The return of ICEFALL: Two critical bugs revealed in Schneider Electric tech
Researchers have announced two critical vulnerabilities in some operational technology systems made by the digital automation giant Schneider Electric.
The announcement comes just months after researchers at Forescout and the U.S. Cybersecurity and Infrastructure Agency (CISA) disclosed some 56 bugs affecting a roster of industrial technology companies including among others, Siemens, Motorola, and Honeywell. The discoveries were known collectively as “ICEFALL.”
Schneider had asked the researchers to refrain from including the two bugs in the ICEFALL list so it could work with customers to remedy the issues before they were announced publicly. The two vulnerabilities — CVE-2022-45788 and CVE-2022-45789 — affect the Unity line of Schneider's Modicon programmable logic controllers (PLCs).
PLCs are in everything from traffic lights to elevators to critical infrastructure, and Schneider PLCs run in systems like water and wastewater processing systems, mining, manufacturing and energy production.
Daniel dos Santos, head of security research at Forescout, and security researcher Jos Wetzels told The Record that the vulnerabilities could be chained together and give cybercriminals and adversaries access to safety mechanisms that usually would help limit the physical damage that could come from a hack. Dos Santos and Wetzels said this isn't a contingency that industrial companies typically plan for.
This isn't just hypothetical. Back in 2021, someone hacked into a Florida water treatment plant and tried to raised the levels of lye in the drinking water. While workers at the plant managed to stop the incident, they noted that there are safeguards which would recognize that the levels were not supposed to be that high or low and automatically stop the change.
The initial ICEFALL announcement alarmed cybersecurity experts because it made clear that industrial tools may be insecure by design and when vulnerabilities are discovered, customers often don't know about them.
Dos Santos and his team were also startled by the fact that 74% of the product families affected by ICEFALL had some form of third party security certification, which suggests a problem there, too. They worried about “limited scope for evaluations, opaque security definitions and a focus on functional testing.”
Fundamental tech
Dos Santos told The Record that the Modicon family of PLCs is one of the most popular in the world and can be traced back to 1968, when the Modicon 084 was the first commercially produced PLC.
Since that time, Schneider Electric has become one of the largest sellers of PLCs. The prevalence of those products showed up in a basic search that Forescout performed on Shodan, an internet scanning tool. The search shows dozens of internet-connected PLCs — despite the fact that security experts discourage connecting them to the internet.
Forescout found that France (33%), Spain (17%), Italy (15%), and the United States (6%) are the countries with the most exposed devices. By querying Shodan for all relevant Modicon Unity models, the researchers found more than 1,000 exposed PLCs.
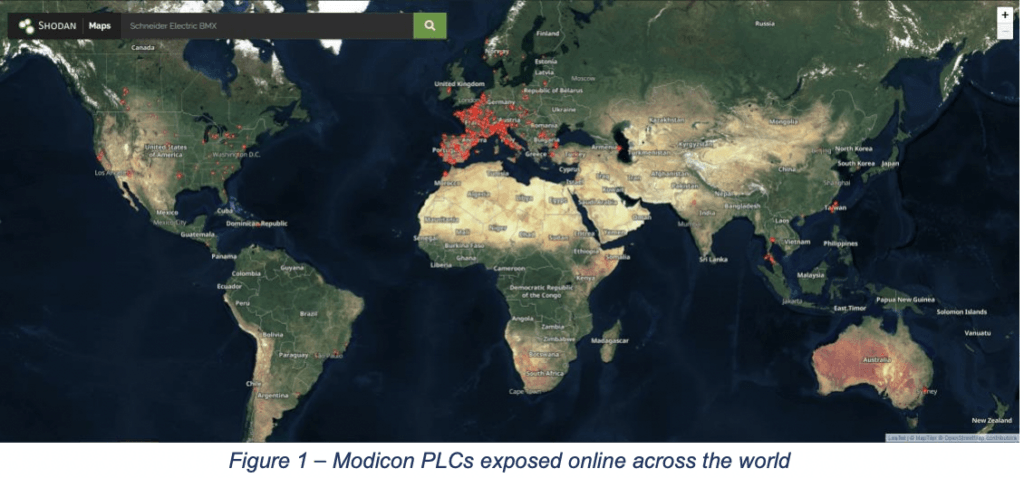
“A quick search for the affected models on Shodan has shown exposed Modicon PLCs in everything from airports, mining, and solar and hydro power generation to chemical manufacturing,” dos Santos and Wetzels said.
They found one Modicon PLC used by an Italian crushing plant used in mining operations and several others used by small power generation facilities. They were able to map nearly 30 exposed devices to real-world critical infrastructure organizations through simple searches that would be dwarfed by the capabilities of a powerful nation-state or military.
About half of the exposed devices in the power industry were connected to one system integrator in a European country that was responsible for a series of solar power parks. Several were found at hydroelectric power plants in the U.S. and dozens of others were in manufacturing organizations in the chemical sector.
Forescout said it disclosed CVE-2022-45788 and CVE-2022-45789 to Schneider Electric in April and July 2022.
In a statement to The Record, a Schneider Electric spokesperson said the company worked closely with Forescout throughout the disclosure process and published two security notifications last month.
“We recommend customers apply those mitigations. We recommend customers implement cybersecurity best practices across their operations as outlined in the Schneider Electric Recommended Cybersecurity Best Practices document,” a spokesperson said.
The bigger picture
Both dos Santos and Wetzels told The Record that the bugs were just one example of how similar vulnerabilities could be used by attackers to move laterally between different network segments and types of networks at the most basic level.
Hackers — in this case most likely from nation-states or militaries — could use bugs like this to bypass functional and safety constraints that would otherwise prohibit cyber-physical attacks with the most serious consequences, Wetzels and dos Santos said.
PLCs — like those used to raise or lower bridges and start or stop pumps — can be taken over by hackers, as illustrated in the advisories for CVE-2022-45788 and CVE-2022-45789.
But typically measures are in place to make sure that a bridge can only be lowered at a certain speed or a pump can be told to operate in a certain way.
“So as an attacker, I need to bypass these functional limits and that means I need to move very deeply into that system. And what typically happens is that in more complex production environments, you have a top-level PLC and behind that, there will be a network of 10 other PLCs, each of which controls something,” Wetzels explained.
“If I'm only able to talk to the PLC at the top level, I cannot tell each of these devices what to do. What we're showing in this report is that if I am able to first hack the top-level PLC and then jump from that PLC to the other PLCs behind it, then I have very detailed control over all the aspects of this infrastructural facility and then it becomes possible to achieve certain cyber-physical effects that otherwise might have been impossible.”
Wetzels and dos Santos said the goal of their report was to get critical infrastructure organizations to do more consequence-driven risk assessments and think deeper about how an attacker might be able to bypass safety measures put in place to protect physical environments.
Many companies, they explained, assume their safety measures cannot be bypassed and operate as if there would be no way for someone — in the example they used — to ostensibly raise or drop a bridge fast enough to cause actual damage.
Using CVE-2022-45788 and CVE-2022-45789 as an example, the two researchers showed that if an attacker can chain vulnerabilities together, they can hack the safety systems nested behind PLCs and get deep into a system.
The report notes that in recent years, particularly since the onset of Russia’s invasion of Ukraine, there have been several instances where malware like TRITON and INCONTROLLER have illustrated that real-world threat actors are both capable of and interested in developing such capabilities.
While most industrial malware is currently focused on stealth and persistence, the researchers warned of what could happen when physical impact is sought.
“This is advanced stuff. This is not your average script kitty stuff, but it is something you should take into account as a possibility when you're designing new system architectures,” Wetzels said.
“When you're evaluating your potential risk, you have to think about whether you can defend against this and if you have the visibility deep down in your systems.”
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



