Vulnerabilities found affecting OT products from German companies Festo and CODESYS
Three vulnerabilities have been disclosed affecting operational technology (OT) products from two German companies: factory automation manufacturer Festo and automation software company CODESYS.
Researchers from cybersecurity firm Forescout said two of the bugs affect Festo automation controllers and one affects the CODESYS software, which is used by hundreds of device manufacturers in different industrial sectors, including Festo.
These vulnerabilities affect hundreds of industrial devices in the supply chain. The most severe one enables denial of service and is trivially easy to execute – either by visiting a hidden web page by or by using a text-based browser tool.
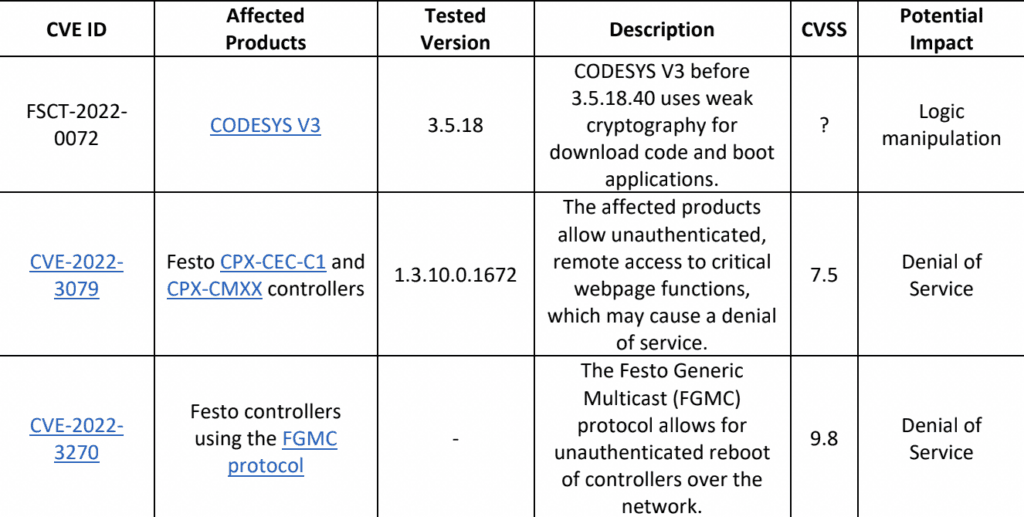
The three vulnerabilities are FSCT-2022-0072 — affecting CODESYS V3 — as well as CVE-2022-3079 and CVE-2022-3270, which affect Festo automation controllers.
Forescout’s Head of Security Research Daniel dos Santos said CODESYS’ CVE-2022-4048 stands out because it shows that even in recent and popular implementations of cryptography in OT systems, there are some basic mistakes.
“The use of insecure pseudo-random number generators, a null initialization vector and the insecure mode of operation ECB are all well-known cryptographic pitfalls that should have been avoided in a product used by many critical OT devices,” he said.

Dos Santos noted that with the help of Festo, they also discovered that known vulnerabilities CVE-2022-31806 and CVE-2022-22515 affected several Festo programmable logic controllers (PLCs) — industrial computers used to control automation — because they shipped with an unsafe configuration of the CODESYS runtime environment.
He suggested IT teams focus on remediating these issues because many other device manufacturers may be integrating CODESYS insecurely in their products and either are not aware of this or have not made their customers aware with a specific security advisory.
The most concerning of the bugs, according to dos Santos, is CVE-2022-3270, which allows for sensitive commands to be run without authentication on some Festo PLCs.
“This once again shows that there are many proprietary OT protocols out there that allow anybody on the network to take control of a PLC.
“In most cases these are legacy protocols designed at a time where security was not a major concern for OT, but they are still used in critical facilities around the world.”
CODESYS has sold more than 8 million device licenses – most to manufacturers of programmable automation components and controllers like Festo. Its automation suite runs on some 1,000 models of more than 500 manufacturers, Forescout says.
These devices are used in industries such as manufacturing, energy automation and building automation.
“Although these devices are typically not supposed to be exposed online, we see almost 3,000 devices running CODESYS when querying the Shodan search engine,” the researchers said.
Festo, meanwhile, is a seller of pneumatic and electrical control systems and drive technology for factories and process automation across 61 countries, with billions in annual sale revenue.
On the Forescout Device Cloud – a repository of data from 19 million devices monitored by Forescout appliances – the researchers saw close to 1,000 Festo controllers, used overwhelmingly within manufacturing.
Forescout disclosed the bugs to the affected companies as well as CERT@VDE, a German security platform for small and medium-sized automation companies.
A spokesperson for Festo provided links to advisories for all of the bugs.
Forescout compared the bugs to more than 56 that were disclosed earlier this year and given the collective name "OT:ICEFALL."
The researchers said that like those disclosures, these new issues “exemplify either an insecure-by-design approach where manufacturers include dangerous functions that can be accessed with no authentication or a subpar implementation of security controls, such as cryptography.”
The main issue Forescout found with CODESYS V3 is that session keys are generated using an insecure pseudo-random number generator (PRNG) working off a small and predictable seed.
According to the researchers, an attacker can “simply brute force the session key to decrypt the downloaded code for manipulation.”
The encryption scheme also uses an insecure mode of operation: Electronic Codebook (ECB) message encryption mode.
“The code is encrypted in ECB mode without additional cryptographic authentication and integrity over the ciphertext as a whole. This means that both confidentiality and integrity are compromised regardless of session key strength,” the researchers said.
“The impact is that an attacker can trivially decrypt and manipulate protected code.”
The other issues concerned several ways to reboot Festo programmable logic controllers (PLCs) without authentication.
Any one of these methods would allow an attacker with network access to target the device and cause a denial of service condition.
An attacker could also use the reboot command in the PLC Browser tool — a text-based monitor for controllers running CODESYS — which allows an operator to issue several commands to the monitored controllers.
Tobias Pfeiffer, head of Festo's Product Security Incident Response Team, told The Record that CVE-2022-3079 only concerned the CPX-CEC-C1 and CPX-CMXX products, with the latter being phased out after discontinuation in 2015. Pfeiffer noted that there are replacements available for CPX-CEC-C1.
Forescout said protection against these vulnerabilities requires patching devices running the vulnerable firmware (FSCT-2022-0072), replacing them with newer equipment (CVE-2022-3079) or changing default configurations (CVE-2022-31806 and CVE-2022-22515).
The researchers also suggested firms create an inventory of vulnerable devices and enforce segmentation controls, isolating tools that cannot be patched immediately.
According to dos Santos, the problems may extend beyond what Forescout found on Shodan.
“Just like Festo has FGMC and other vendors have other insecure engineering protocols that we reported on the original OT:ICEFALL disclosure, there certainly are many other instances of this that are not yet public knowledge,” he said.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



