QNAP investigating new Deadbolt ransomware campaign
Taiwanese hardware vendor QNAP said on Friday that it is investigating yet another Deadbolt ransomware campaign targeting users of its network-attached storage (NAS) devices.
The company did not respond to requests for comment but released an advisory saying it recently detected a new batch of DeadBolt ransomware victims.
“According to victim reports so far, the campaign appears to target QNAP NAS devices running outdated versions of QTS 4.x. We are thoroughly investigating the case and will provide further information as soon as possible,” the company said.
QNAP urged customers to update their QTS or QuTS hero systems to the latest version as soon as possible.
For those who have already been compromised, QNAP said they should take a screenshot of the ransom note – in order to keep the Bitcoin address – then “upgrade to the latest firmware version.”
“The built-in Malware Remover application will automatically quarantine the ransom note which hijacks the login page,” QNAP explained.
“If you want to input a received decryption key and are unable to locate the ransom note after upgrading the firmware, please contact QNAP Support for assistance.”
Almost exactly one month ago, QNAP released a similar warning after several customers reported Deadbolt ransomware infections.
It is unclear where members of the Deadbolt ransomware group are based but it emerged in January and began attacking thousands of NAS devices around the world.
In January, dozens of people turned to QNAP message boards and Reddit to say they logged on only to find the Deadbolt ransomware screen. People reported losing decades of photos, videos and irreplaceable files.
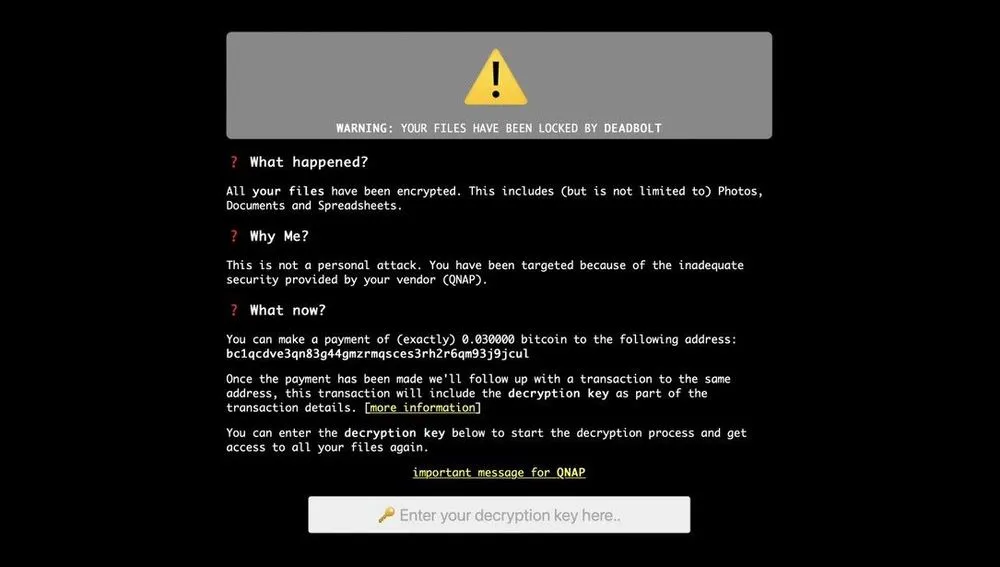
The ransom note most victims see demands 0.03 Bitcoin for the decryption key and says, “You have been targeted because of the inadequate security provided by your vendor (QNAP).” At least one user on Reddit reported paying the ransom and not getting the decryption key.
The group also sent out a message directly to QNAP in January claiming all affected customers were “targeted using a zero-day vulnerability.”
“We offer you two options to mitigate this (and future) damage,” the group said, demanding a payment of 5 Bitcoin in exchange for details about the alleged zero-day used to launch the attack, or 50 Bitcoin for a universal decryption master key and information about the zero-day.
“There is no way to contact us. These are our only offers,” the January message reportedly said.
There continues to be significant debate among QNAP NAS users about whether even updated versions of the system are still vulnerable to the ransomware. QNAP has insisted that the ransomware group is only targeting unpatched systems.
A QNAP user, who asked to be identified only as "Seth D" out of fear of reprisal from Deadbolt or QNAP, contacted The Record on Saturday to say he logged into his QNAP NAS on Friday morning and discovered the Deadbolt splash screen.

"I worked on trying to recover my files all day, but it’s mostly hopeless," he said in an email interview.
He also disputed QNAP's insistence that Deadbolt was targeting users who had not updated their devices to the latest version.
"According to my device, I’m running the latest firmware too, so whatever this 'day zero' vulnerability the Deadbolt jerks are referencing, QNAP hasn’t done a thing to fix it," he said.
"I literally tried updating my firmware once I got back into my NAS and past the Deadbolt splash screen, (within 10-20 minutes after some googling), and my NAS told me I was using the most recent firmware. Plus Deadbolt themselves have stated this is a day zero vulnerability that QNAP hasn’t addressed. At this point I’m more apt to believe the hackers over a company that can’t do the one job it’s products are designed to do."
He said he tried to look for ways to contact QNAP for help but called their support systems "atrocious and not customer friendly…like they don’t really want people contacting them."
He now cannot access the files he backed up and criticized QNAP for blaming the Deadbolt issue on users who did not update their systems.
He suggested QNAP pay the ransom and get the master key from the Deadbolt operators or cover the cost for each individual affected user to get their keys.
Nearly 5,000 affected devices
Security company Censys reported that of the total 130,000 QNAP NAS devices sold, 4,988 services “exhibited the telltale signs of this specific piece of ransomware.”
Lookout’s Hank Schless said NAS devices are tools connected to a network that allow for the storage and retrieval of data from a centralized location for authorized users and others.
Organizations use NAS to bring the benefits of cloud infrastructure inside their network, and now with people working from anywhere, these systems are web-facing to ensure employees have access to the data they need regardless of location, Schless explained.
“While this enables productivity, it can introduce serious risk if not done correctly. Not only could attackers compromise the data within the particular resources they discover, but they could also move laterally around your network after initial compromise,” he added.
In May, Censys managed to track the Bitcoin wallet transactions associated with an infection and figured out that of the previous batch of victims, 132 paid ransoms totaling about $188,000. The company also created a dashboard to track the number of victims around the world.
Most of the recent infections are taking place in the United States, Germany and the United Kingdom.
After a brief respite following the January attacks, Censys said more than 1,000 QNAP devices were infected with the Deadbolt ransomware in March.

Theon Technology CEO Scott Bledsoe noted that any NAS device is a big target for ransomware since it is used to store a significant amount of business critical data.
"Given the large number of QNAP NAS devices that are currently deployed, the Deadbolt ransomware can be used to target a wide variety of organizations for profit by the attackers," he said.
Security company Emsisoft released its own version of a decryptor after several victims reported having issues with the one they received after paying a ransom. Some users even said they never got a decryptor after paying the ransom, while others said the decryptor malfunctioned.
Emsisoft’s decryptor requires users to have already paid the ransom and received the decryption keys from the Deadbolt ransomware operators.
Bud Broomhead, CEO at IoT security company Viakoo, said QNAP drives are often managed outside of IT departments and have become targets for cybercriminals. Many NAS instances are not protected by firewalls and are left unpatched.
“QNAP devices are very attractive to cybercriminals whose strategy is to ask a large number of victims for a small amount of money (as opposed to few victims being asked for large amounts),” Broomhead said.
“The ~$900 asked for as ransom is at a level where many operators of the devices will choose to pay rather than get their IT or security teams involved (and potentially face internal consequences for not having properly onboarded and secured the devices).”
Other experts, like Vectra CTO Oliver Tavakoli, urged NAS users to not expose their devices to the internet because they are not designed to withstand a capable adversary.
Other companies’ devices also have been attacked. Users of Asustor’s NAS hardware were also warned in February of potential Deadbolt ransomware infections after dozens of people took to Reddit and other message boards to complain of attacks.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.