SVR cyberspies used iOS zero-day in recent phishing campaign
The Russian hacking group that breached software provider SolarWinds in an infamous supply chain attack last year has returned to its regular skullduggery and, for the past few months, has conducted a massive spear-phishing operation aimed at government agencies, think tanks, consultants, and NGOs.
Tracked as APT29 or Cozy Bear, the group has been linked by White House officials to the SVR, the Russian Foreign Intelligence Service.
In reports published on Thursday by Microsoft and security firm Volexity, the two companies said the SVR hackers breached a Constant Contact marketing account belonging to USAID, a US government agency that provides help to foreign organizations.
APT29 took control over the Constant Contact account and used it to send around 3,000 booby-trapped emails to more than 150 organizations across 24 countries.
In the vast majority of emails, the hackers sent links to victims that redirected them to websites that used JavaScript code to drop a malicious ISO image file on their computers.
If users opened the image file, a backdoor (Cobalt Strike beacon) would be installed on their systems that would ping the hackers in case of a successful compromise.
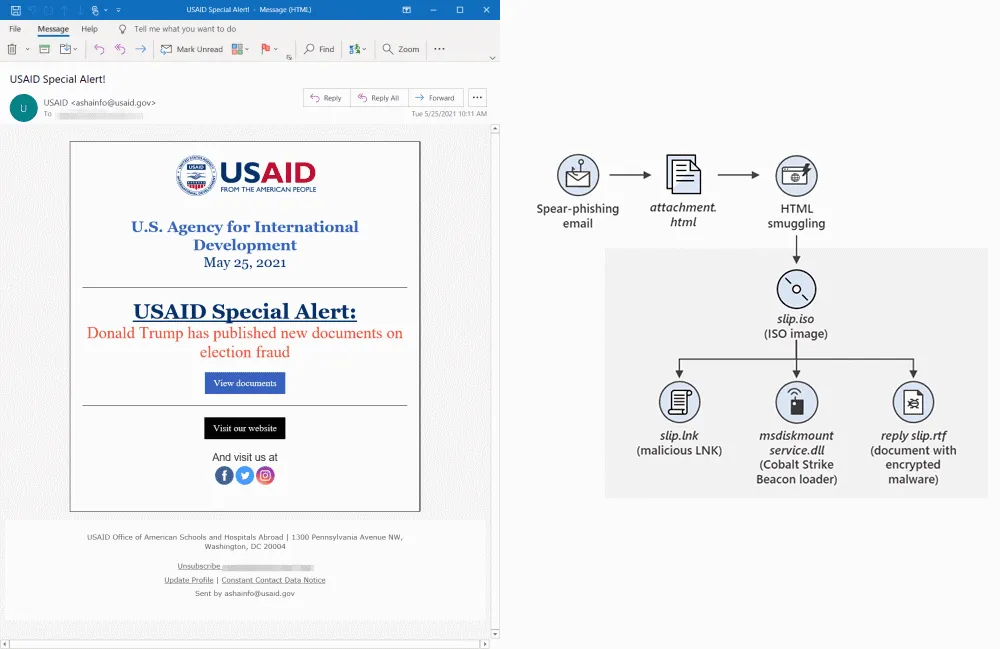
But while using ISO files as a malware delivery system is quite rare, APT29 conducting spear-phishing attacks is not and has been their main modus operandi for the past decade.
What was notable of the recent attacks was that in particular cases, the hackers filtered incoming users and directed iOS users to a special page where they deployed a Safari iOS zero-day bug to infect victims' devices.
Tracked as CVE-2021-1879, Apple patched the zero-day in March after receiving an alert from Google's Threat Analysis Group. It is unclear if Google detected the same attacks, or the zero-day was used in a different campaign and then also reused by APT29.
The recent APT29 attacks were discovered because the group abandoned the stealthy approach they had been using for months and launched a massive spear-phishing campaign on May 25, consisting of thousands of emails per day, which exposed their operations, according to Microsoft.
My favorite part(s) are actually the months of testing/refinement leading up to the broad campaign
— Christopher Glyer (@cglyer) May 28, 2021
Jan: Firebase URL tracking user clicks - no payload
Feb: Firebase URL (tracking enabled) hosted ISO
Feb/Mar:
HTML -> ISO -> LNK -> CS
HTML -> ISO -> RTF -> CS
URL -> ISO -> …
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



