Lumma infostealer’s infrastructure seized during US, EU, Microsoft operation
Law enforcement agencies and cybersecurity firms coordinated a global takedown of the infrastructure of the Lumma malware — a powerful information-stealing tool used by cybercriminals to target dozens of industries.
Steven Masada, assistant general counsel at Microsoft’s Digital Crimes Unit, said in a blog post Wednesday that the malware, sometimes referred to as LummaC2, “steals passwords, credit cards, bank accounts, and cryptocurrency wallets and has enabled criminals to hold schools for ransom, empty bank accounts, and disrupt critical services.”
In a briefing with reporters on Wednesday, FBI officials said they have been investigating Lumma since September 2023 and have since found around 10 million infections. The FBI has tracked thousands of paying Lumma customers, with $250, $500 and $1,000 monthly subscription tiers available.
“Access to Lumma via a user panel makes it incredibly easy for those with very little technical knowledge to become a player in the malware game,” said FBI senior official Brett Leatherman.
“The FBI is estimating losses from credit card theft alone, facilitated to the malware platform as $36.5 million in just 2023.”
Microsoft said it identified more than 394,000 Windows computers infected with Lumma malware between March and May this year. The company worked with Europol, the U.S. and Japan on an operation disrupting Lumma’s technical infrastructure, effectively cutting off communications between the malicious tool and victims.
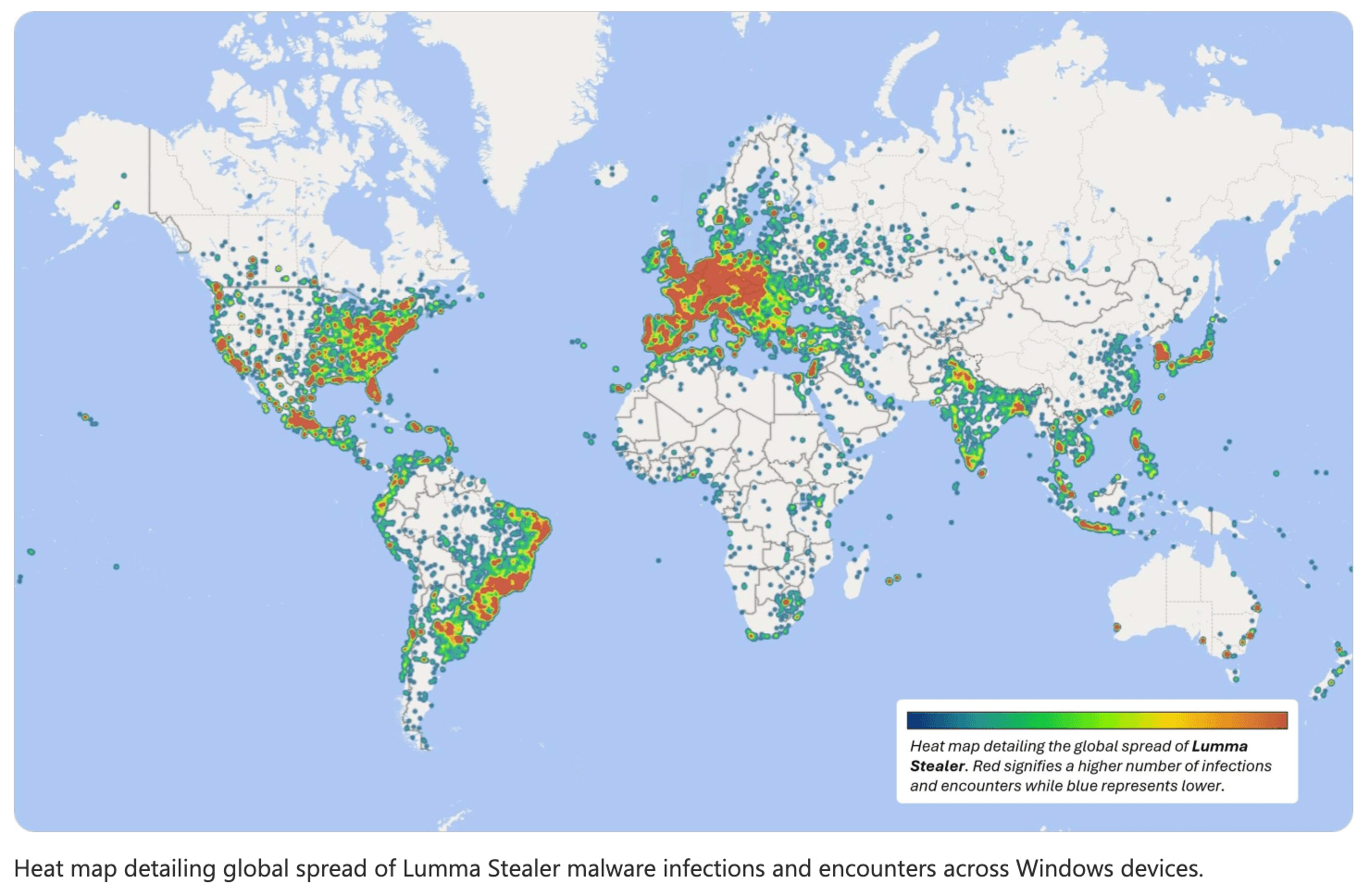
Source: Microsoft
A court order allowed Microsoft to take down, suspend, and block off approximately 2,300 malicious domains that formed the backbone of Lumma’s infrastructure. Masada said the operation allowed them to sever communications between affected devices and the malware infrastructure.
The U.S. Justice Department unsealed two warrants authorizing the seizure of five domains used by Lumma operators. Microsoft worked with Japan’s Cybercrime Control Center and Europol to suspend Lumma infrastructure based in Japan and Europe.
Officials said the U.S. government initially seized two Lumma domains on Monday but the malware’s administrators informed their users of three new domains they had set up, which the DOJ then took down on Tuesday.
“Malware like LummaC2 is deployed to steal sensitive information such as user login credentials from millions of victims in order to facilitate a host of crimes, including fraudulent bank transfers and cryptocurrency theft,” said Matthew Galeotti, head of the U.S. Justice Department’s Criminal Division.
The seized websites were used by administrators to distribute Lumma to their affiliates and other cybercriminals, according to the DOJ. The tool was used to steal browser information, login credentials for emails and banking services, cryptocurrency information and more. The FBI has identified at least 1.7 million instances where Lumma was used to steal this type of information, according to court filings.
Leatherman noted that the U.S. State Department assisted in the operation through its $10 million reward program for information on foreign malicious cyber activity. He did not elaborate on what kind of information came through that channel or how reward might have been paid.
‘Easy to distribute’
Lumma is considered one of the world’s most widely used infostealers, allowing cybercriminals to steal large tranches of sensitive data from infected devices. The malware has been sold on underground forums since at least 2022 and was developed by a Russia-based cybercriminal known as “Shamel.”
Lumma is marketed on Telegram as a service with different tiers, offering cybercriminals the ability to tailor it to their needs. Masada said Lumma is “easy to distribute, difficult to detect, and can be programmed to bypass certain security defenses, making it a go-to tool for cybercriminals and online threat actors, including prolific ransomware actors such as Octo Tempest (Scattered Spider).”
In most instances, the malware is spread through phishing emails or malvertising, typically impersonating trusted brands like Microsoft. The tech giant recently uncovered a campaign in March where actors using Lumma impersonated Booking.com.
Microsoft has found evidence of its use in campaigns targeting the gaming community, education systems, telecommunications, finance, healthcare and manufacturing. Masada noted that Shamel has spoken publicly about his efforts to market Lumma, previously saying he has about 400 active clients.
The outgoing assistant director of the FBI’s Cyber Division, Bryan Vorndran, said the infostealer is responsible for millions of attacks. The FBI urged anyone who believes their computer or device has been compromised to contact the Internet Crime Complaint Center (IC3).
Microsoft officials noted that in addition to its use by prominent cybercriminal groups like Scattered Spider, there is evidence pointing to Lumma’s use in the recent cyberattacks on education tech giant PowerSchool.
An array of Lumma victims have contacted the FBI since 2023, including airlines, universities, banks, insurance companies, hospitals, state governments, internet service providers and more, Leatherman said.

The FBI and Cybersecurity and Infrastructure Security Agency (CISA) published a technical advisory detailing how infected victims can remediate their systems. Several other cybersecurity firms involved in the operation, including Cloudflare, Bitsight and ESET, released technical breakdowns of Lumma and its infrastructure.
Leatherman acknowledged that it is likely the actors behind Lumma will reconstitute their operation but said part of the FBI’s goal is to fracture the trust within the cybercriminal landscape.
“Some of the information that we leverage in these technical operations often lead to our ability to further identify actors down the road. I don't know if that will be the case here, but we will pursue attribution,” he said.
“I think these actors should know that when we have the technical capacity to do this, there are operational security concerns within that ecosystem that they should take note of and maybe not trust the operational security of their colleagues in this environment because of technical operations like this.”
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.
Martin Matishak
is the senior cybersecurity reporter for The Record. Prior to joining Recorded Future News in 2021, he spent more than five years at Politico, where he covered digital and national security developments across Capitol Hill, the Pentagon and the U.S. intelligence community. He previously was a reporter at The Hill, National Journal Group and Inside Washington Publishers.




