ZHtrap botnet deploys honeypots to trap and steal bots from rivals
Security researchers discovered last week a new IoT botnet that deploys honeypots to capture attacks from rival botnets and then uses that information to hijack its rivals' infrastructure.
Named ZHtrap, this new botnet was built on an improved version of the infamous Mirai IoT malware.
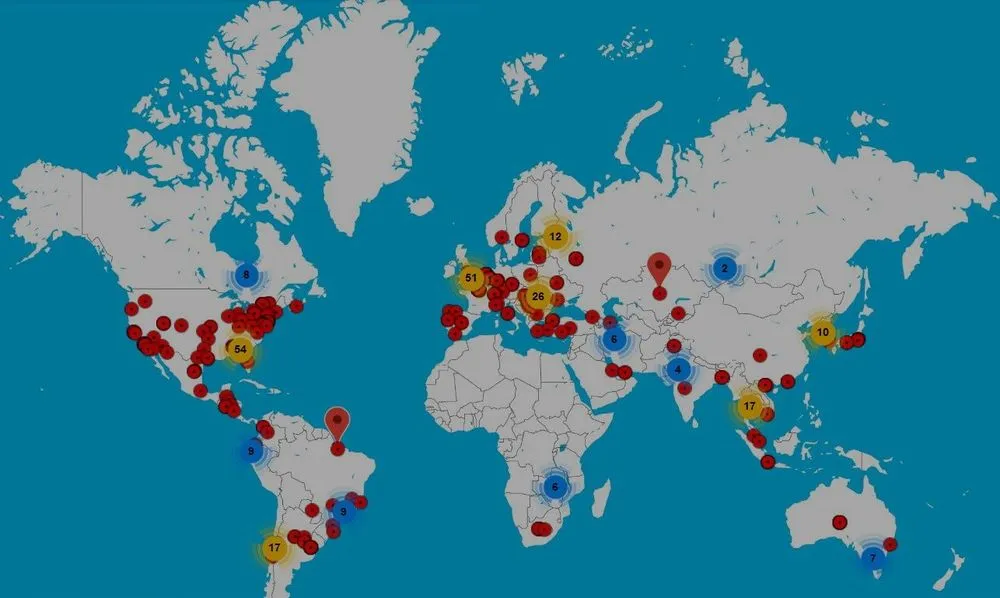
Discovered by the Netlab network security division at Qihoo 360, the botnet works by using vulnerabilities to infect DVRs, CCTV cameras, Netgear routers, and Realtek-based devices.
Once infected, each of these devices is also used to scan the internet for other victims the botnet could attack and infect. All infected devices (called "bots") are then used to launch DDoS attacks, according to functionality found in the ZHtrap source code.
A unique approach to hijacking rivals
But Netlab said that while most of ZHtrap's inner workings resemble what other botnets are also doing, there was one small detail that stood out and made this botnet unique.
On some of the infected devices, Netlab said that ZHtrap installed a honeypot, a type of software specialized in mimicking vulnerable systems and logging what commands attackers perform after accessing the honeypot.
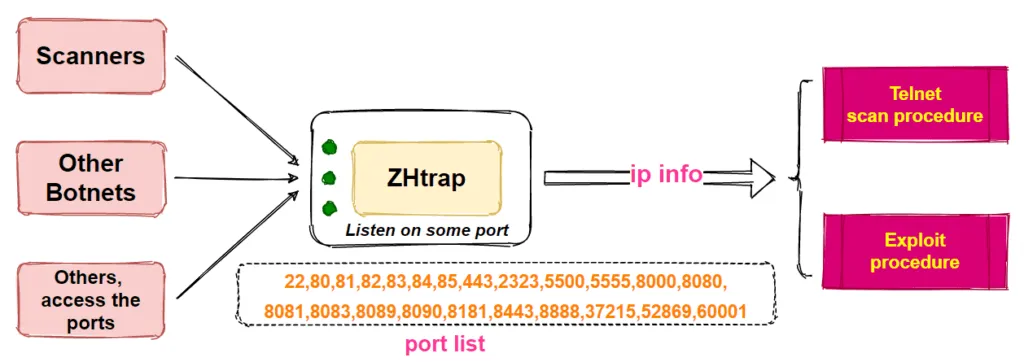
Image: Netlab
Netlab argues that the purpose of these honeypots was for the ZHtrap gang to collect the IP addresses belonging to the scan&exploit bots operated by rival botnet gangs.
Since these bots are by definition unpatched and still vulnerable to attacks, ZHtrap could exploit these systems itself and hijack and capture the attacking bots from its rivals, allowing the botnet to increase its size with minimal effort.
But despite its primary functionality being centered around carrying out DDoS attacks, Netlab also warns that ZHtrap is more advanced than your typical botnet.
The botnet will also install reverse web shell on all infected devices, perform Telnet scans, and even download and execute other payloads, which means the botnet could pivot to an access-as-a-service system and allow third-parties to launch attacks on enterprise networks via the infected devices.
Three versions of this botnet have been seen so far, suggesting it's still actively developed and upgraded with new functionality.
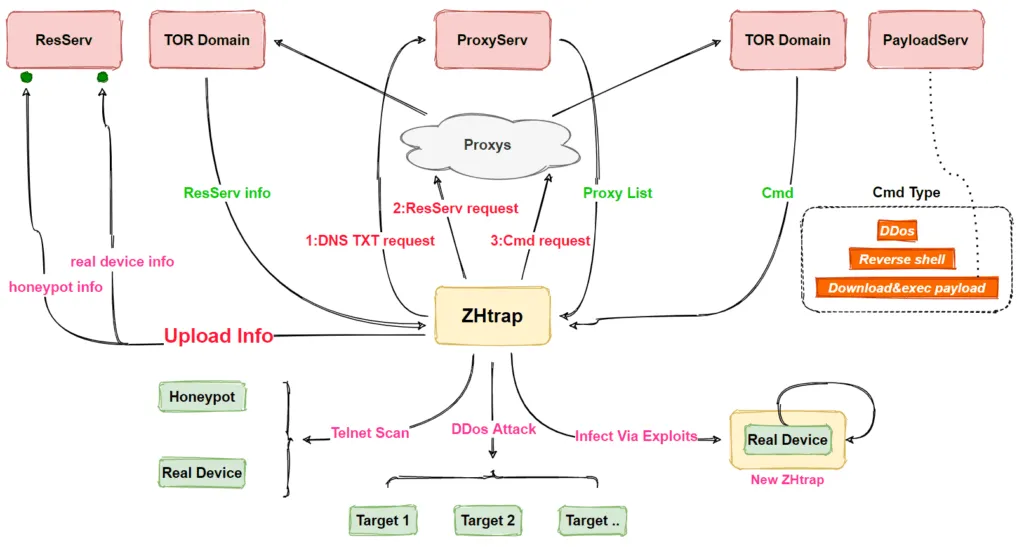
Image: Netlab
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.