UK water company confirms cyberattack after confusion over ransomware group threats
South Staffordshire PLC, the supplier of water to about 1.6 million people in the South Staffordshire and Cambridge regions in the U.K., announced a cyberattack on Monday.
The company did not respond to requests for comment but in a statement said the incident did not affect its ability to supply safe water and focused solely on their corporate IT network.
“We can confirm we are still supplying safe water to all of our Cambridge Water and South Staffs Water customers,” the company said. “This is thanks to the robust systems and controls over water supply and quality we have in place at all times as well as the quick work of our teams to respond to this incident and implement the additional measures we have put in place on a precautionary basis.”
The company said it is working with government and regulatory authorities to resolve the incident.
South Staffordshire PLC is owned jointly by U.K.-based independent infrastructure investment company Arjun Infrastructure Partners and Mitsubishi Corporation. Neither company responded to requests for comment.
The announcement came hours after cybersecurity experts expressed confusion and concerns about comments made by the Cl0p ransomware group.
The prolific ransomware gang claimed on its leak site that it attacked Thames Water — another water provider in the U.K. But when experts dug through the leak, it became clear that the ransomware group may have named the wrong victim.
i mean i'm doing correlation between personel names in the leaked data and they have water in them…. just it's a bit further north than the THAMES! pic.twitter.com/c7j1UmSKFQ
— MrR3b00t | #StandWithUkraine #DefendAsOne (@UK_Daniel_Card) August 15, 2022
Many of the documents are tied to South Staffordshire PLC or are about residents of South Staffordshire.
The leaks included U.K. passports, driver’s licenses, credentials and screenshots of systems within South Staffordshire PLC’s operational network.
Cl0p included a lengthy note alongside the stolen files. Even though they apparently named the wrong company in their post, the group claimed to have been in contact with a negotiator.
Cl0p claimed that they "spent months" in the company's system and saw "first hand evidence” of bad security practices. Despite attacking the water authority, the group said it does not attack critical infrastructure and decided against encrypting the company’s systems.
Among the usual stuffs like passport photos and etc, Clop ransomware gang published these screenshots in the leak page for Thames Water…
— MalwareHunterTeam (@malwrhunterteam) August 15, 2022
pic.twitter.com/hqrPzekqbZ
"But we show them that we have access to more of 5 TB of data. Every system including SCADA and these systems which control chemicals in water," the group wrote. "Do not be afraid from us. We do nothing. But other group who will try are not will be as honest as we," the group added.
They went on to claim the company's negotiator was only interested in "buying time" and offered a low ransom. The group said it considered the ransom low because they believe it "would be easy to change the chemical composition for their water."
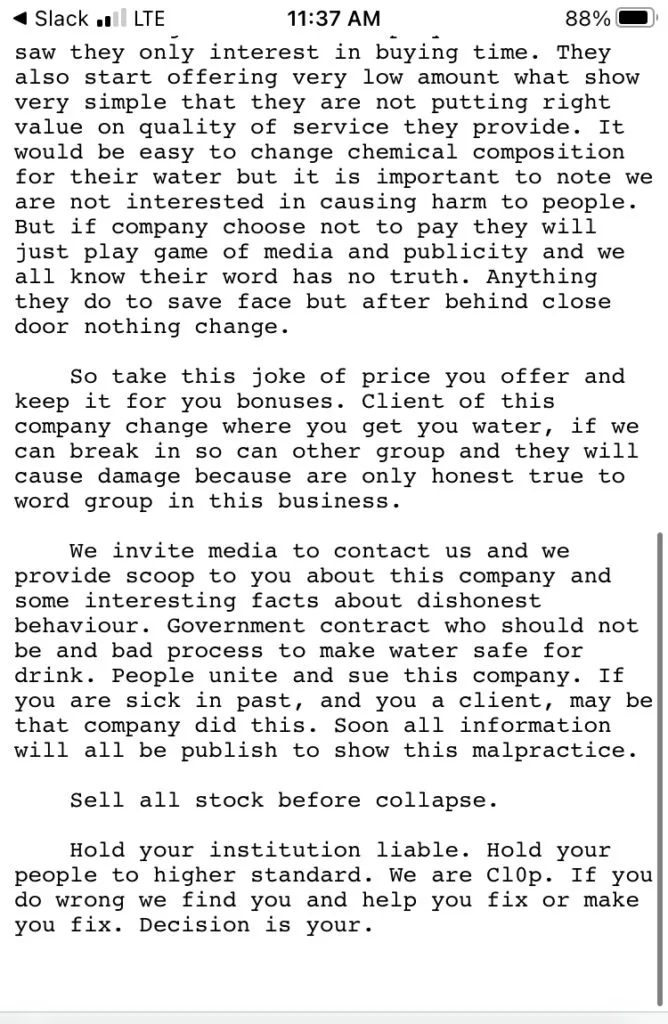
The note reiterates that the gang is "not interested in causing harm to people” but believed other groups would.
The group made several more claims about the company’s internal processes and alleged government deals.
Ransomware attacks on water utilities have increased significantly over the last two years. In February 2021, city officials in Oldsmar, Florida, said a hacker attempted to poison the local water supply by changing the concentration of sodium hydroxide at a water treatment plant to toxic levels.
The attack was spotted and stopped before anyone in the 15,000-person city was harmed they said. In March 2021, the U.S. Department of Justice indicted a Kansas man on charges of hacking into a local water utility in March 2019 in an attempt to sabotage operations and harm the local population.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



