New Haron ransomware gang emerges, borrows from Avaddon and Thanos
Malware analysts from South Korean security firm S2W Labs have discovered a new ransomware operation that launched in the cybercrime ecosystem this month that heavily borrows from past ransomware operations such as Thanos and the now-defunct Avaddon.
Named Haron, the first samples linked to this gang have been spotted earlier this month.
Just like the vast majority of ransomware operations today, the Haron gang goes after enterprise targets in order to maximize its profits and also runs a "leak site" where it threatens to publish data stolen from companies who refuse to pay for decrypting their files.
But while Haron uses the same tactics used by more advanced ransomware families, S2W researchers say that under the hood, Haron is more of an amateurish Frankenstein, being built around code copied from other ransomware gangs.
These similarities include:
- Using a leaked builder for the old Thanos ransomware to create the final Haron ransomware binary.
- The website where victims are told to go negotiate and pay the ransom (the "payment site") is nearly similar to the one run by the former Avaddon gang.
- The leak site is also almost identical to Avaddon's site.
- The Haron gang's ransom note contains large portions of text copy-pasted from the Avaddon note.
- The Haron web server also contained icons and images that were previously found on the official Avaddon site.
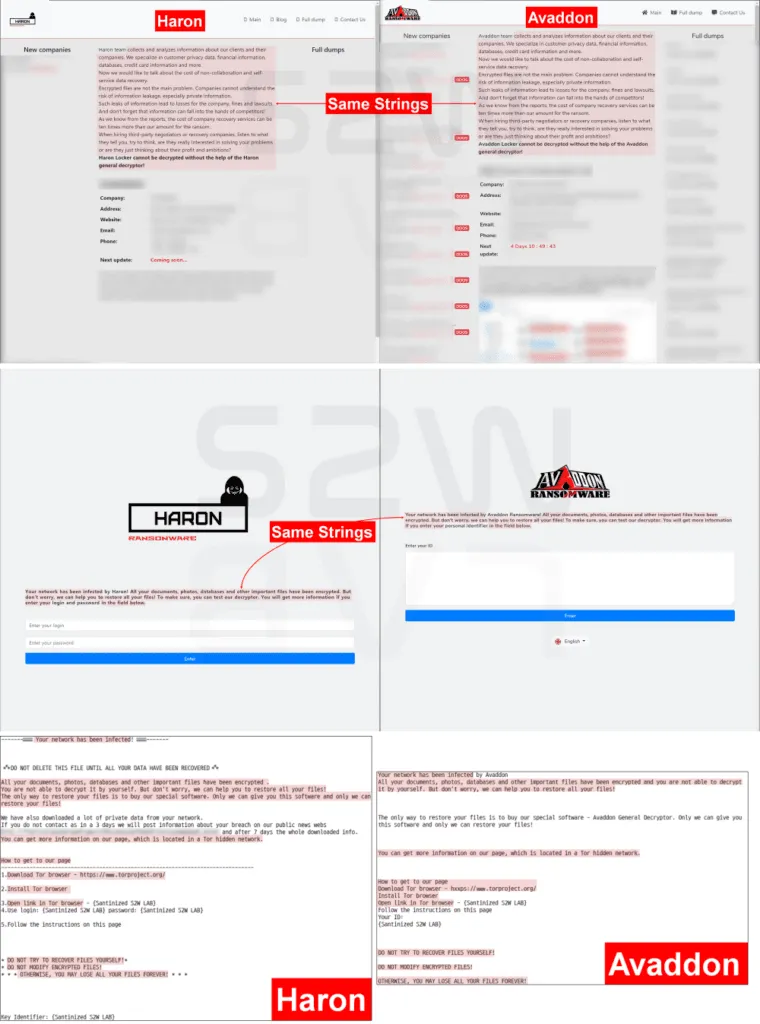
All of these suggest that the Haron gang had direct access to some parts of Avaddon's operation.
However, it is unclear how this happened. It is unclear if the Haron gang purchased these items from the Avaddon gang directly or if they hired one of Avaddon's former members, most likely the person responsible for the gang's web-facing applications, such as Avaddon's payment and leak sites.
But as S2W researchers point out, while the Haron gang had incorporated Avaddon's web-based systems into its operations, they did not have access to the Avaddon ransomware source code.
Written in C++, the original Avaddon ransomware was an advanced ransomware strain, something superior to the C# codebase of the Thanos strain, also used by the Prometheus ransomware group.
Looks like we have new cyber bad guys here:
— The Brofessor (@Glacius_) July 19, 2021
- Haron Ransomware
- They create a dedicated group to talk with the victim (company member or middle man)
- Try to disable Raccine (cc @cyb3rops )
- Command lines details here: https://t.co/yltXMh2cxA
(cc @malwrhunterteam @circl_lu ) pic.twitter.com/keCezERFFq
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



