DNS hijacks at two cryptocurrency sites point the finger at GoDaddy, again
Two cryptocurrency portals are currently dealing with DNS hijacking attacks that are redirecting visitors to fake versions of their websites where crooks are trying to collect seed phrases and private keys from visitors so they can access wallets and steal their funds.
The attacks have hit the Cream Finance and PancakeSwap services earlier today, according to messages posted by both companies on their official Twitter profiles.
Our DNS has been compromised by a third party; some users are seeing requests for seed phrase on https://t.co/Hr6S4Fqodo. DO NOT enter your seed phrase.
— Cream Finance (@CreamdotFinance) March 15, 2021
We will never ask you to submit any private key or seed phrases.
There is a chance we have been DNS hijacked, the same as @CreamdotFinance.
— PancakeSwap Ev3ryone's Favourite D3X (@PancakeSwap) March 15, 2021
Until we are able to confirm this is not the case, do not use the site.
We will confirm ASAP.
In the meantime, better safe than sorry.
Please retweet for visibility! https://t.co/keLsiPFcOh
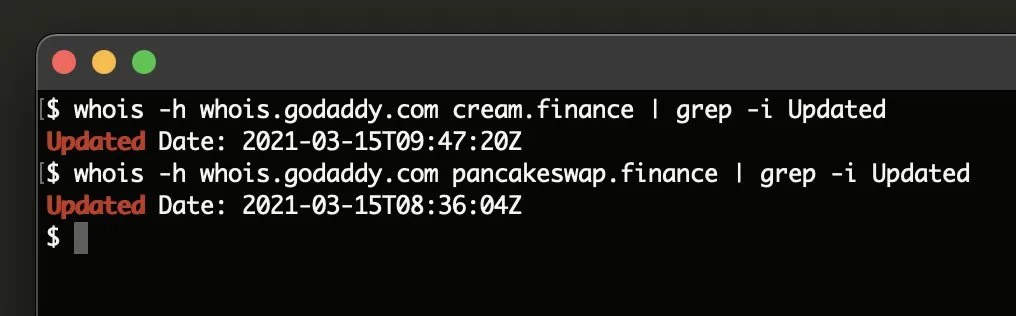
According to a source who tipped The Record earlier today, the same attacker is believed to be behind both incidents as DNS records for both websites were changed within a minute of each other.
Once the DNS records were pointed to the attacker's IP addresses, visitors going to both sites were redirected to phishing sites where the attacker tried to collect seed phrases and private keys using pop-ups like the one shown below.
don't do this pic.twitter.com/9tjUn0sdoh
— icebergy (@icebergy_) March 15, 2021
These seed phrases and private keys would have allowed attackers to access customer cryptocurrency wallets and initiate transactions to steal their funds.
At the time of writing, both services are still dealing with the attacks. Users are advised to keep an eye on both companies' Twitter profiles for updates before navigating to their websites and logging into accounts.
Fingers pointing at GoDaddy again
Precise technical details about how attackers managed to modify DNS records for both websites are still shrouded in mystery, but as security researcher MalwareHunterTeam pointed out earlier today, both companies managed their DNS records via web hosting company GoDaddy.
Both @CreamdotFinance and @PancakeSwap have their domains registered by GoDaddy...
— MalwareHunterTeam (@malwrhunterteam) March 15, 2021
So, if someone somehow not phished both companies' people at the same time, it's again time to say thanks to GoDaddy. pic.twitter.com/LEFd40HqtI
While there is the possibility that the attackers compromised web hosting accounts for both companies in separate incidents, there is also the possibility that attackers might have compromised a GoDaddy employee's account to change DNS server records and execute the attack.
The latter scenario happened twice before last year, in March and November 2020, with attackers executing a phishing attack against GoDaddy employees to collect their work credentials and then use official GoDaddy accounts to modify DNS records for multiple cryptocurrency and domain hosting-related sites. Victims of the previous attacks included the likes of Escrow.com, Liquid.com, NiceHash.com, Bibox.com, Celsius.network, and Wirex.app.
A GoDaddy spokesperson was not immediately available for comment in regards to the recent attacks on Cream Finance and PancakeSwap.
But such an attack would have also been possible if the attackers phished IT staffers at both sites for their web hosting management account credentials.
Phishing attacks targeting web hosting accounts have become common since the start of 2019, when FireEye exposed an Iranian state-sponsored hacking group behind a global DNS hijacking campaign.
The campaign involved the Iranian hackers phishing their targets for web hosting-related accounts and then using a DNS hijack attack to redirect traffic for email servers through infrastructure controlled by the attackers, allowing them to phish employees and read their emails.
The tactics used by the Iranian hackers were almost immediately duplicated by cybercrime groups looking to make a profit, and cryptocurrency-related portals have been their favorite targets due to the large amounts of funds they process on a daily basis, but with very few of the security safeguards implemented by banks and other financial institutions.
Updated on March 20 to add that both Cream Finance and PancakeSwap have now confirmed that the incident had occurred after the attackers managed to gain access to their GoDaddy accounts.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



