Microsoft warns of a 32% surge in identity hacks, mainly driven by stolen passwords
Hackers are increasingly using stolen identities to breach organizations, impersonating employees or contractors before stealing data and launching ransomware, according to new research.
Microsoft’s 85-page Digital Defense Report 2025 covers dozens of pertinent cybersecurity issues including ransomware, nation-state attacks, AI and more. But the company’s researchers said the one statistic that stood out more than most others was the continued success of password attacks that allowed hackers to take over victim accounts.
Despite a growing sophistication of cyber threats, “more than 97% of identity attacks are password attacks. In the first half of 2025 alone, identity based attacks surged by 32%,” said Amy Hogan-Burney, a corporate vice president at Microsoft.
“That means the vast majority of malicious sign-in attempts an organization might receive are via large-scale password guessing attempts. Attackers get usernames and passwords (‘credentials’) for these bulk attacks by and large from credential leaks.”
Hackers are also increasingly turning to other methods to obtain credentials. Microsoft tracked surges in the use of infostealer malware by criminals and an increase of IT scams where cybercriminals call a company’s help desk and simply ask for password resets. The scheme has drawn headlines in recent months due to a string of high-profile attacks launched by English-speaking cybercriminals connected to the Scattered Spider organization.
Infostealers allow cybercriminals to quietly gather credentials and information at scale before either using it themselves or selling the data on cybercrime forums. Microsoft noted its role in taking down Lumma Stealer — one of the most prevalent infostealer observed in the last year.
Microsoft said since the takedown, it has continued to “identify and dismantle new Lumma Stealer infrastructure.” Microsoft said it is still unclear whether the takedown will be effective but pointed to its work disrupting cracked versions of Cobalt Strike as evidence that these methods do have an impact.
Microsoft’s report tracks trends from July 2024 through June 2025. The most targeted entities were IT companies and government bodies at the national and local level.
In addition to identity-based attacks, Microsoft also said it saw several key vulnerabilities exploited — including CVE-2024-50623 which impacted popular file sharing tool Cleo and other bugs affecting prominent tools made by Fortinet, BeyondTrust and SimpleHelp.
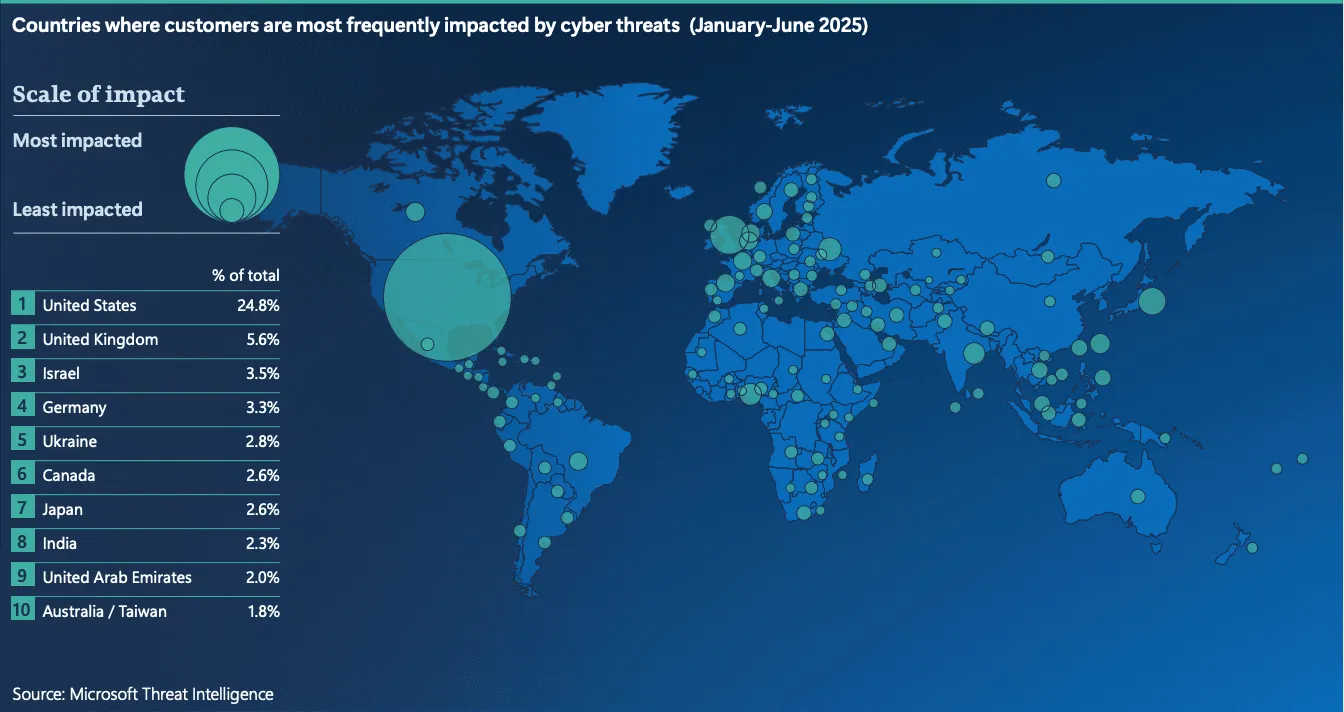
Image: Microsoft
Ransomware affiliate shell games
Microsoft incident responders said 19% of cases where they were able to determine a threat actor’s objectives involved ransomware.
Microsoft cited figures from cybersecurity firm Intel 471 that found 120 ransomware variants were used against 71 industries over the last year, with more than half of all victims based in the U.S.
Nearly half of all alleged victims seen on ransomware leak sites had an annual revenue of $50 million or less. Ransomware actors increasingly leveraged social engineering to obtain or reset credentials, particularly through vishing or tech support scams.
“For example, this year multiple actors conducted help desk-themed social engineering, using messaging platforms such as Teams to communicate with targets and the Windows utility Quick Assist for remote access,” the company’s researchers said.
Microsoft noted that it now tracks specific threat actors because many use multiple strains of ransomware. A cybercriminal known as Octo Tempest used Dragon Force, RansomHub and Qilin ransomware strains throughout the year, illustrating how simple it is for hackers to move between ransomware-as-a-service affiliation.
In a separate notice on social media, Microsoft spotlighted a recent disruption of a threat actor that bounced between using Vice Society, Rhysida, BlackCat, Quantum Locker and Zeppelin ransomware strains.
Another new trend spotted by Microsoft was the exploitation of antivirus (AV) exclusions to avoid detection. AV exclusions are typically used by IT or security teams to stop AV software from wasting resources scanning trusted files or directories, the researchers explained.
“Attackers seek out misconfigurations such as overly broad exclusions, which they could use to disable or sidestep defenses during hands-on-keyboard intrusions,” Microsoft said.
“This year, attackers used exclusions to bypass AV defenses in 30% of observed human-operated ransomware incidents. Despite these evolving threats, attacks reaching the encryption stage have slowed and are now increasing at a rate of only 7% in 2024-2025 compared to 102% in 2023-2024, per our incident tracking.”
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



