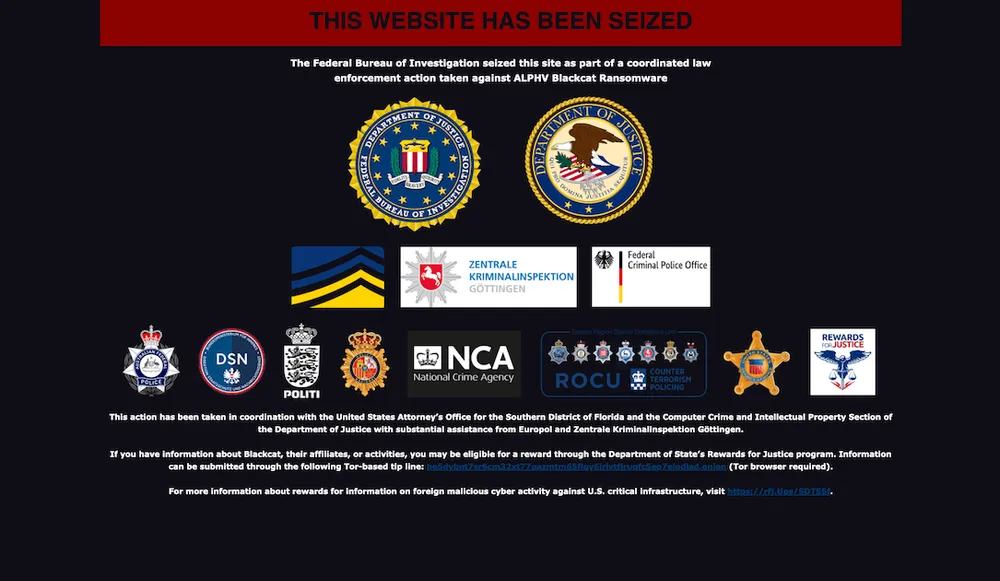
FBI posts takedown notice on AlphV ransomware group’s website
The darknet website of the AlphV/Blackcat ransomware gang was replaced by a splashpage on Tuesday announcing it had been seized by the FBI.
Following the seizure the Department of Justice released a statement about its “disruption campaign” targeting the gang and unsealed a search warrant revealing how a confidential source had helped it access more than 900 public/private key pairs controlling AlphV’s darknet website infrastructure.
The Cybersecurity and Infrastructure Security Agency (CISA) said that as of September 2023, the group’s affiliates “have compromised over 1,000 entities — nearly 75 percent of which are in the United States and approximately 250 outside the United States — demanded over $500 million, and received nearly $300 million in ransom payments.”
The takedown follows more than a week of speculation regarding potential law enforcement action after the criminals’ site became inaccessible earlier this month. Although the site subsequently came back online, it was stripped of all references to victims that the criminals had published as part of their extortion efforts.
Read More: FBI warrant reveals ‘confidential source’ helped AlphV/Blackcat ransomware takedown
The ransomware group is notorious for the scale and impact of its attacks. Inthe past two months alone, victims have included the healthcare manufacturer Henry Schein, Fidelity National Financial, and the Japanese watchmaker Seiko.
In an unusual incident in November, the gang also reported one of its victims to the U.S. Securities and Exchange Commission in a bid to increase the pressure on financial software company MeridianLink to make an extortion payment.
The seizure notice states: “The Federal Bureau of Investigation seized this site as part of a coordinated law enforcement action taken against ALPHV Blackcat Ransomware.”
Logos included on the notice credit the involvement of around a dozen agencies, including the U.S. Department for Justice, the U.S. Secret Service, Europol, and the German Federal Criminal Police Office. It particularly credits Europol and the Zentrale Kriminalinspektion Göttingen as having provided “substantial assistance.”
The national police forces of Australia, Spain and Estonia are also featured on the splash page, as is Austria’s Directorate of State Security and Intelligence, and the United Kingdom’s National Crime Agency and the Eastern Region Special Operations Unit of Britain’s regional organized crime units.
Also included on the splashpage was the logo of the U.S. Rewards for Justice Program, which offers to pay individuals who provide information to the U.S. that helps protect the country’s national security. It appears to be the first time the program’s logo has been featured on such a splashpage — although the program is regularly cited by law enforcement tackling ransomware gangs.
The program has for some time listed several Russian military intelligence officers among its targets, and recently celebrated the takedown against the Hive ransomware group by tweeting it was prepared to pay up to $10 million for information about it and similar organizations — although the program logo was not included on the splashpage that replaced the Hive gang’s website.
Earlier this year, the Russian telecommunications regulator Roskomnadzor blocked access to the Rewards for Justice website, alongside the sites for the CIA and the FBI.
Malware, social engineering, and more
The group has released a new version of the malware that was better at evading defense systems and was able to encrypt both Windows and Linux devices, according to the FBI and CISA advisory. The hackers also do their homework, too, the agencies said.
“ALPHV Blackcat affiliates use advanced social engineering techniques and open source research on a company to gain initial access. Actors pose as company IT and/or helpdesk staff and use phone calls or SMS messages to obtain credentials from employees to access the target network,” the FBI and CISA said. “ALPHV Blackcat affiliates use uniform resource locators (URLs) to live-chat with victims to convey demands and initiate processes to restore the victims’ encrypted files.”
Some affiliates of the group exfiltrate data and extort victims without ever deploying ransomware — at times deleting data from victims’ systems to incentivize payment.
The group often offers alleged “cyber remediation advice” or “vulnerability reports” explaining how they gained access to a victim’s systems, the advisory said.
Jonathan Greig contributed to this story.
Editor's note: Story updated 2 p.m. ET with information from the FBI and CISA advisory.
Alexander Martin
is the UK Editor for Recorded Future News. He was previously a technology reporter for Sky News and a fellow at the European Cyber Conflict Research Initiative, now Virtual Routes. He can be reached securely using Signal on: AlexanderMartin.79