Ransomware tracker: Schools, hospitals face a surge in attacks
After experiencing a brief dip at the beginning of the year, ransomware attacks are showing signs of a resurgence with some sectors disclosing incidents at record rates.
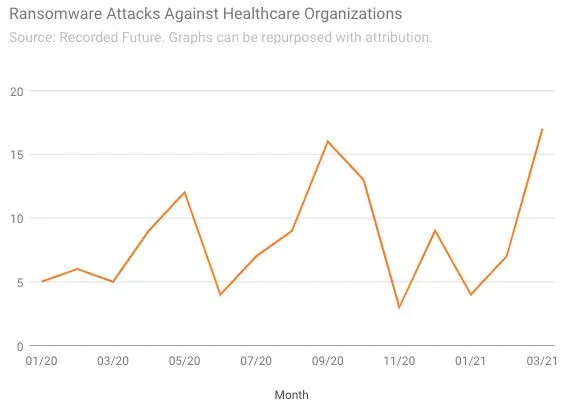
Healthcare organizations and schools, for example, both reported in March a surge in ransomware attacks that surpassed all-time highs set last September. There were 17 hospitals, healthcare systems, and clinics that disclosed ransomware attacks last month, up from 7 in February and 5 in March 2020, according to an analysis from Recorded Future that uses data from government agencies, news reports, hacking forums, and other sources.
Healthcare organizations have been hit hard during the pandemic, in part because ransomware operators see these institutions as especially vulnerable targets that might be more willing to pay to restore their services. However, it’s unclear why there was an uptick in March—the reported incidents targeted a wide variety of health organizations across the country, in states including Kentucky, Arizona, Idaho, New York, and Texas, suggesting that they could be unrelated.
Schools under attack
School systems also reported a record number of ransomware incidents in March—there were 13 such incidents last month, which compares to 7 in February and 5 in March 2020. Unlike healthcare organizations, there are two explanations that help explain the surge in attacks on education systems: After a string of successes in the U.S., ransomware groups seem to be taking their playbook overseas, and many universities have also been exposed to ransomware due to vulnerabilities in a firewall vendor’s networking equipment.
“School systems have been under constant attack, but we’re really seeing it take off in countries like the U.K.,” said Allan Liska, a ransomware expert at Recorded Future who is involved in the analysis. “There does seem to be this model where ransomware actors have figured out that school systems are a good target so they go after the ones in different countries.”
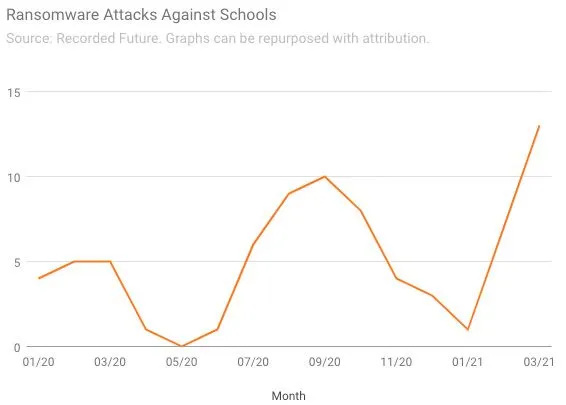
In the U.K., schools across Nottinghamshire had to shut down their IT networks at the beginning of March after a central trust that manages their systems was hit by ransomware. South and City College Birmingham closed all eight of its campuses to students for a week, while Cambridge Meridian Academies reported a ransomware attack to the government that occurred on March 12. Most recently, London’s biggest school trust—a network of 48 schools that educates 36,000 children a year—was hit by a ransomware attack that brought down its IT systems.
Additionally, many colleges and universities in the U.S. have been caught up in the Accellion-related cyberattack, in which hackers exploited a vulnerability in the firewall vendor’s File Transfer Appliance. The University of California system, the University of Miami, Stanford University, and others reported last month that they were being targeted by the Clop ransomware gang in connection with the breach.
Another bad sign for schools is that ransomware operators appear to be getting more brazen with their demands. Last month, hackers who breached Broward County Public Schools in Florida—the sixth largest school district in the nation—demanded a whopping $40 million to decrypt the data and threatened to release sensitive information if the ransom wasn’t paid.
Ransomware extortion sites see a dip
Although ransomware attacks appear to be surging across several industries, one potential bright spot in March is ransomware extortion sites, which saw a significant drop in activity. These sites have become increasingly popular over the last year among ransomware groups, which use them to leak portions of victim data to pressure their targets to pay ransom demands. But in March, only 89 victims had their data exposed on these sites tracked by Recorded Future, down from 189 in February and the peak of 283 in December 2020.
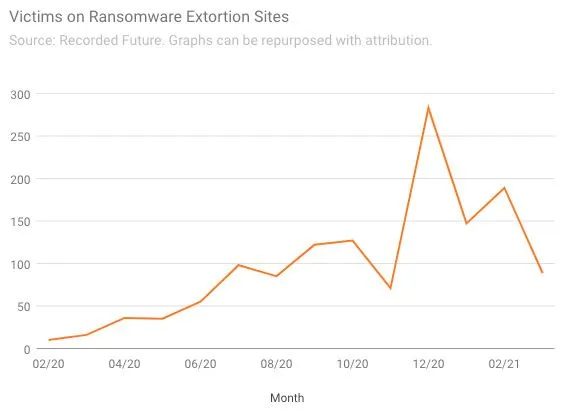
Liska says much of the decline can be traced to recent law enforcement actions against extortion groups, which have caused reverberations throughout the ransomware ecosystem.
“What you’re seeing is a scrambling—ransomware affiliates that want to stay in the game are trying to set up with new groups, but that takes time,” Liska said. “The reshuffling causes some delay in the extortion.”
Department of Homeland Security Secretary Alejandro Mayorkas said in a talk at the end of last month that his department would be focusing on combating ransomware, and made it a priority in a newly-announced cybersecurity “sprint” that will look at ways to curb ransomware groups. If disruption efforts continue, it could act as a meaningful deterrence, Liska said.
Additionally, the dip in ransomware extortion site activity could be partly attributed to old-fashioned infrastructure issues: Several extortion sites have experienced glitches, which could be preventing operators from updating them regularly. “I know it’s hard to believe that if your infrastructure is held together with baling wire and duct tape it would go down... but we’ve seen sites go down for a week or more recently,” he said.
The Record by Recorded Future allows outside organizations to share and distribute graphs from this ongoing project with proper attribution.
Adam Janofsky
is the founding editor-in-chief of The Record from Recorded Future News. He previously was the cybersecurity and privacy reporter for Protocol, and prior to that covered cybersecurity, AI, and other emerging technology for The Wall Street Journal.



