Nation-state hackers using malicious USB drives in attacks in Africa, Asia and Oceania
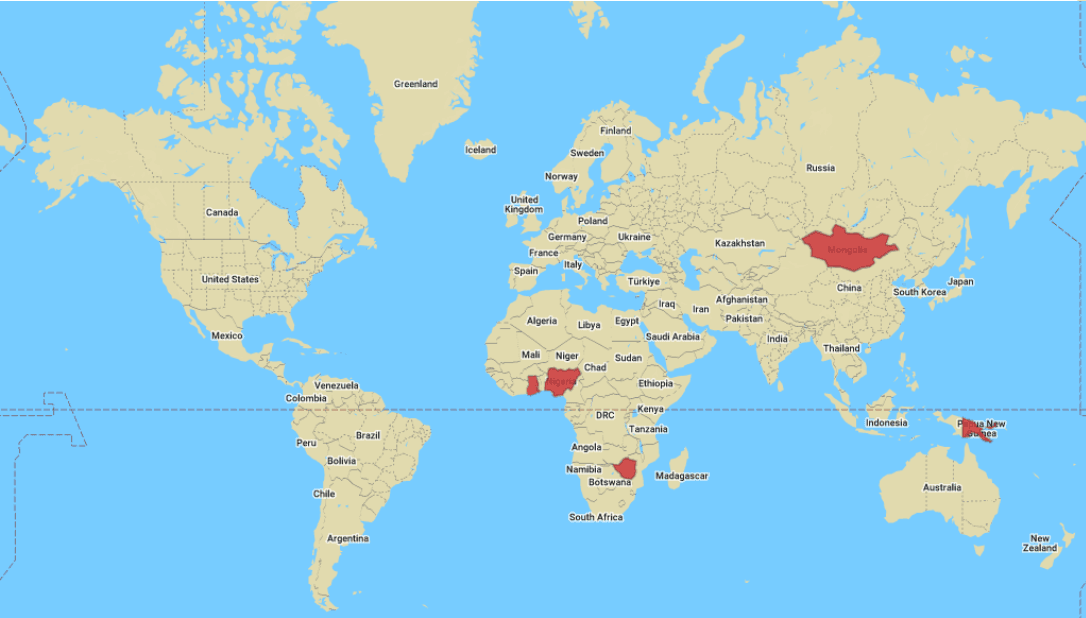
Hackers are using USB drives laden with a strain of malware typically used by the Chinese government to target people in Mongolia, Papua New Guinea, Ghana, Zimbabwe, and Nigeria.
Gabor Szappanos, threat research director at Sophos, said researchers found that last November government organizations across Southeast Asia were being targeted with USB drives that had the PlugX malware – a malicious tool developed in 2008 by Chinese government hackers commonly known as Mustang Panda.
By December, the attack – which he called “retro” because of the use of USB drives – was found thousands of miles away in Africa.
“Now, this latest cluster of USB worm activity is hopping across three different continents. We don’t typically think of removable media as being particularly ‘mobile,’ especially when compared to internet-based attacks, but this method of dispersion has proved to be highly effective in this part of the world,” Szappanos said.
“It's too soon to say that USB worms are making a comeback, but it’s certainly no longer a technique relegated to a decade or two ago. Some of today’s most well-known threat actors are taking advantage of USBs to spread malware.”
The Sophos researchers saw “localized outbreaks” of a new variant of PlugX being spread through the USB drives in Mongolia, Zimbabwe, and Nigeria after initial campaigns in Papua New Guinea and Ghana in January 2023.
The malware and USB delivery method are partially meant to steal information from air-gapped networks – ones that are disconnected from the internet and physically isolated.
When deployed, the malware reaches out to an IP address that was previously tied to Mustang Panda actors by cybersecurity researchers from Palo Alto in 2019.
The PlugX malware copies everything in a victim’s recycle bin as well as anything on the device’s hard drive. It collects .doc, .docx, .xls, .xlsx, .ppt, .pptx and .pdf files for exfiltration.
The researchers explained that USB-based malware was far more common a decade ago, when hackers could compromise an organization by simply dropping thumb drives in certain parking lots.
“However, as defenders alerted users to the potential attack vector, and other method of file storage and transmission became more popular, this technique was abandoned. Now APT groups are re-adding this method as an effective infection and exfiltration method,” the researchers said.
Mustang Panda has previously been accused of targeting prime ministers and leaders across Southeast Asia – including Myanmar – as well as Indonesia’s intelligence agency, and even the Russian government. It has also targeted telecoms worldwide.
Palo Alto Networks released a lengthy report on PlugX in 2021.
The group has used lures tied to COVID-19 and Russia’s invasion of Ukraine to spread malware like PlugX over several years.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



