CISA says Killnet DDoS attacks on U.S. hospitals had little effect
The Cybersecurity and Infrastructure Security Agency said it helped dozens of hospitals respond to a series of distributed denial-of-service (DDoS) incidents last week that were launched by a pro-Kremlin hacking group.
A spokesperson for CISA told The Record that several of the incidents temporarily reduced the availability of the hospitals’ public-facing websites, but there were no reports of unauthorized access to hospital networks, disruption to health care delivery or impacts on patient safety.
The hacking group, Killnet, has spent months launching DDoS attacks on governments across Europe and companies in the U.S. The gang targeted U.S. airlines in October and last week set its sights on U.S. hospitals.
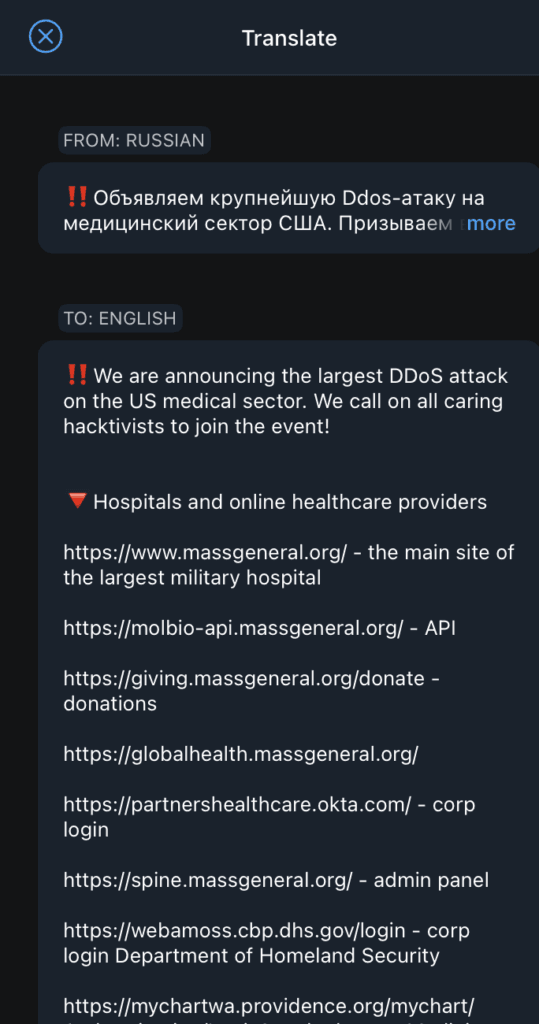
On their popular Telegram channel, the hackers boasted of launching DDoS attacks on hospitals in more than 25 states. Less than half of the attacks — which involved routing a deluge of page requests at hospital websites — were successful in knocking websites offline, CISA said.
The agency said DDoS incidents have become a priority issue.
“Our regional personnel are working closely with our partners on the ground and we encourage all organizations—including state and local governments—to stay vigilant and to take steps to protect themselves,” the spokesperson said, eventually referencing a guide released with the FBI in October about how organizations can reduce the likelihood and impact of DDoS attacks.
The spokesperson added that for much of the past year, CISA has been helping organizations mitigate DDoS attacks, particularly those launched by Killnet. The agency also worked with several tech companies to provide free resources to under-funded organizations that can help them reduce the impact of DDoS attacks.
CISA plans to continue working with the U.S. Department of Health and Human Services (HHS) to communicate with hospitals about government assistance and third-party services.
Cybersecurity firm Cloudflare said hospitals have reached out in recent days looking for help in addressing Killnet’s DDoS campaign.
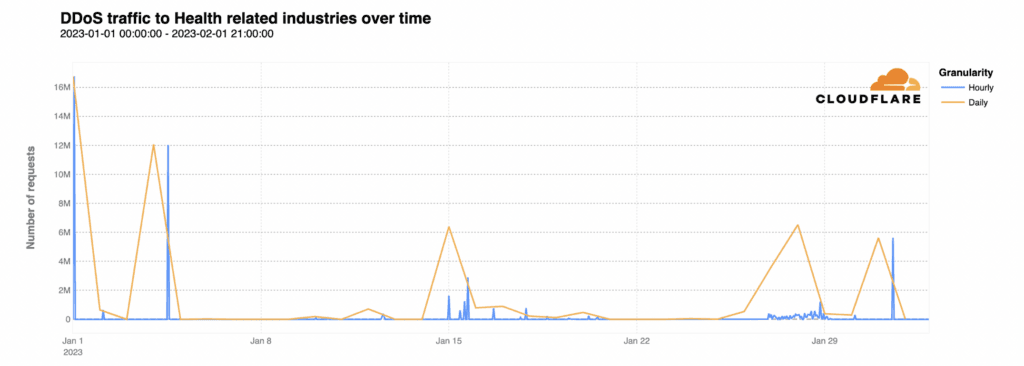
Cloudflare experts said the attacks are not originating from a single botnet — a group of Internet-connected devices taken over by hackers and used to amplify DDoS attacks.
“This could indicate the involvement of multiple threat actors acting on behalf of Killnet, or it could indicate a more sophisticated, coordinated attack,” the company explained in a blog post.
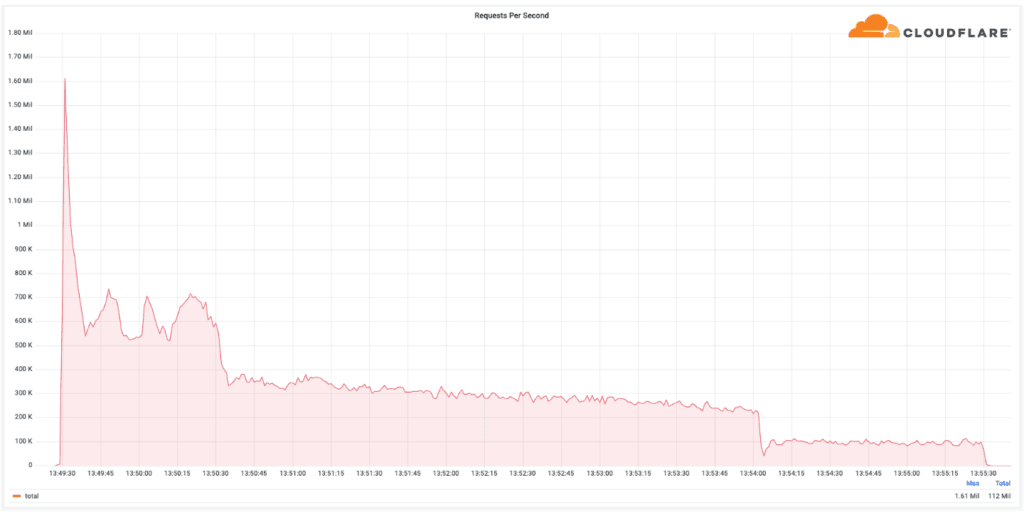
Omer Yoachimik, product manager at Cloudflare, told The Record that attacks have come in several waves over the last week and so far have been relatively small, in the range of the range of 10,000 to 100,000 HTTP requests per second (rps).
The largest attack on a hospital reached 1.6 million rps, with the peak lasting less than 10 seconds and the entire attack taking about six minutes. Cloudflare did not name the hospital.
“That’s a large attack that would degrade services and affect application usability,” he said, adding that most sites would not be able to withstand that without a DDoS protection service.
The largest attack Cloudflare has ever seen affecting any industry was 26 million rps.
Yoachimik explained that their research into the DDoS campaign indicates that the attacks are being crowdsourced – meaning Killnet operators are reaching out to other groups and individuals that are either using multiple botnets or different attack methods.
HHS published an alert warning healthcare institutions that some DDoS incidents may eventually lead to ransomware attacks.
“It is likely that pro-Russian ransomware groups or operators, such as those from the defunct Conti group, will heed Killnet’s call and provide support. This likely will result in entities Killnet targeted also being hit with ransomware or DDoS attacks as a means of extortion, a tactic several ransomware groups have used,” HHS warned.
Since Russia began its invasion of Ukraine 11 months ago, hacking groups like Killnet and NoName057 have targeted an array of government institutions, businesses and organizations across Europe and the United States.
Akamai published a report last week that found DDoS incidents in Europe increased significantly in 2022, with more campaigns now involving extortion tactics. The company also warned that DDoS attacks are now increasingly being used as cover for actual intrusions involving ransomware and data theft.
Akamai’s Patrick Sullivan said attacks on Eastern Europe have skyrocketed from 1% to as high as 30% of all observed attacks on its DDoS platform in 2022.
“There has been a surge in politically motivated DDoS attacks in the past year due to heightened geopolitical tensions,” he said.
“Threat actors have targeted a variety of sectors, including government institutions and private companies, across Western Europe, in addition to US healthcare organizations most recently.”
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



