Pro-Russia hackers are increasingly targeting hospitals, researchers warn
Cybersecurity researchers said this week that they have observed the pro-Russia hacking group known as Killnet increasingly launch distributed denial of service (DDoS) attacks targeting healthcare organizations since November.
Killnet was established following Russia’s invasion of Ukraine in February 2022, and spent most of the last year launching DDoS attacks against governments and companies around the world.
While the attacks are mostly a nuisance – knocking websites offline for about an hour in most cases – they have caused concern within the U.S. government, particularly when they are launched at critical infrastructure like airports and hospitals.
In recent months, the group has focused its attention on the websites of healthcare organizations, launching a campaign in February that targeted hospitals in more than 25 states.
The Cybersecurity and Infrastructure Security Agency (CISA) said less than half of these attacks – which involved routing a deluge of page requests at targeted websites — were successful in knocking sites offline.
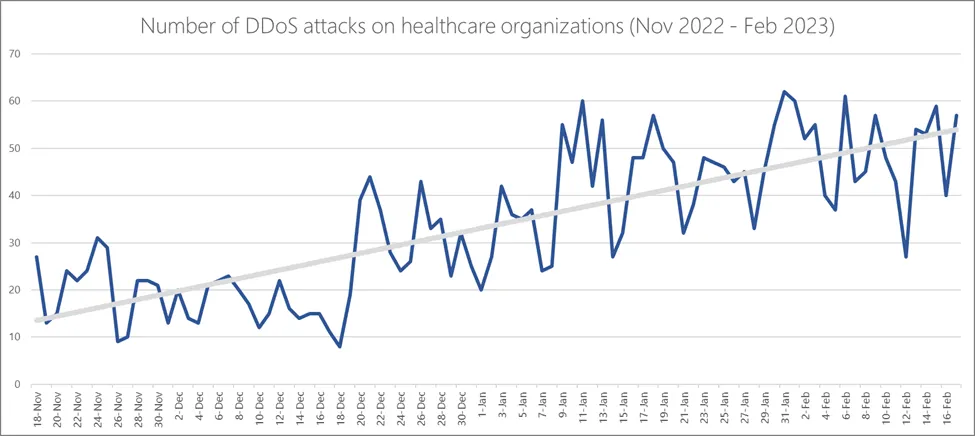
On Friday, Microsoft Azure Network Security Team members Amir Dahan and Syed Pasha published an analysis of DDoS attacks on healthcare organizations using their security tools.
They tracked all of the attacks from November 18, 2022 to February 17, 2023, observing an increase from 10-20 daily attacks in November to 40-60 attacks each day in February.
“The types of healthcare organizations attacked included pharma and life sciences with 31% of all attacks, hospitals with 26%, healthcare insurance with 16%, and health services and care also with 16%,” they said.

Killnet typically tried two different methods – creating many different connections and trying to keep them alive for as long as possible to render a website useless, or establish as many new connections as possible over a short amount of time to drain resources.
“KillNet and its affiliated adversaries utilize DDoS attacks as their most common tactic. By using DDoS scripts and stressors, recruiting botnets, and utilizing spoofed attack sources, KillNet could easily disrupt the online presence of websites and apps,” the researchers said.
DDoS protection services like Cloudflare have reported similar trends. Akamai — another firm that offers similar tools — published a report last month that found DDoS incidents in Europe increased significantly in 2022, with more campaigns now involving extortion tactics. The company also warned that DDoS attacks are now increasingly being used as cover for actual intrusions involving ransomware and data theft.
Cloudflare’s Omer Yoachimik told The Record that their research into the Killnet healthcare DDoS campaign indicates that the attacks were being crowdsourced – meaning Killnet operators are reaching out to other groups and individuals that are either using multiple botnets or different attack methods.
CISA also told The Record that DDoS incidents have become a priority issue for them as they seek to protect critical infrastructure.
“Our regional personnel are working closely with our partners on the ground and we encourage all organizations — including state and local governments — to stay vigilant and to take steps to protect themselves,” the spokesperson said, referencing a guide released with the FBI in October about how organizations can reduce the likelihood and impact of DDoS attacks.
The spokesperson added that for much of the past year, CISA has been helping organizations mitigate DDoS attacks, particularly those launched by Killnet. The agency also worked with several tech companies to provide free resources to under-funded organizations that can help them reduce the impact of DDoS attacks.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



