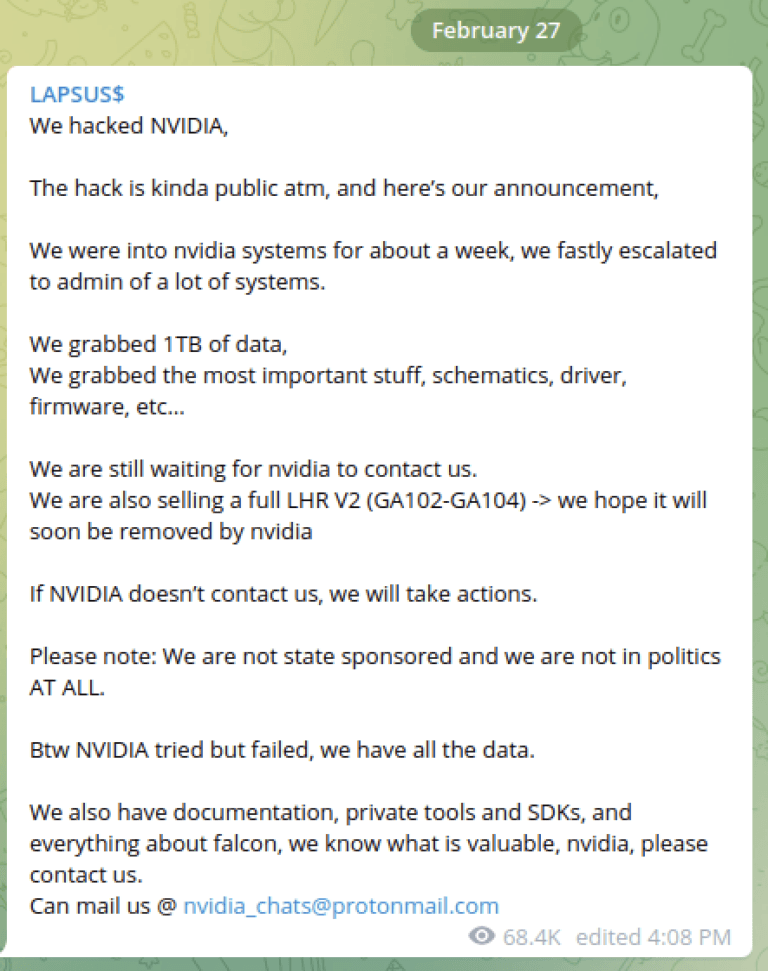
In addition to the ransomware attacks on Ignitarium, Diodes Inc., Etron Technology, SilTerra Malaysia Sdn. Bhd., and Semikron — NVIDIA, AMD and Samsung faced theft of data and extortion from the RansomHouse gang and the notorious Lapsus$ Group.
Lapsus$ made its return to headlines over the last week when Uber attributed an attack to the group.
The report calls for semiconductor companies to be added to the U.S. Cybersecurity and Infrastructure Security Agency’s (CISA) list of 16 critical infrastructure sectors because some ransomware groups have tenuous rules about attacks on certain companies.
“But while the semiconductor industry may not be listed as a critical infrastructure sector as of this writing, with the growing recognition of its strategic importance, as well as the US government’s plan to support domestic chip production, we believe that there is a strong likelihood that the US government may classify semiconductor firms as a critical infrastructure sector in the future, which will serve as a new deterrent to prevent ransomware affiliates from targeting this industry,” the report explained.
Last week, the U.S. House version of the annual National Defense Authorization Act (NDAA) included a proposal that would create a new designation — called “systemically important entities” — requiring operators of the most vital U.S. critical infrastructure to enact strong digital security standards and share threat intelligence with the government in return for increased federal support.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.