North Korean hackers stole nearly $400M in cryptocurrency in 2021
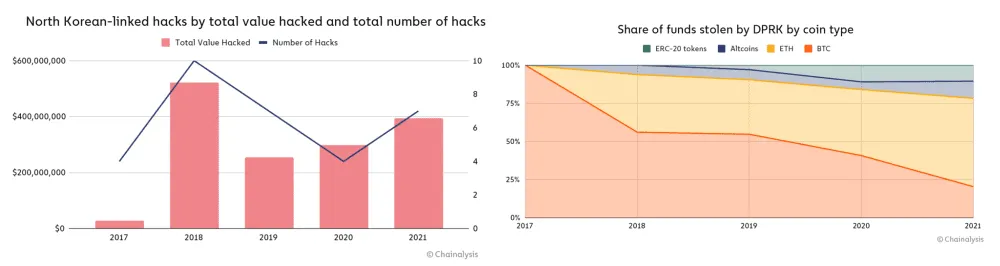
Hackers working for the North Korean government are believed to have stolen almost $400 million worth of cryptocurrency from seven hacked companies over the course of 2021, up from the $300 million they stole from four companies the year before.
Chainalysis, a company that tracks illegal blockchain transactions, said in a report today that 58% of the stolen funds were Ether (ETH), while Bitcoin (BTC) accounted for only 20% of the stolen funds.
Researchers said North Korean hackers laundered and cashed out most of their funds using cryptocurrency mixers and Asian-based crypto-to-fiat exchanges.
But the hackers didn't cash out all their stolen funds; as Chainalysis says it found more than $170 million worth of cryptocurrency the hackers stole from 49 crypto exchanges between 2017 and 2021 in what looked to be "holding accounts," money that the group had yet to move or launder following the initial thefts.
"Whatever the reason may be, the length of time that DPRK is willing to hold on to these funds is illuminating because it suggests a careful plan, not a desperate and hasty one," the company said today.
Kaspersky: BlueNoroff linked to hacks all over the world
Chainalysis attributed all these attacks to the Lazarus Group, a generic term that is often used to describe multiple North Korean threat actors.
But the reality is that North Korean hackers usually operate across specific areas of interest, such as politically-focused cyber-espionage, the tracking of dissidents, economic espionage, and financial theft.
The Lazarus sub-division most often linked to bank and cryptocurrency hacks is a group tracked as BlueNoroff, which the US Treasury Department described as North Korea's money-making machine for its nuclear weapons and ballistic missile programs in sanctions imposed against the group in 2019.
In a separate report published earlier today, Russian security firm Kaspersky said that after years of investigation, it finally managed to link BlueNoroff to numerous hacks all over the world, at cryptocurrency companies in Russia, Poland, Slovenia, Ukraine, the Czech Republic, China, India, the US, Hong Kong, Singapore, the UAE, and Vietnam.
The campaign, which Kaspersky had been tracking internally as SnatchCrypto since 2017, used malicious documents sent via email or LinkedIn messages to individuals working at cryptocurrency companies.
Once the victim viewed and interacted with these files, they would be infected with a backdoor that would allow the hackers to search through their computer and keep an eye on what the individual was doing.
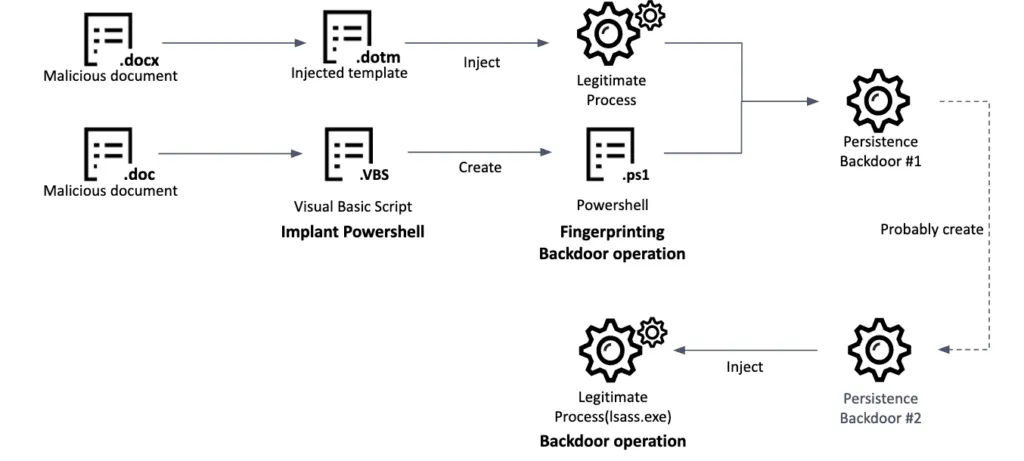
Other campaigns were even less sophisticated and used LNK (Windows shortcut) files, but the end result was the same, with the BlueNoroff gang gaining access to a victim's device.
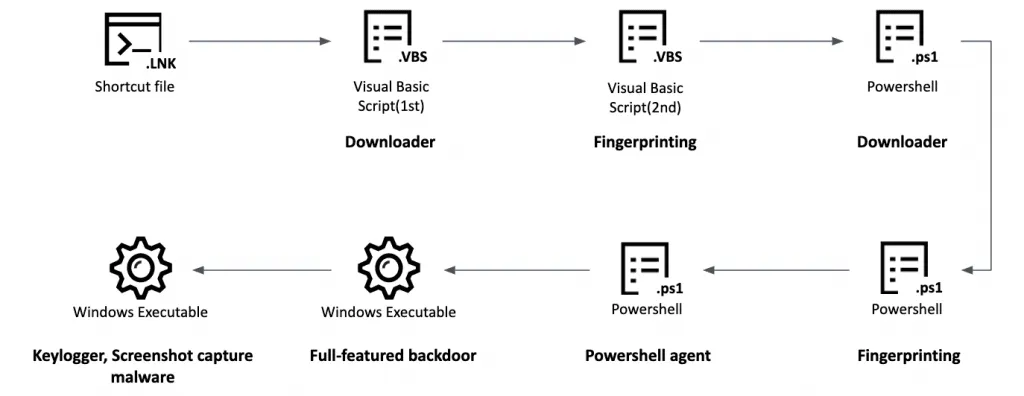
"In some cases where the attackers realized they had found a prominent target, they carefully monitored the user for weeks or months," the Kaspersky team said. "They collected keystrokes and monitored the user's daily operations, while planning a strategy for financial theft."
Hackers replace victim's Chrome extension to steal funds
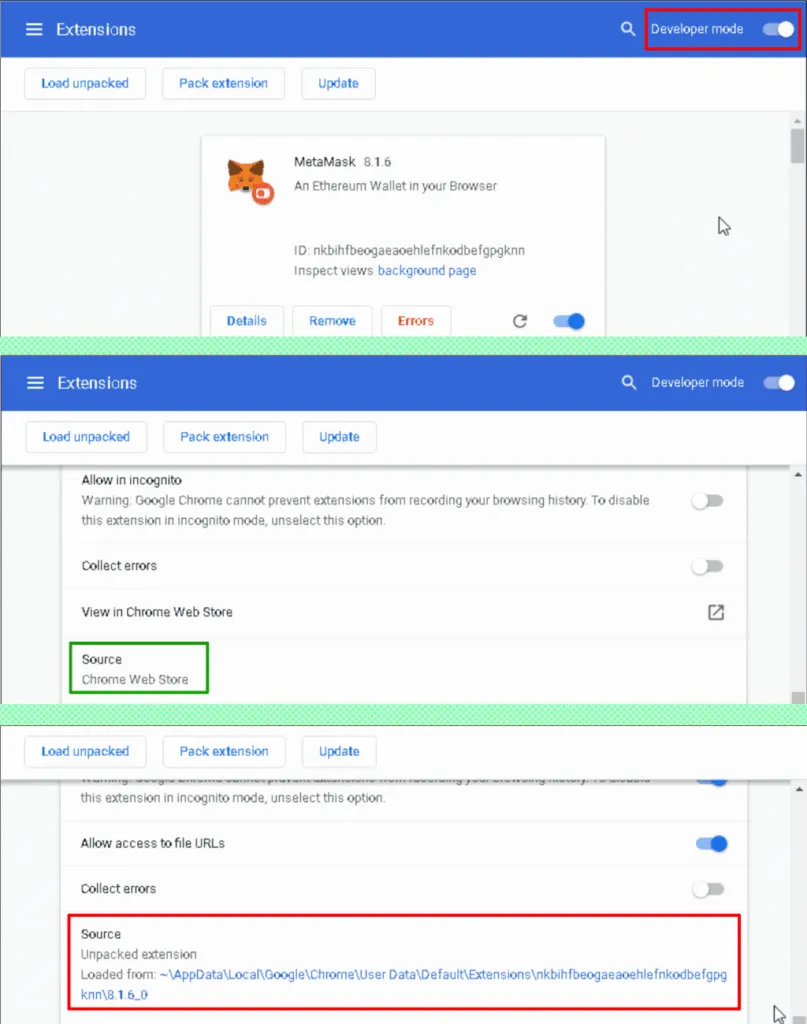
As a testament to the level of their skill, Kaspersky said that in particular incidents, BlueNoroff hackers went as far as to develop a malicious version of the official Metamask Chrome extension, which they later installed locally, on a victim's device, replacing the original one, installed from the Chrome Web Store.
Kaspersky researchers said this extension was modified to detect when a victim would initiate a transaction and then hijack transaction parameters and send most of the target's funds to a BlueNoroff account.
"All this sounds easy, but in fact requires a thorough analysis of the Metamask Chrome extension, which is over 6MB of JavaScript code (about 170,000 lines of code)," Kaspersky researcher said about the length and effort the hackers went to pull off an attack.
"The injection is very hard to find manually unless you are very familiar with the Metamask codebase. However, a modification of the Chrome extension leaves a trace," the Kaspersky team said, pointing to the fact that when an attack was executed, the Developer Mode option in Chrome extensions section would have had to be turned on, and the source of the Metamask extension would have changed from the Play Store to a local address as well.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



