Siemens, Motorola, Honeywell and more affected by 56 ‘ICEFALL’ vulnerabilities
Security researchers have discovered 56 new vulnerabilities – collectively known as “ICEFALL” – that affect several of the largest operational technology (OT) equipment manufacturers supplying critical infrastructure organizations.
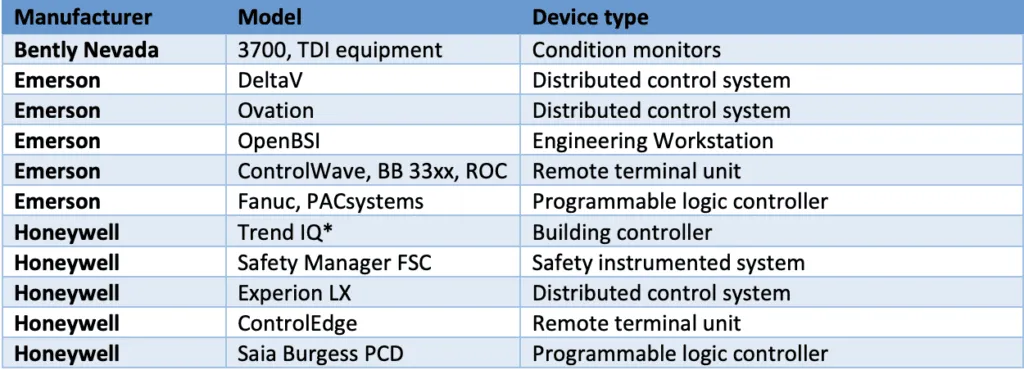
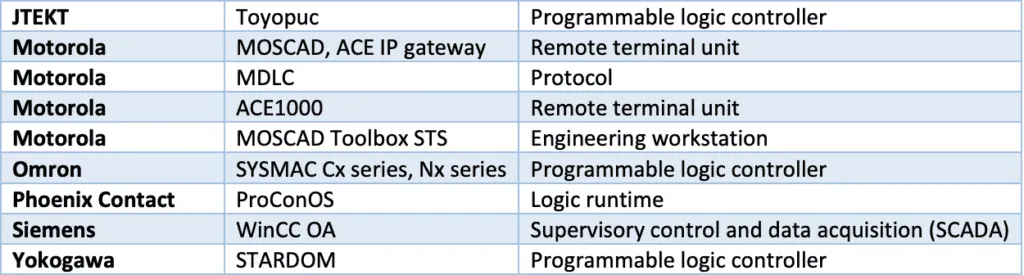
The vulnerabilities affect Siemens, Motorola, Honeywell, Yokogawa, ProConOS, Emerson, Phoenix Contract, Bentley Nevada, Omron and JTEKT. Discovered by researchers with Forescout, the 56 vulnerabilities were disclosed in coordination with the U.S. Cybersecurity and Infrastructure Security Agency (CISA) and other government agencies around the world.
The vulnerabilities are broken down into four general categories: Insecure engineering protocols, weak cryptography or broken authentication schemes, insecure firmware updates and remote code execution via native functionality.
Daniel dos Santos, head of security research at Forescout, told The Record that the most concerning CVEs were those related to insecure engineering protocols because they are “prime examples of lack of security controls.”
“The ones allowing for remote code execution are very concerning because they allow for stealthier attacks (for instance changing process variables without alerting the operator) and for attackers to obtain persistence on a device,” dos Santos said.
Nearly 40% of the vulnerabilities allow for the compromise of credentials and 21% involve firmware manipulation.
He added that the report highlighted the larger issue within the industrial control system (ICS) industry of tools that are insecure by design. Forescout said in its report that vulnerabilities like the ones within ICEFALL are often “brushed off as a particular vendor or asset owner being at fault.”
By putting all 56 vulnerabilities in the same batch together, the company’s goal “is to illustrate how the opaque and proprietary nature of these systems, the suboptimal vulnerability management surrounding them and the often-false sense of security offered by certifications significantly complicate OT risk management efforts.”
He noted that right now, the kinds of vulnerabilities described in the report are typically exploited by nation-states, and dos Santos highlighted malware like Industroyer, TRITON, Industroyer2 and INCONTROLLER that are designed specifically to attack OT systems.
“But there have been past examples of ransomware gangs, such as EKANS, targeting ICS processes as well as other attackers tampering with critical processes, such as in the Oldsmar water treatment attack,” he explained. “As it becomes easier for adversaries less sophisticated than state-sponsored ones to exploit these vulnerabilities, the number and variety of attacks may increase.”
dos Santos and his team were also alarmed by the fact that 74% of the product families affected by OT:ICEFALL have some form of security certification, highlighting the “limited scope for evaluations, opaque security definitions and focus on functional testing.”
Many of the devices have been certified with OT security standards such as IEC 62443.
The report also exposed that the OT/ICS industry is rife with device vulnerabilities that are not disseminated to every manufacturer, leaving many security teams in the dark about issues in their supply chain.
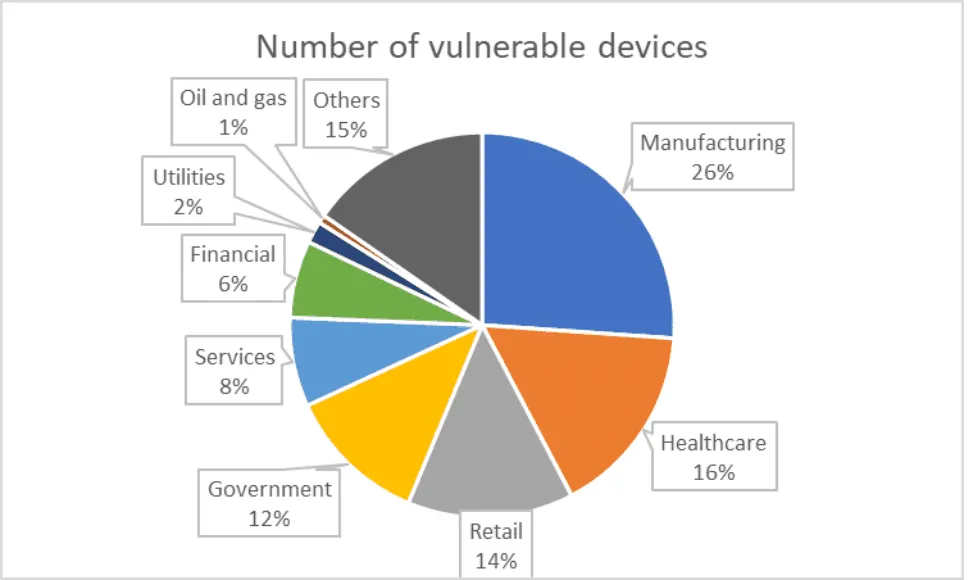
The majority of devices mentioned in the report are used within the manufacturing industry, but several of the vulnerabilities affect devices used widely in healthcare and government. Forescout said these kinds of organizations are most common because of the presence of building automation controllers.
According to dos Santos, the products affected by OT:ICEFALL are also known to be prevalent in industries such as oil and gas, chemical, nuclear, power generation and distribution, water treatment and distribution, mining, and building automation.
Through a search on Shodan, the researchers found more than 5,000 of the vulnerable devices exposed online, with most being Saia Burgess and OMRON controllers or devices running the ProConOS runtime.
Of the 18 million devices Forescout monitors through its Forescout Device Cloud service, nearly 30,000 were vulnerable to the Icefall CVEs.
Manufacturers need to be open about insecure-by-design vulnerabilities, move to product lines that implement security controls, help asset owners with this transition and more generally, need to stop thinking that it's ok for OT devices to be insecure because they are isolated, according to dos Santos.
“As many past incidents have shown, there are ways for adversaries to reach these devices on a target network and exploit insecure by design functionality,” he said.
Ron Fabela, CTO of security company SynSaber, told The Record that the project laid bare the problems OT and ICS systems have with hardcoded passwords and lack of authentication.
But he questioned how the report would be received among security officials who are already “over taxed with compliance, breach reporting, and ‘threat actor of the month’ FUD.”
“Like Project Basecamp, OT ICEFALL focuses on the low hanging exploitation fruit of ICS, where exploitation isn't really necessary at all in most cases. Simply sending the correct command, knowing how to run strings against firmware, or often times just reading the manual will yield the necessary information for attacking these systems,” he said.
“But the community needs to ask the question: does generating CVEs for engineering decisions move the ball forward in securing ICS? While the work of researchers is beneficial from an awareness stance, asset owners are left with more ‘vulnerabilities’ that are most likely un-patchable during their operational period.”
Claroty vice president of research Amir Preminger added that it will be interesting to see how the vendors responded to the report.
Preminger said when Claroty’s team notifies a vendor about a vulnerability, their goal is to give users a patch or at least a proper mitigation, which is better than just segmenting the OT protocols behind a firewall.
“These kinds of reports show the magnitude of the challenges that OT asset owners are coping with and the technical debt that vendors need to bridge to make OT networks more secure,” Preminger said.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.

