Multi-tasking doctor' was mastermind behind 'Thanos' ransomware builder, DOJ says
A French-Venezuelan physician created the "Thanos" ransomware builder and other tools used by cybercriminals, according to charges unveiled Monday by the Department of Justice.
The criminal complaint, unsealed in a Brooklyn federal court, said 55-year-old Moises Luis Zagala Gonzalez designed several tools to help those interested in creating and propagating ransomware, including software he named Thanos.
Thanos allows users to concoct their own, custom-made malware for locking up victims' files and extorting money from them. Zagala provided extensive guidance on how people can launch ransomware affiliate programs and get the biggest ransom payments from victims, the DOJ said.
The Justice Department said Zagala is a cardiologist living in Ciudad Bolivar, Venezuela.
“As alleged, the multi-tasking doctor treated patients, created and named his cyber tool after death, profited from a global ransomware ecosystem in which he sold the tools for conducting ransomware attacks, trained the attackers about how to extort victims, and then boasted about successful attacks, including by malicious actors associated with the government of Iran,” said U.S. Attorney Breon Peace.
FBI Assistant Director-in-Charge Michael J. Driscoll added that Zagala not only created and sold ransomware products to hackers, but also trained them in how to use it.
Zagala faces up to five years in prison for attempted computer intrusion and another five years for conspiracy to commit computer intrusions.
The FBI said two different informants spoke with Zagala about setting up a ransomware-as-a-service operation. He went by several nicknames — including “Nosophoros,” “Aesculapius” and “Nebuchadnezzar” — while providing support to those buying or renting his ransomware programs.
Thanos had several features that included the ability to create custom ransom notes as well as tools that allowed cybercriminals to choose what data got stolen during attacks. Users could even customize their ransomware with self-delete options and other features to evade detection by security researchers.
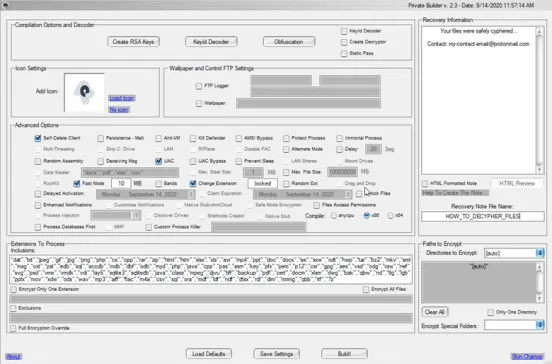
According to the DOJ, users could license the software for periods of time or join an affiliate program and give Zagala a cut of their profits. He allegedly accepted payment in regular currency as well as Monero and bitcoin.
Zagala marketed the program profusely on dark net marketplaces, touting its customizable features and widespread adoption among cybercriminals and nation-state actors, the DOJ said.
An informant told the FBI that Zagala provided a detailed tutorial on how to create an affiliate network, noting that he himself generally had crews ranging between 10-20 members and sometimes as low as 5.
Hackers often came to him after they had already broken into a company, according to the complaint. Zagala would check the access they came with and then allow them to deploy the ransomware.
“They come with access to [b]ig LAN, I check and then I accept[.] they lock several big networks and we wait … If you lock networks without tape or cloud (backups)[,] almost all pay[.],” he allegedly told the informant in October 2020.
He also offered advice, noting that companies with backups could still be hurt through data exfiltration and that he had helpers who could encrypt backups as well.
Zagala’s products were well-regarded among cybercriminals, and the Justice Department said it found several reviews for his products that touted their effectiveness.
One reviewer said they used Zagala’s products to “infect a network of approximately 3000 computers” and another said it has the “best support.” In one forum, Zagala linked to a news story about Iranian state actors using Thanos to attack companies in Israel.
He frequently switched usernames and screen names, telling one FBI informant in November 2021 that he had to because “malware analysts are all over me.”
On May 3, FBI agents spoke with one of Zagala’s relatives in Florida who confirmed information tying him to the ransomware operation.
In addition to creating Thanos, Zagala is accused of creating a ransomware tool called “Jigsaw v. 2,” that allowed users to track how many times victims tried to remove the malware.
“If the user kills the ransomware too many times, then it's clear he won’t pay so better erase the whole hard drive,” Zagala wrote according to the DOJ. It had features that allowed the ransomware to delete 1,000 files as punishment if the victim rebooted their system.
In 2019, Emsisoft released a decryptor for the Jigsaw ransomware.
Researchers have long noted that the several popular ransomware strains were based on Thanos, including Prometheus and Haron.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.

