Texas hospital still bringing systems back online after Sept 1 ransomware attack
Oakbend Medical Center is still in the process of restoring its systems after a ransomware attack crippled their digital services starting on September 1.
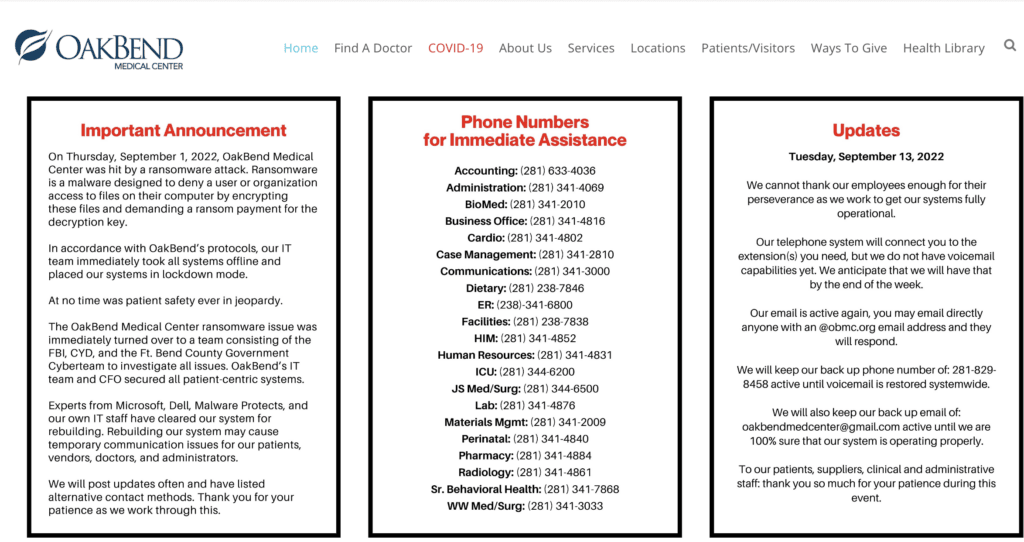
In a statement on Tuesday, the Richmond, Texas hospital said its phone system was still having issues related to voicemail services but explained that its email platform is now back up and running. The statement says the phone services are slated to be fully back to normal by the end of the week.
Ivan Shulman, interim marketing director for OakBend Medical Center, told The Record that as of Tuesday, the FBI and the Fort Bend County Cyber Crimes Unit are handling the ransomware attack.
"The hospital is restoring systems and focused on patient care. OakBend has not been made aware of any patient data that has been compromised but is prepared to act immediately if informed by the above authorities," Shulman said.
The hospital said on September 1 that its IT team took all systems offline following the ransomware attack.
"At no time was patient safety ever in jeopardy. The OakBend Medical Center ransomware issue was immediately turned over to a team consisting of the FBI, CYD and the Ft. Bend County Government Cyberteam to investigate all issues,” the hospital said in its first statement.
“Oakbend's IT team and CFO secured all patient-centric systems. Experts from Microsoft, Dell, Malware Protects and our own IT staff have cleared our system for rebuilding. Rebuilding our system may cause temporary communication issues for our patients, vendors, doctors, and administrators.”
Ft. Bend County Government and other Texas cybersecurity agencies did not respond to requests for comment about the incident.
The Daixin ransomware group took credit for the attack, posting the hospital to its leak site this week and claiming to have stolen more than 1 million records with patient and employee data.
The gang claimed the databases included Social Security Numbers and other information, openly threatening to use the data for a variety of crimes.
Representatives for Daixin contacted DataBreaches.net and said it stole 3.5 GB of data and shared a list of 258 directors it obtained during the attack. The gang shared samples of the patient data it stole that included troves of sensitive healthcare information.
OakBend Medical Hospital data leak includes employee PII.
— Dominic Alvieri (@AlvieriD) September 13, 2022
Password file found exposed the same short easily guessed password used on 33% (3 of 9) sensitive accounts listed.
40,000 annual emergency room visits or about 109 ER visits per day have been disrupted by Daixin @FBI https://t.co/m3XlFE53Aq pic.twitter.com/iOtBm6dZZ3
A representative for OakBend Medical Center did not respond to requests for comment about whether data had been stolen or if a ransom will be paid.
OakBend Medical Center says it is "the last remaining independent nonprofit hospital in the Greater Houston Area" and has about 450 physicians on staff. It handles about 40,000 emergency room visits a year and 100,000 annual outpatients.
The ransomware group emerged in June and has only publicly claimed three victims: Oakbend Medical Center, Fitzgibbon Hospital in Missouri and a German company called Ista International.
The incident comes just weeks after the LockBit gang launched a crippling attack on a hospital about an hour south-east of Paris which disrupted its medical imaging, patient admissions, and other services.
The United Kingdom’s National Health Service is still struggling to cope with a ransomware attack on an IT provider this summer.
Several NHS departments faced outages, according to The Guardian. Services like dispatches for ambulances, referrals for patients, appointment bookings, prescriptions and more were impacted by the ransomware attack. Officials told staff members that it will take weeks for the system to be restored.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



