Pro-Ukraine group says it took down Trigona ransomware website
A group of pro-Ukraine hacktivists known as the Ukrainian Cyber Alliance says it has shut down the leak site run by the Trigona ransomware group.
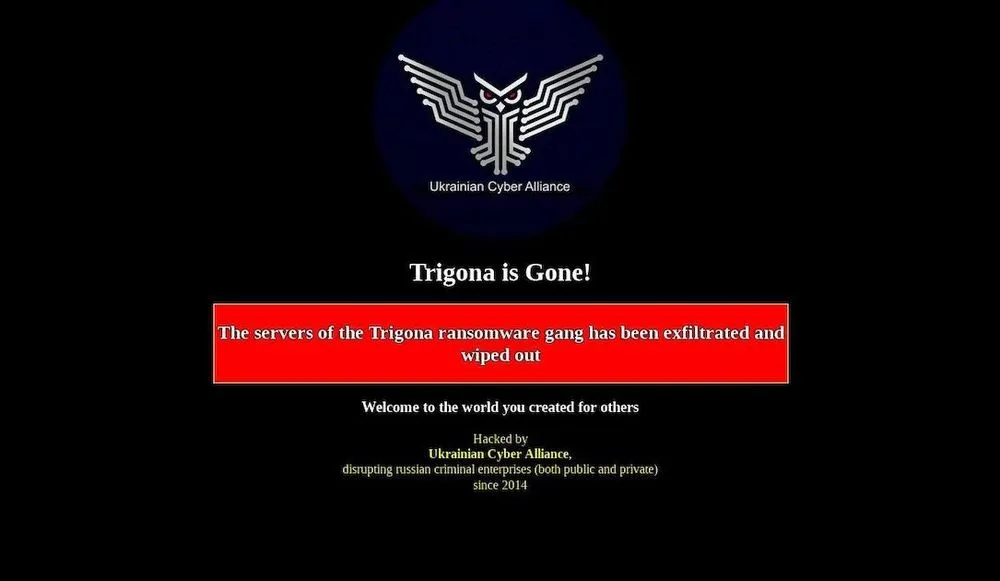
According to the spokesperson for the alliance, who goes by the online alias "herm1t," the hacktivists wiped out 10 of the Trigona gang's servers, defaced its website and exfiltrated data about the cybercrime operation.
“Their entire infrastructure is completely blown away," herm1t said on Tuesday in a Facebook post. This includes the website’s administrative panel, landing page, blog, internal server, cryptocurrency wallets and developer servers.
The spokesperson, who also uses the name Sean Townsend, claims that the alliance treated Trigona just as the gang had treated its victims. “Welcome to the world you created for others!” herm1t said on X, formerly Twitter.
Trigone. The servers of the Trigona ransomware gang has been exfiltrated and wiped out by @UCA_ruhate_ Welcome to the world you created for others! pic.twitter.com/ALiud4sPQv
— herm1t (@vx_herm1t) October 17, 2023
Trigona Leaks is a dark web “name-and-shame” extortion blog allegedly operated by the Trigona ransomware group. As of March, the website advertised stolen data from four victims located in the U.S. and Europe, according to Dmitry Smilyanets, a product management director at Recorded Future, the cybersecurity firm that is the parent company of Recorded Future News.
“They were a real threat,” Smilyanets said.
Herm1t told Recorded Future News that the group plans to go through the obtained data themselves and possibly, in the future, share some of it or pass it on to other researchers.
Last week, herm1t claimed to have hacked the Trigona group’s account for the Confluence collaboration platform run by the software company Atlassian.
“This revelation stirred significant attention, highlighting that even ransomware gangs are using platforms like Confluence,” said threat intelligence platform FalconFeeds.
Trigona’s activity has drastically declined this month, according to threat researcher Paul Pajares of cybersecurity company Trend Micro. The primary flaw has been poor management of the leak site, he told Recorded Future News.
Typically it's government agencies, rather than other hackers, that shut down major ransomware websites. For instance, there's the U.S. Department of Justice's campaign against the Hive ransomware group and the shutdown of RaidForums.
“Takedowns from government agencies carry more weight,” said security researcher Dominic Alvieri. He said that Trigona's hack seems more personal.
“It should be pretty easy for Trigona to close the old leak site and probably set up new servers/hosting elsewhere,” Alvieri said.
Known for tough deadlines
The Trigona ransomware family was first observed in June 2022. It mostly targeted tech, healthcare, and banking companies in the U.S., India, Israel, Turkey, Brazil and Italy, according to a report by Trend Micro.
Trigona attempts to extort its targets with intimidating time requirements, said researchers at SentinelOne. Victims are then led to a payment portal on the dark web where the group prefers to accept Monero cryptocurrency.
The threat actor behind Trigona is might have a connection to the Russia-linked AlphV group, also known as BlackCat, researchers said.
“We believe that any similarities between Trigona and BlackCat ransomware are only circumstantial,” Trend Micro said. “One possibility is that ALPHV collaborated with the threat actors deploying Trigona but were not actually involved with its development and operation.”
Daryna Antoniuk
is a reporter for Recorded Future News based in Ukraine. She writes about cybersecurity startups, cyberattacks in Eastern Europe and the state of the cyberwar between Ukraine and Russia. She previously was a tech reporter for Forbes Ukraine. Her work has also been published at Sifted, The Kyiv Independent and The Kyiv Post.