US indicts alleged North Korean state hacker for ransomware attacks on hospitals
A hacker working for the North Korean government has been indicted for his alleged role in ransomware attacks on U.S. hospitals and healthcare companies.
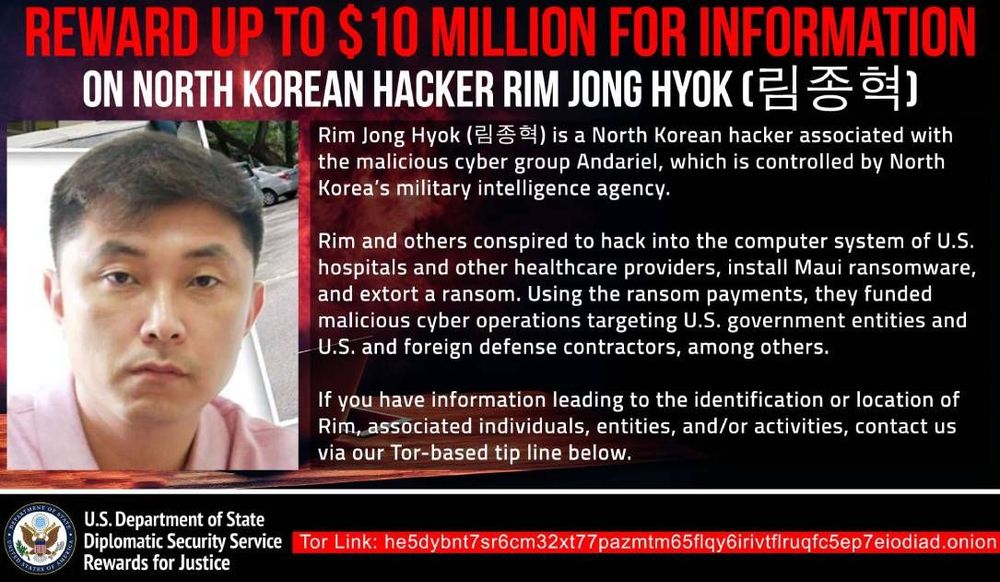
A federal arrest warrant was issued on Wednesday for Rim Jong Hyok, an alleged member of the Andariel Unit within the country’s intelligence agency, the Reconnaissance General Bureau (RGB).
Rim was identified by several U.S. military agencies as the culprit behind several ransomware attacks using the Maui strain that were conducted in 2021 and 2022. At least one of the attacks targeted a hospital in Kansas, where the warrant for Rim’s arrest was issued. The attacks encrypted computers and servers used for medical testing or electronic medical records and disrupted healthcare services.
The FBI said investigators found that Rim and other Andariel actors victimized five healthcare providers, four U.S.-based defense contractors, two U.S. Air Force bases, and the National Aeronautics and Space Administration’s Office of Inspector General.
Rim faces charges for conspiracy to commit computer hacking and money laundering. Senior FBI and Justice Department officials told Recorded Future News that Rim is the only person they had “sufficient evidence to charge at this time,” noting that if they obtain more evidence of other perpetrators they will charge them.
They added that Rim used the ransoms to buy servers that were then used in other cyber espionage hacks against government organizations and customers in the U.S., South Korea and China.
A Justice Department official told reporters on Thursday that it was able to claw back more than $600,000 in cryptocurrency gained through the Maui ransomware attacks and plans to return the funds to the victim organizations. They also were able to take down infrastructure used by the hackers and seize accounts on several platforms related to the attacks.
The State Department also offered a reward of $10 million for information about Rim, who the U.S. government said was last known to be in North Korea.
Andariel attacks
Alongside the indictment, military and law enforcement agencies in the U.S., U.K. and South Korea published advisories on Thursday about the operations of Andariel — which they said has been a key player in North Korea’s longstanding efforts to steal sensitive weapons manufacturing information.
“In one computer intrusion operation that began in November 2022, the malicious cyber actors hacked a U.S.-based defense contractor from which they extracted more than 30 gigabytes of data, including unclassified technical information regarding material used in military aircraft and satellites, much of which was from 2010 or earlier,” the State Department said.
The FBI and other agencies said Andariel, based out of the RGB’s 3rd Bureau in Pyongyang and Sinuiju, has repeatedly targeted “defense, aerospace, nuclear, and engineering entities to obtain sensitive and classified technical information and intellectual property to advance the regime’s military and nuclear programs and ambitions.”
Paul Chichester, director of operations at the U.K.’s National Cyber Security Centre (NCSC), said the operation exposed on Thursday “shows the lengths that DPRK state-sponsored actors are willing to go to pursue their military and nuclear programmes.”
The group is an “ongoing threat to various industry sectors worldwide,” the NCSC said, and continues to update their tactics and skills in attacks on several countries, including the U.S., South Korea, Japan and India.
The hackers continue to use phishing attacks and vulnerabilities like Log4j to breach systems and exfiltrate data.
“The information targeted — such as contract specifications, bills of materials, project details, design drawings, and engineering documents — has military and civilian applications and leads the authoring agencies to assess one of the group’s chief responsibilities as satisfying collection requirements for Pyongyang’s nuclear and defense programs,” the agencies explained.
In some cases, U.S. agencies saw Andariel actors launch ransomware attacks and conduct cyber espionage operations on the same day. In other instances, ransomware was leveraged alongside cyber espionage attacks on the same organization.
The group was previously sanctioned in 2019 by the U.S. Treasury, which said the group “consistently executes cybercrime to generate revenue and targets South Korea’s government and infrastructure in order to collect information and to create disorder.”
A senior Justice Department official said that a key takeaway from the case is that nation-states are now using ransomware to enrich themselves and fund other activities.
“Another takeaway is that North Korea makes a lot of news for their crypto actions, but this is a good reminder that they're also involved in cyber espionage, just like other nation state actors, and ransomware is just one tool in the North Korean toolbox to fund further cyber espionage operations aimed at gaining secrets to help further their larger military and nuclear program objectives,” they said.
“The benefits of these activities are symbiotic. Without the ability to conduct these ransomware operations and receive payments, other cyber operations conducted by DPRK would be difficult to continue.”
The advisory contained contributions from Microsoft and Mandiant, which published its own alert about Andariel on Thursday and tagged the group as APT45.
Michael Barnhart, a principal analyst at Mandiant, said Andariel has a history of targeting government and defense companies around the world, but the indictment “showcases that North Korean threat groups also pose a serious threat to citizens’ everyday lives and can’t be ignored or disregarded.”
“Their targeting of hospitals to generate revenue and fund their operations demonstrates a relentless focus on fulfilling their priority mission of intelligence gathering, regardless of the potential consequences it may have on human lives,” he said.
“For the international community, often silently facing similar threats, these indictments offer reassurance that collaborative efforts are underway to address the issue.”
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.