Ransomware incidents hit 117 countries in 2023, task force says
More than 6,500 ransomware attacks were recorded in 2023, touching a record number of 117 countries across the globe after a brief dip in 2022.
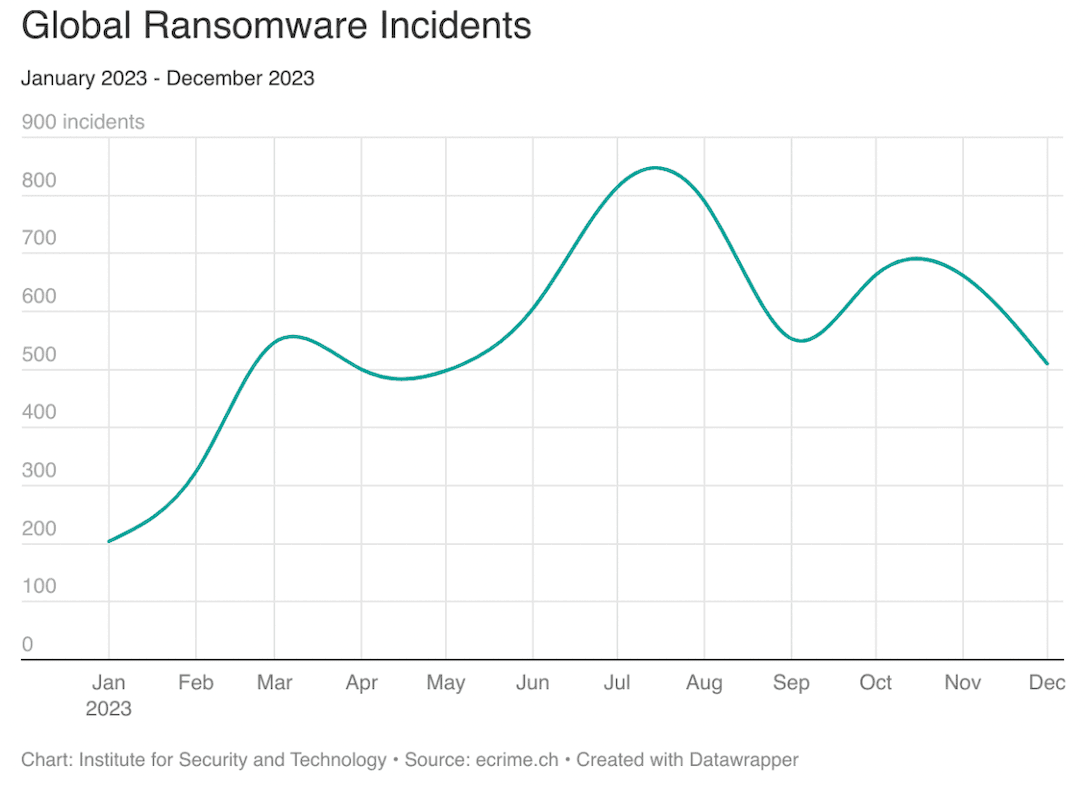
There was a 73% year-over-year increase in attacks to 6,670 ransomware incidents, with notable spikes in June and July due to the exploitation of a popular file transfer tool.
The numbers were compiled by the Ransomware Task Force, which was organized in 2021 by the nonprofit Institute for Security and Technology and is a public/private consortium made up of cybersecurity experts, government officials and more.
In its annual report covering 2023, the organization used data from eCrime.ch, which aggregates messages posted on data leak sites as its primary source of information.
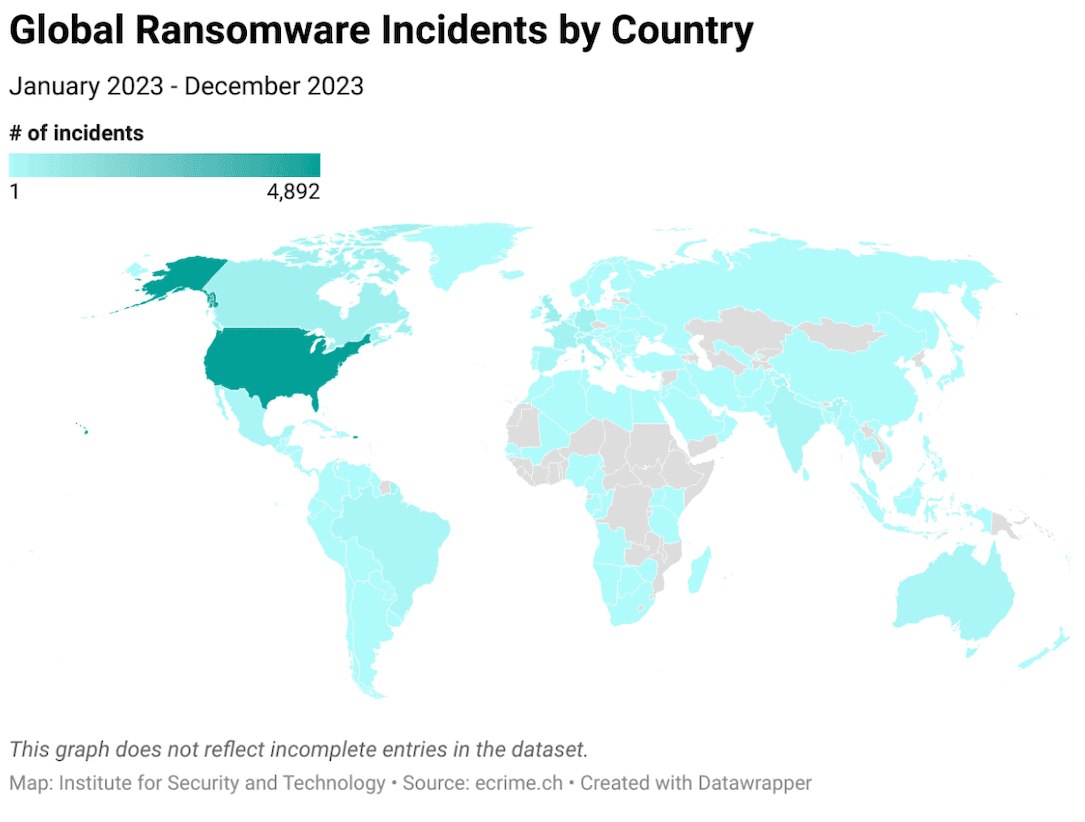
The task force found at least 117 countries experienced ransomware incidents launched by 66 different groups. For 2022, the numbers were slightly lower at 105 countries and 58 ransomware gangs.
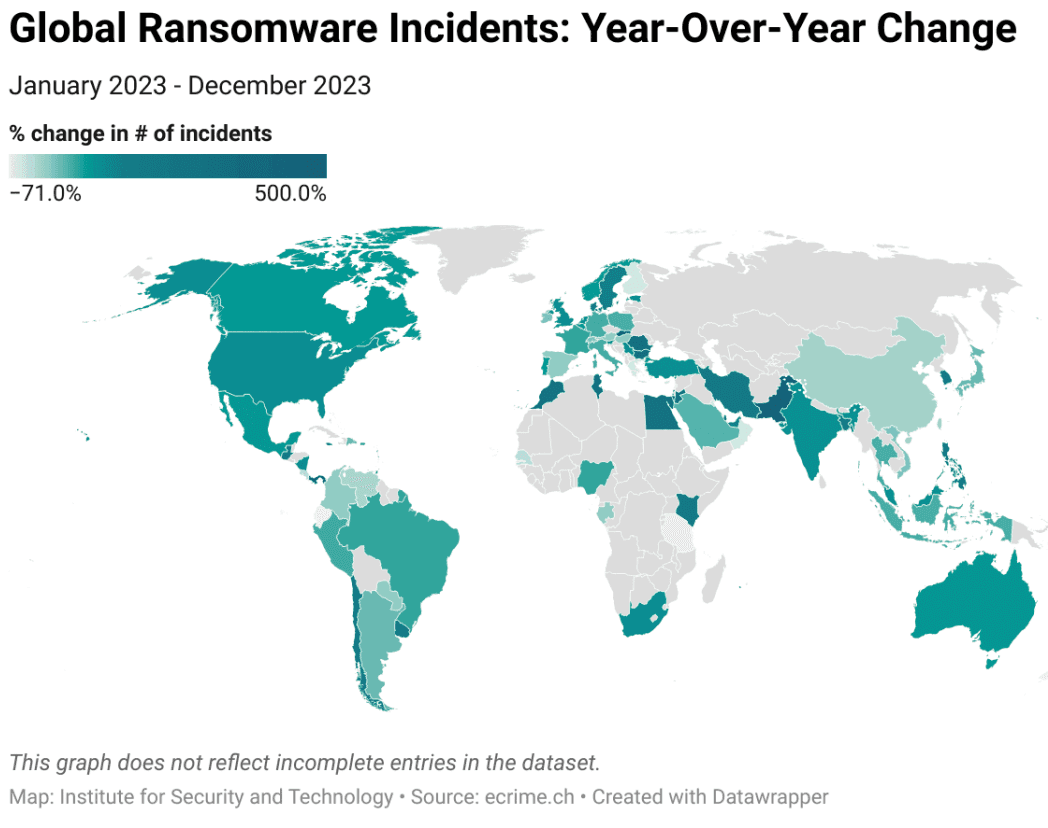
The data for 2023 showed increases in ransomware activity across South Asia and South America — two regions that are rapidly digitizing. Iran, Pakistan, Brazil and India saw the greatest increases, with Brazil facing attacks on its presidential office and India seeing incidents affecting its hospitals and financial systems.
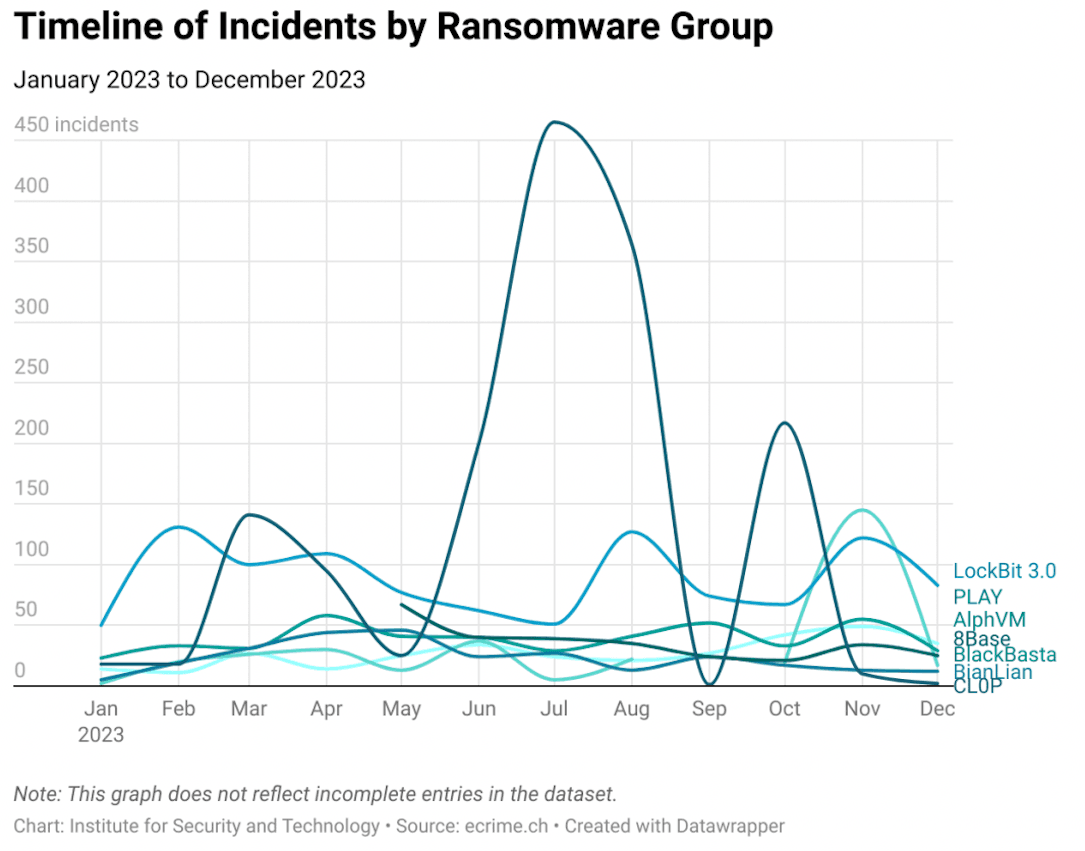
LockBit and AlphV, two ransomware-as-a-service groups taken down by law enforcement this year, led the way in most regions with the highest numbers of attacks. Gangs made a point of targeting the construction industry as well as healthcare and IT.
While some experts believe ransomware gangs often lie about some victims they post on leak sites, eCrime.ch’s numbers track with other assessments from the FBI and blockchain research company Chainalysis. Both have released reports illustrating that 2023 was a record year in terms of ransomware complaints and earnings accrued from the attacks.
The Ransomware Task Force lamented the evidence showing that the “scale, frequency, and complexity of incidents continue to increase as cybercriminals refine the RaaS model.”
“The fundamental criminal effectiveness of the RaaS model has not changed, and these crimes continue to grow more profitable over time. Additional efforts must be taken in 2024 and beyond to disrupt this model,” the group said.
The report said that half of the recommendations the task force made in a report on ransomware in 2021 are still not fulfilled. While progress has been made with incident reporting structures and global collaborations, little has been done to address the continued flow of ransom payments. Law enforcement agencies encourage ransomware victims not to make payments if possible.
The Ransomware Task Force said in April that while some of the recommendations would require legislative action, many of the efforts around better preparing organizations for attacks and providing financial support for those affected is still insufficient.
“Governments have not taken all necessary further actions to combat ransomware,” the report said.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



