Threat actors exploiting Twitter changes after Musk takeover, research shows
Researchers at ProofPoint are seeing a noticeable increase in phishing campaigns targeting the credentials of Twitter users following Elon Musk's takeover of the company.
After Tesla CEO Elon Musk completed his acquisition of the social media giant, he pushed through several changes – including the controversial feature allowing people to pay a monthly $8 fee to receive a “verification” check.
The feature was quickly abused and had consequential effects on the market performance of several companies that were spoofed by both cybercriminals and jokesters.
Sherrod DeGrippo, vice president of threat research and detection at Proofpoint, said cybercriminals are now using verification phishing campaigns to largely target media and entertainment figures, journalists, and other users who are already verified on Twitter.
“Multiple campaigns have used lures related to Twitter verification or the new Twitter Blue product, such as ‘Twitter blue badge Billing Statement Available.’ We have seen these campaigns using both Google Forms for data collection as well as URLs that redirect to actor-hosted infrastructure,” DeGrippo said.
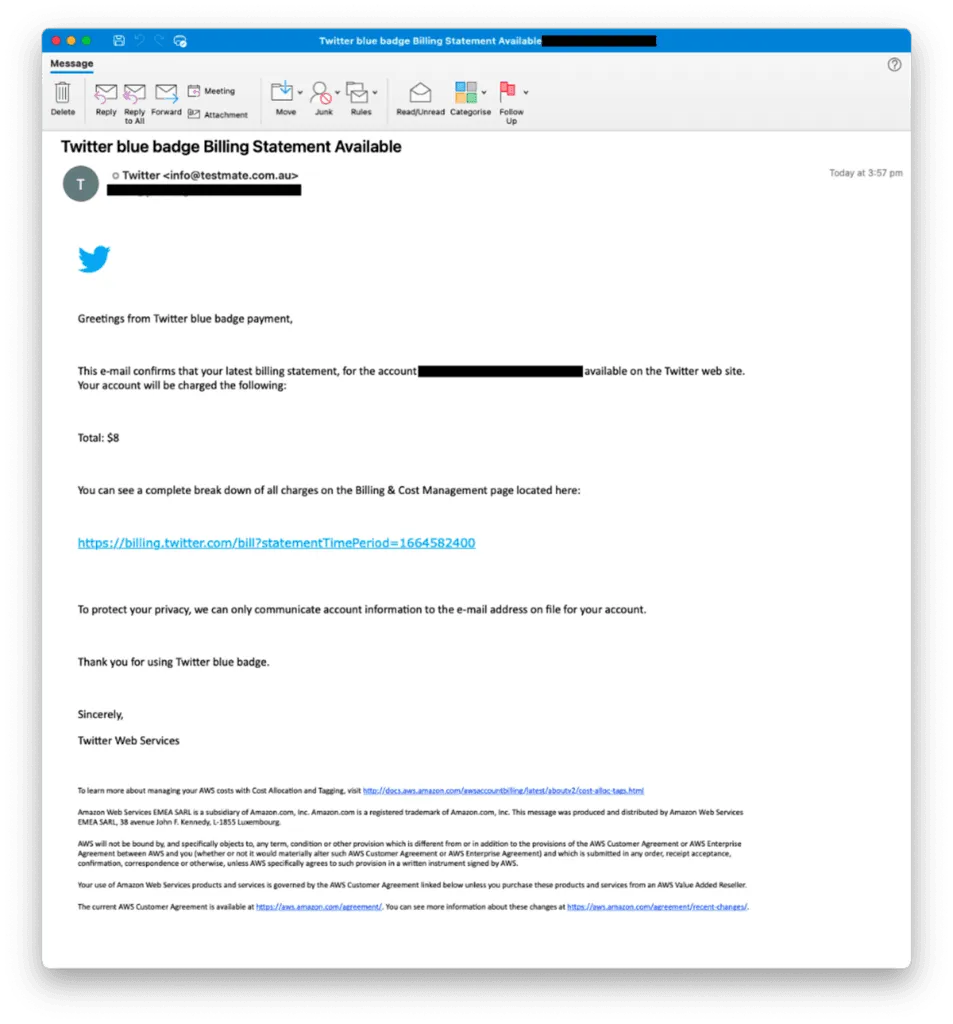
“These campaigns typically target media and entertainment entities including journalists, and users who appear to be verified on Twitter. Often, the email address matches the Twitter handle used, and/or the email is available in the user’s Twitter bio.”
DeGrippo added that historically, they have seen occasional Twitter credential phishing using verification-related lures from cybercrime threat actors but noted that the activity has increased in recent weeks. Access to accounts is extremely lucrative, according to DeGrippo and Matt Chiodi, chief trust officer of Cerby.
Chiodi explained that social media accounts are generally managed by marketing teams and can have access to hundreds of millions of corporate dollars for advertising.
There is also considerable financial and brand damage risk to organizations.
“Not only could criminals siphon off that cash, they could defame a company’s Twitter profile with offensive content,” he said. “Social media phishing incidents like this remain my top concern.”
DeGrippo said legitimately verified Twitter accounts typically have larger audiences than the average user, and compromised accounts can be used to spread misinformation, urge users to engage with additionally malicious content like fraudulent cryptocurrency scams, and can be used to further phishing campaigns to other users.
Proofpoint previously published research on a government-backed hacking group that regularly targeted media users with Twitter-related phishing lures. The cybersecurity company has also seen an increase in “pig butchering” fraud – which involves cybercriminals reaching out to victims over text or through social media sites and buttering them up over weeks before introducing scams to steal money or cryptocurrency.
Twitter data suggests most of the people buying Twitter Blue are promoting three things: right wing politics, cryptocurrency, and porn. https://t.co/yiXnqX1gw8
— Adam Smith (@adamndsmith) November 16, 2022
Chiodi added that the phishing issue was part of a larger problem surrounding the lack of enterprise-grade authentication options, something none of the most prominent social media platforms offer.
Most platforms like Twitter do not offer security standards such as single sign-on or automated user creation – instead opting to hold on to the username/password combo that can be easily exploited by cybercriminals.
“This is unacceptable for tools that are so widely used by consumers and critical to enterprises and democracy,” he said.
“Phishing will continue to grow until the world moves to passwordless. Remember, passwords aren’t the problem, it’s how users manage them since they have traditionally had no options to help automate the entire process from account creation to login.”
Twitter on the dark web
According to a new report from Cybersixgill, the dark web is overrun with people selling access to compromised Twitter accounts and bots with the ability to inflate follower accounts. The report's data predates Musk's takeover of the company but Dov Lerner, head of threat intelligence at Cybersixgill, said it is clear that threat actors are monitoring changes and will seek creative ways to exploit them.
Their research shows that a significant portion of inauthentic Twitter accounts may have been built with tools and services found on the deep and dark web – a problem Lerner said is getting worse.
“On the underground, Twitter users can purchase bots to inflate their followers and activities, such as likes and replies. This can enable them to churn out spam or to simulate a community. Alternatively, they can simply purchase pre-made accounts with the followings,” Lerner said.
“For example, one bot sold on underground forums advertises mass subscriptions, likes, retweets, comments, and tweets, as well as the ability to change the profile’s username, name, and description. In essence, this allows the bot’s user to operate a firehose of activity, spamming however they desire.”
Other bots being sold for just $100 allegedly give users automatic follows, likes and retweets. Anyone who purchases it will be given the source code that allows them to tailor the features that mean most to them. Another tool for sale offers buyers an additional 1,500 followers per day on Twitter, Instagram and YouTube.
For the compromised accounts that are for sale, buyers are given usernames, passwords, and complete control.
“One actor posted a handful of accounts for sale at prices ranging from tens to hundreds of dollars. These accounts were largely crypto/NFT-themed, each with thousands to tens of thousands of followers,” Lerner said.
“In another example, an actor sought to sell an account with 45,000 followers for $450.”
Lerner explained that these accounts may have been compromised through credential stuffing attacks or may have come from compromised endpoints on access markets, which sell access to or data stolen from infected machines.
“A massive number of Twitter accounts could have been compromised this way: out of the over 2,146,000 compromised machines sold on access markets over the last year, a whopping 435,000 (20.3%) included access to a Twitter account,” Lerner added.
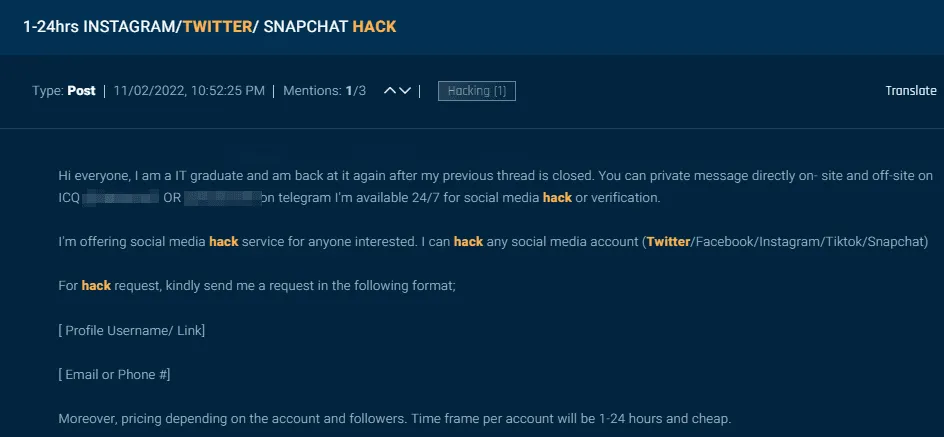
Some underground operators even offer hacking services for those who want to target specific accounts. At least one actor offered hacking services within 24 hours and priced their services based on the account type and number of followers. Other services offer ways to get profiles banned.
Lerner said hackers have already found ways to exploit Musk’s Twitter Blue service.
“While the attack exploited a new feature, in our understanding its techniques of building large accounts quickly relied heavily on existing toolboxes of account amplification and takeover,” Lerner said.
“Many of these attackers, in fact, could have used tools and services that they found on the underground. Twitter’s new management must recognize that many of the threats observed on the surface–and others about which they might have been unaware–have bubbled up from the deep and dark web.”
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.

