The FBI will feed hacked passwords directly into Have I Been Pwned
Australian security researcher Troy Hunt announced today that he granted the US Federal Bureau of Investigation a direct line to upload new content into Have I Been Pwned, a website that indexes data from security breaches.
The HIBP creator said that when the FBI discovers password collections during their investigations, they will upload the data into a section of the site called Pwned Passwords.
The FBI will provide passwords as SHA-1 and NTLM hashes and not in plain text. No user personal details will be provided, but only the password hashes.
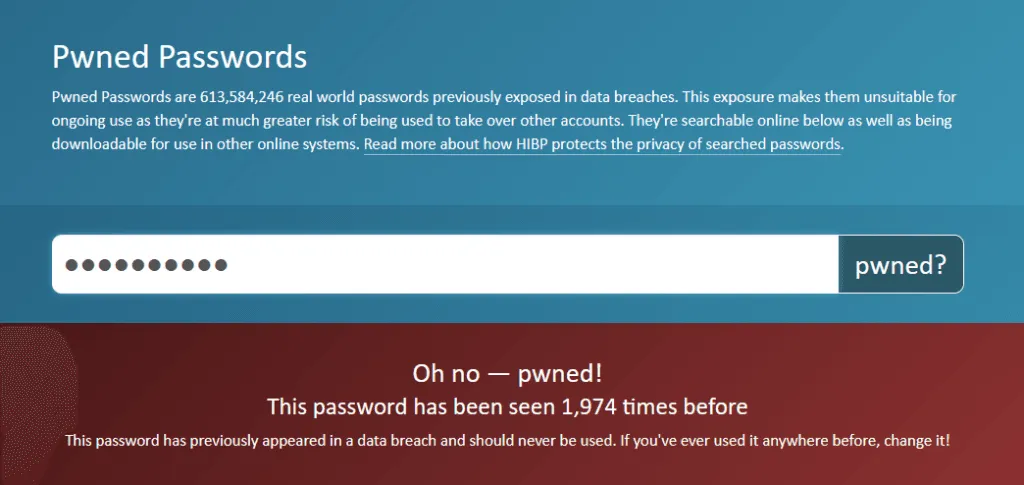
The passwords will be added to Pwned Passwords, a collection of more than 613 million leaked passwords.
While the main HIBP website allows users to search if their emails, names, or usernames have been leaked online in past security breaches, Pwned Passwords is a smaller and more specialized component of the HIBP site that tells users if a password string has ever been leaked online, without attaching the password to any user details.
The idea behind HIBP's Pwned Passwords component is that hackers collect passwords from public breaches and create password dictionaries, which they use to carry out brute-force or credential stuffing attacks.
If users reused the password somewhere else, or if multiple users use the same password, they risk having their accounts hijacked by hackers trying random (previously leaked) passwords.
While most people know Hunt and the HIBP site because of its data breach search functionality, in reality, it's the Pwned Passwords feature that has proven to be more useful and more widely adopted.
Available as a public search, API, and downloadable database, the Pwned Passwords component has been integrated into thousands of public and private applications, where it is used to check if users are using weak or previously leaked passwords, and then prompt users to change their credentials.
Seventeen countries across the world currently use Pwned Passwords to make sure government employees don't use weak or previously leaked passwords.
Until now, the service had been using passwords from data breaches sent to Hunt by security researchers and anonymous tipsters.
The FBI becomes the first official external source to provide data to HIBP's Pwned Passwords.
"We are excited to be partnering with HIBP on this important project to protect victims of online credential theft. It is another example of how important public/private partnerships are in the fight against cybercrime," said Bryan A. Vorndran, Assistant Director, Cyber Division, FBI.
The move comes after Hunt and the FBI collaborated for the first time last month when the FBI shared a list of 4.3 million email addresses collected from the Emotet botnet.
Pwned Passwords code has been open-sourced
The announcement that HIBP has partnered with the FBI also comes on the same day when Hunt open-sourced the code behind the Pwned Passwords component.
In a blog post, Hunt said the two announcements were a pure coincidence and that the FBI did not require Hunt to open-source the HIBP code, a move he first began exploring way back in August 2020.
The code, available on GitHub, will be shepherded by the .NET Foundation, and Hunt said that the code for the main HIBP data breach index would also be open-sourced in the future.
Header image: Troy Hunt
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



