Backdoor malware found on the Myanmar president's website, again
A cyber-espionage hacking group is believed to have hacked the website of the Myanmar president's office and planted a backdoor trojan inside a localized Myanmar font package available for download on the site's front page.
The intrusion was detected on Wednesday, June 2, 2021, by Slovak security firm ESET.
Researchers said the malware used in the attack has similarities to malware strains used in past spear-phishing campaigns aimed at Myanmar targets by a Chinese state-sponsored hacking group known under codenames such as Mustang Panda, RedEcho, or Bronze President.
Backdoor malware hidden in font package
But while Mustang Panda has a long history of carrying out carefully crafted email-based attacks, for this particular operation, the group appears to have modified a Myanmar Unicode font package the Myanmar presidency was offering for download on its website.
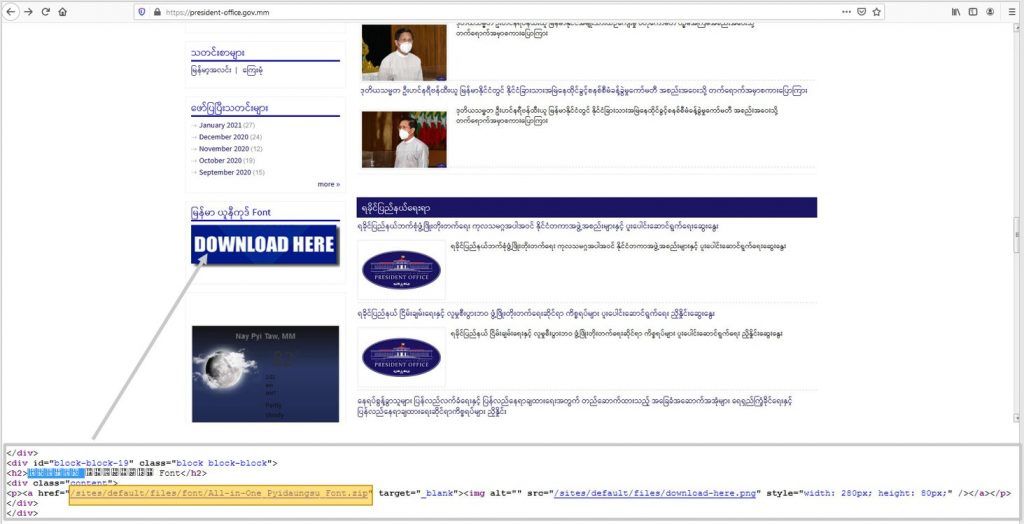
Image: ESET
"In the archive, attackers added a Cobalt Strike loader [named] Acrobat.dll, that loads a Cobalt Strike shellcode," the ESET team wrote in a Twitter thread yesterday.
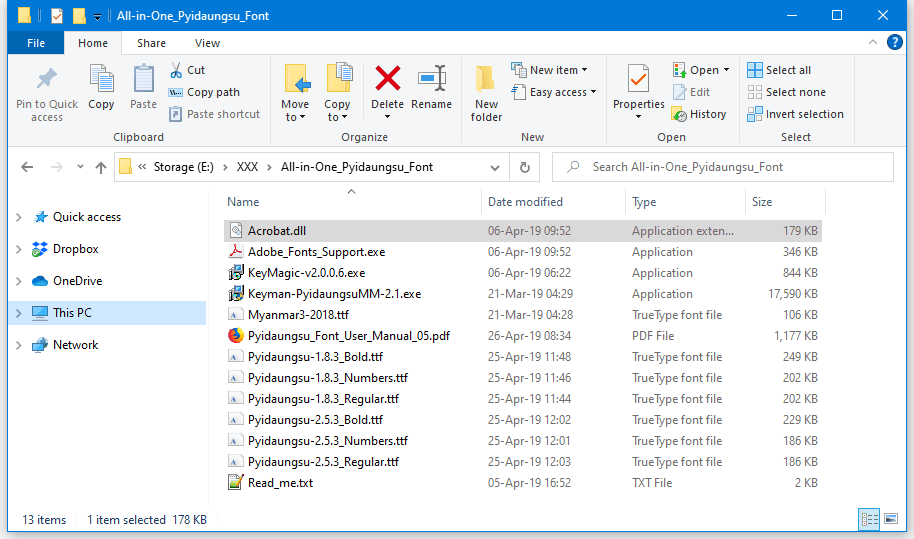
Image: The Record
Researchers said this loader pinged back to a command and control (C&C) server located at 95.217.1[.]81.
The loader also showed similarities with other malware samples that were delivered as file attachments in spear-phishing campaigns aimed at Myanmar targets in the past.
Hidden in files named "NUG Meeting Report.zip," "Proposed Talking Points for ASEAN-Japan Summit.rar," "MMRS Geneva," "2021-03-11.lnk" and "MOHS-3-covid.rar," the archives show the signs of an advanced and stealthy cyber-espionage operation, even if ESET said it has yet to officially confirm Mustang Panda's involvement beyond a doubt.
But yesterday's incident also marks the second time the Myanmar president's office was hacked to host a watering hole attack. The first incident took place between November 2014 and May 2015, when another suspected Chinese cyber-espionage group used the site to distribute a version of the EvilGrab malware.
The website is still compromised at the time of writing and downloading and installing the font package is not advised.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



