Coverage of Killnet DDoS attacks plays into attackers' hands, experts say
A notorious pro-Russian hacking group drew headlines on Monday after launching distributed denial-of-service (DDoS) attacks on the websites of airports in at least 24 different states and threatening more operations against U.S. entities.
Researchers at cybersecurity firm Radware said they tracked brief outages on Chicago's air travel website, flychicago.com, as well as the sites for Los Angeles International Airport (LAX), Hartsfield-Jackson Atlanta International Airport (ATL), and Phoenix Sky Harbor Airport (PHX).
Several other website outages were reported later on Monday thanks to the DDoS attacks, which flooded the seldom-used sites with junk traffic.
Despite the scope of the attack, cybersecurity experts said the media coverage was disproportionate to the actual damage done.
They noted that no lasting damage is caused by DDoS attacks and that Killnet operators explicitly seek out attacks that will garner media interest.
In its Telegram channel on Monday, the group’s leaders boasted of being featured on CNN and other outlets.
According to former FBI Chief of Operations Mike McPherson, Killnet originally emerged in February as a collective response to Ukraine’s IT army – a group of hackers supporting the country in its war against Russia.
The goal of the attacks is not necessarily any damage to the websites, McPherson told The Record, but to sow panic and erode a sense of trust that those responsible for ensuring protection can do so adequately.
“This is in addition to the positive notoriety which a successful attack will have on the attacker's reputation,” said McPherson, a senior vice president of security operations at ReliaQuest.
“These events differ from other general attacks, as their intent is not theft of intellectual property or cyber espionage – it’s to be purely disruptive, and at times used as an extortion method or distraction from a separate attack which has yet to be revealed.”
CNN was the first to report that the attacks were launched by Killnet, a pro-Russian hacking group that has been active since the invasion of Ukraine.
The group uses DDoS attacks to briefly take websites offline, previously targeting dozens of government networks across Europe in countries like Romania, Italy, Lithuania, Norway, Poland, Finland and Latvia. They have also targeted the websites of the U.S. Congress, a U.S. tax paying website, and more. Just last week, the group targeted the websites of several U.S. state governments.
The DDoS incidents on Monday involved the websites of airports in Alabama, Arizona, Arkansas, California, Colorado, Connecticut, Delaware, Florida, Georgia, Hawaii, Idaho, Illinois, Indiana, Iowa, Kansas, Kentucky, Louisiana, Maryland, Massachusetts, Michigan, Minnesota, Mississippi, Missouri and more.
Nozomi Networks senior director Gary Kinghorn said the DDoS attacks were not particularly damaging or long lasting and noted that most of the major airports appeared to be responding normally to new connection requests without delay as of early to mid-morning on Monday.
DDoS attacks, he explained, are not targeted attacks that exploit a specific vulnerability, but generally just overwhelm a site’s ability to respond with an enormous amount of traffic from a large number of distributed clients.
Kinghorn said the attacks used against the airports on Monday appeared to be what is called a “SYN flood” – where there are a large number of connection requests that never complete and exhaust the target website's resources on incomplete connections that delay response to legitimate users.
“It’s hard to defend against DDoS attacks because every website that is open to all users can be overwhelmed with a traffic spike of valid connection requests until you can identify and filter out a range of IP sources or expand capacity or bandwidth for the target site,” he said.
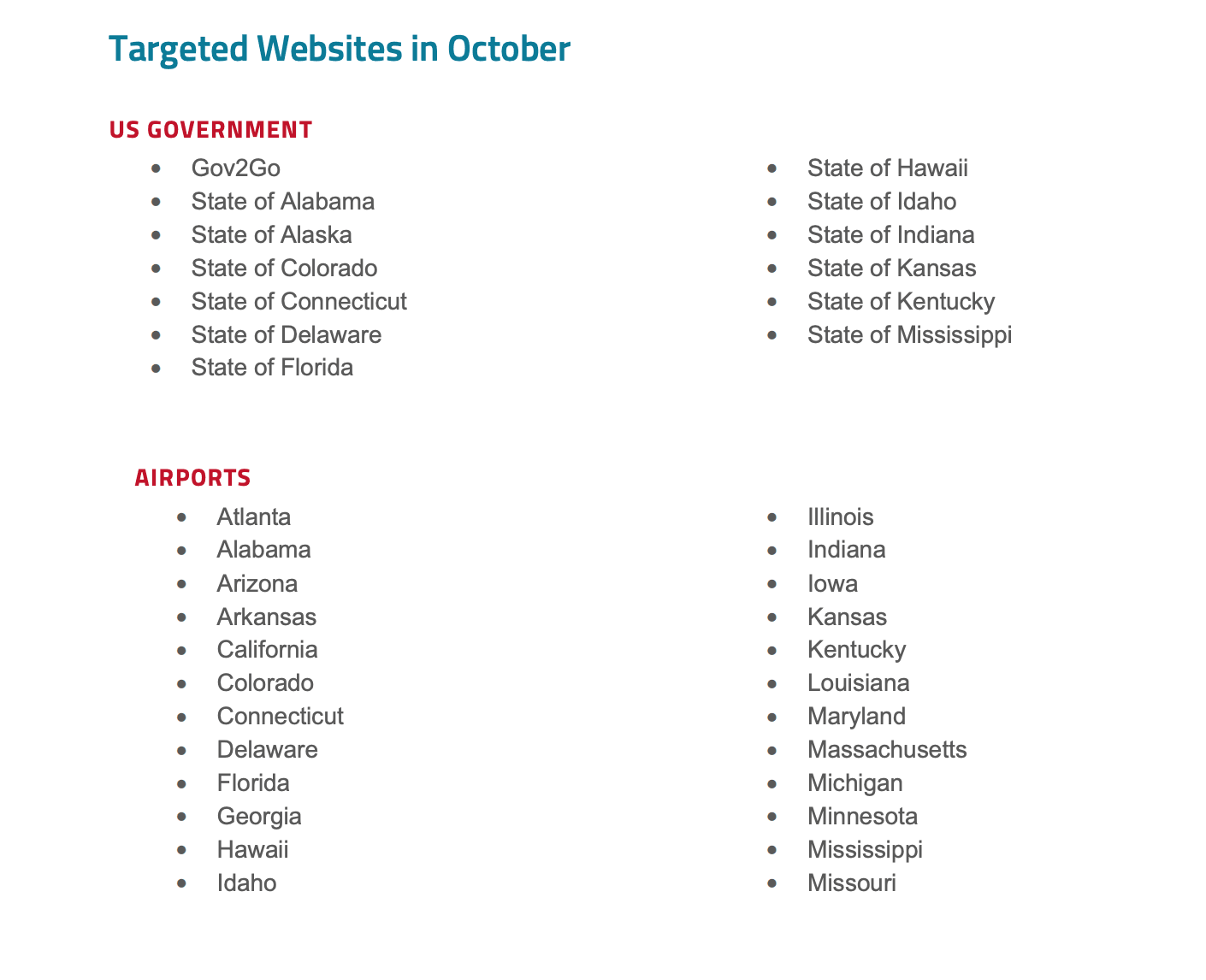
A list of past Killnet DDoS targets. (Radware)
But several experts noted that there was no operational impact on the airports themselves – only minor, brief outages on the airport websites, which typically carry basic information like maps, as well as security line wait times.
Critical Insight president Michael Hamilton called the attacks “essentially an annoyance” that was conducted by “reasonably unsophisticated actors.”
“However, the Russian volunteers are not without skilled cyber actors and it may only be a question of time before more sophisticated attacks are leveled at infrastructure,” he said.
Chris Grove, director of cybersecurity strategy at Nozomi Networks, noted that the Cybersecurity and Infrastructure Security Agency (CISA) referenced Killnet in an advisory about six months ago following the group’s March attack on Bradley International Airport in Connecticut.
CISA at the time warned that similar attacks were on the horizon and provided a list of the tactics Killnet operators typically use.
The DDoS attacks on airport websites coincided with widespread bombing of Ukrainian capital city Kyiv, as well as other parts of the country, in retaliation for the bombing of a bridge connecting the disputed Crimean peninsula to Russia.
Sergey Shykevich, threat intelligence group manager at Check Point Software, told The Record that Killnet likes to focus on the most prominent websites of the federal government, “but specifically on those websites where significant downtime cannot be ignored, but on the other hand not protected enough.”
“Even though Killnet didn’t use sophisticated capabilities, their DDoS attacks last week on US government and transportation sectors were quite successful,” he said. “We shouldn’t be surprised if we see more from Killnet this week.”
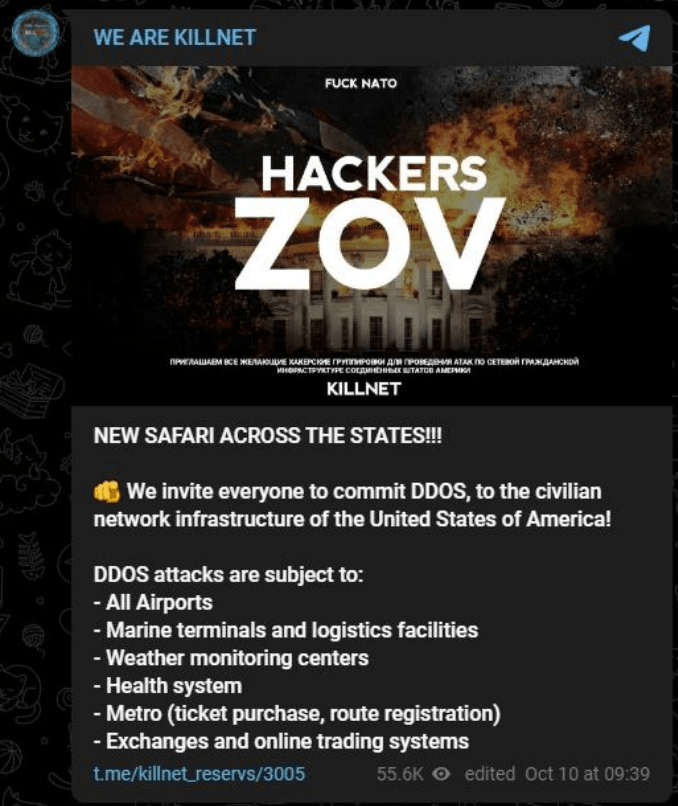
On its Telegram channel on Tuesday, Killnet members turned their attention to DDoS attacks on JP Morgan and several related entities. They also urged members to launch attacks against U.S. civilian network infrastructure like marine terminals and logistics facilities, weather monitoring centers, public transportation systems and more.
KillMilk, the alleged founder of the group, also suggested they may be planning further attacks involving more serious techniques, including wiper attacks, which are designed to destroy data.
“The United States brags about its cyber training, but what it really looks like and how much experience it has in cyber warfare — you will see soon through our actions,” the group’s leader boasted.
“We learned and broke Europe for eight months while the United States prepared to confront us. We are just beginning to cause disruption in America's cyberspace.”
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



