QNAP warns of new bug prompting worries of potential Deadbolt ransomware exploitation
Data-storage hardware vendor QNAP is warning customers to update their devices after the discovery of a vulnerability that exposes thousands to attacks.
The company published an advisory this week about the bug — CVE-2022-27596 — which affects QNAP devices running proprietary QTS 5.0.1 and QuTS hero h5.0.1 software. The company has given the bug a CVSS score of 9.8 out of 10.
“The vulnerability is not actively exploited now,” a spokesperson for QNAP told The Record.
Still, there is one big reason for QNAP hardware users to be highly vigilant: Thousands have been terrorized for more than a year by the Deadbolt ransomware gang, which has specifically targeted QNAP customers.
The bug was discovered by a third-party researcher and reported through the company's Security Bounty Program, the spokesperson said.
Patch now: CVSS 9.8 (Critical) SQLi in QNAP NAS, likely to be exploited by threat actors such as the operators of Deadbolt Ransomware as well as RaspberryRobinhttps://t.co/OIr26KUrCa
— Will (@BushidoToken) February 1, 2023
Scans report by @censysio https://t.co/FcZ0kVLydl
Several researchers, including some from security company Censys, expressed concern that QNAP has deemed the issue “a critical vulnerability with a low attack complexity, no authentication required, and it can be exploited remotely.”
“Censys has observed 67,415 hosts with indications of running a QNAP-based system; unfortunately, we could only obtain the version number from 30,520 hosts. But, if the advisory is correct, over 98% of identified QNAP devices would be vulnerable to this attack,” Censys senior security researcher Mark Ellzey said.
“We found that of the 30,520 hosts with a version, only 557 were running QuTS Hero greater than or equal to ‘h5.0.1.2248’ or QTS greater than or equal to ‘5.0.1.2234,’ meaning 29,968 hosts could be affected by this vulnerability.”
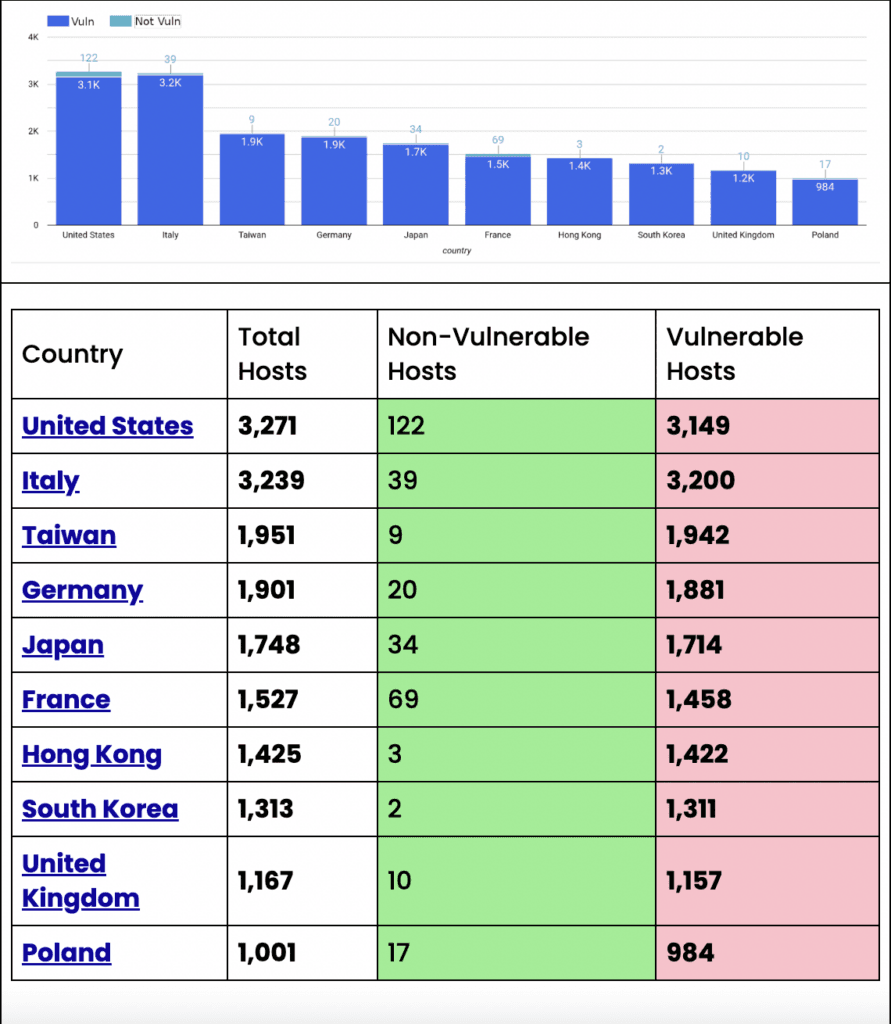
The country with the most vulnerable hosts was the United States, which had more than 3,200. Italy, Taiwan, Germany and Japan were not far behind.
Mark Ellzey, senior security researcher at Censys, told The Record on Friday that the number of vulnerable devices moved up to 31,567.
"There is good reason for this; most of these devices live on residential networks (a residential network is an ISP that people use in their homes, (FIOS, Comcast, etc)," he said.
"For example, HINET Data Communications provides broadband services to small businesses and local residents. HINET saw 322 new QNAP devices come online. Networks like these are the networks of normal everyday people, not high-availability server farms, so you're going to see an ebb and flow of listening services as people log in and log out of their internet."
Deadbolt activity
Censys data shows that the Deadbolt group has infected more than 20,000 devices and collected about $200,000 from victims — many of whom use QNAP network-attached storage (NAS) devices to store treasured family photos, wedding videos and other personal files. The company also created a dashboard to track the number of victims around the world.
Since January, thousands of QNAP customers using the company’s NAS devices have reported being attacked by the DeadBolt ransomware group, which demands a ransom of 0.03 Bitcoin ($1,100) for the decryption key.
After the initial attacks affected about 3,600 devices in January 2022, the group continued to resurface with campaigns in March, May and June this year. Reddit and other message boards have been flooded with customers lamenting the loss of files that included family photo albums, wedding videos and more. Dozens of users took to Reddit to complain that they were among those attacked in the most recent campaign.
In a note to QNAP, the hackers demanded 5 Bitcoin ($93,900) to reveal details about the alleged zero-day vulnerabilities they initially used to attack its users and another 50 Bitcoin ($939,000) to release a master decryption key that would unlock all of the victims’ files.
I just got hacked. Ransomware named DeadBolt found an exploit in @QNAP_nas storage devices, encrypting all files. They ask $1,000 from individuals or $1.8 million from QNAP. I have 50tb of data there, none of it essential or sensitive, but it hurts a lot. Time for a fresh start. pic.twitter.com/E8ZkyIbdfp
— Lex Fridman (@lexfridman) January 27, 2022
Security company Emsisoft released its own version of a DeadBolt decryptor after several victims reported having issues with the one they received in exchange for paying a ransom.
However, it only works with a decryption key supplied by the operators of the DeadBolt ransomware through a ransom payment.QNAP has previously warned of different ransomware strains being used to target their users, including the Checkmate ransomware and the ech0raix ransomware.
"There is no indication of Deadbolt infections so far -- but given that the group was targeting QNAP devices before, there is a decent chance they are working on finding this vulnerability now," Ellzey said.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



