US agency attributes $540 million Ronin hack to North Korean APT group
The US Treasury’s Office of Foreign Assets Control (OFAC) on Thursday attributed one of the largest decentralized finance (DeFi) hacks ever to notorious North Korean APT group Lazarus.
On March 29, popular DeFi platform Ronin Network was hacked and about $540 million worth of Ethereum and US dollar-pegged stablecoin USDC was stolen.
But on Thursday, OFAC announced sanctions against the North Korean APT group and explicitly tied them to the attack on Ronin Network through the thief's Ethereum address. They listed the address’ owner as Lazarus Group.
According to blockchain analysis firm Elliptic, the decision to hand down the sanctions bans “US persons and entities from transacting with this address to ensure the state-sponsored group can’t cash out any further funds they continue to hold onto through US-based crypto exchanges.”
Over the past two weeks, the group behind the Ronin Network hack has slowly siphoned off about 3,000 ETH – more than $9 million – every two to three days from the amount that was initially stolen, according to blockchain researchers at PeckShield.
The funds have repeatedly been sent to Tornado Cash, a cryptocurrency mixer that allows people to hide the origin of funds. As of April 9, PeckShield said the hackers had laundered about 7.5% of the stolen funds and still had around 159,710 ETH – or $512 million – in the wallet.
By April 14, Elliptic said the hackers had laundered about 18% of their stolen funds.
“First, the stolen USDC was swapped for ETH through decentralized exchanges (DEXs) to prevent it from being seized. Tokens such as stablecoins are controlled by their issuers, who in some cases can freeze tokens involved in illicit activity,” Elliptic explained.
“By converting the tokens at DEXs, the hacker avoided the AML and KYC checks performed at centralized exchanges. This is an increasingly common tactic seen in hacks of this type.”
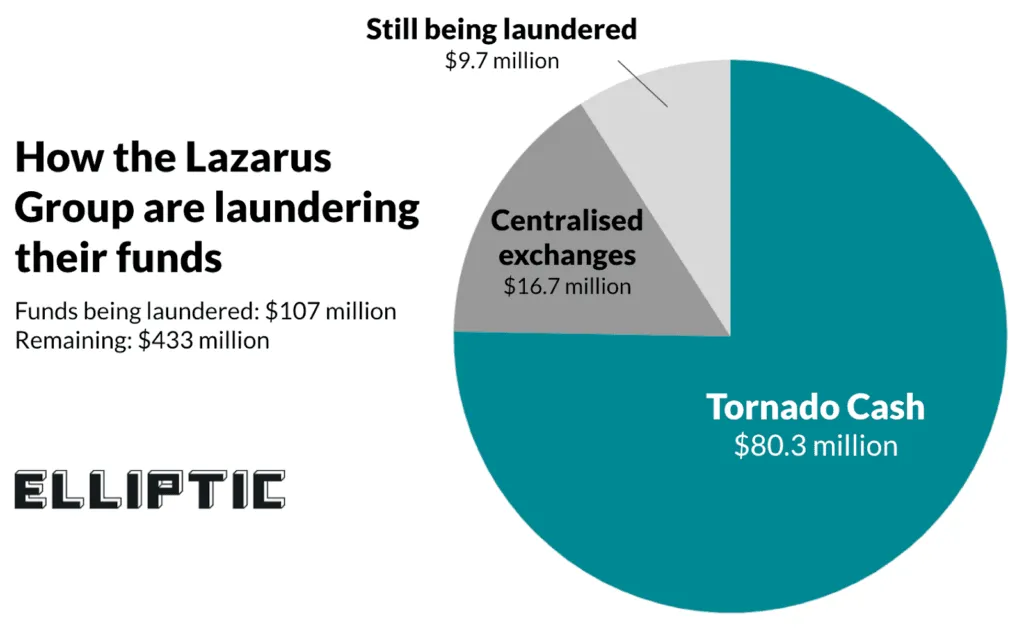
Elliptic noted that the attackers first laundered nearly $17 million of ETH through three centralized exchanges, but the exchanges quickly announced that they would be working with law enforcement.
From then on, the attackers turned to Tornado Cash, laundering about $80.3 million worth of ETH.
“The attacker’s blockchain activity shows that another $9.7 million worth of ETH is in intermediary wallets prepared to be laundered, most likely also through Tornado Cash. This leaves a considerable $433 million remaining in the attacker’s original wallet,” Elliptic explained, adding that like PeckShield and others, they are monitoring the wallets receiving the stolen funds.
They noted that actors connected to Lazarus Group initially only targeted centralized exchanges in South Korea and across Asia before expanding their attack radius in 2021.
Chainalysis, a company that tracks illegal blockchain transactions, said in a January report that hackers working for the North Korean government are believed to have stolen almost $400 million worth of cryptocurrency from seven hacked companies throughout 2021.
Chainalysis attributed all these attacks to the Lazarus Group, a generic term that is often used to describe multiple North Korean threat actors.
Elliptic added that there has been an increase in North Korean missile tests in recent months, noting that many experts believe the country funds its weapons programs through its DeFi hacks.
“It is somewhat unsurprising that this attack has been attributed to North Korea. Many features of the attack mirrored the method used by Lazarus Group in previous high-profile attacks, including the location of the victim, the attack method (believed to have involved social engineering) and the laundering pattern utilized by the group after the event,” Elliptic said.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



