Russian hackers target European hospitality industry with ‘blue screen of death’ malware
Suspected Russian cybercriminals are using a fake “Blue Screen of Death” page to target European hotels and hospitality companies with malware.
Researchers from Securonix said they have been tracking an ongoing malware campaign they call PHALT#BLYX, which typically starts with a lure centered around hospitality search engines.
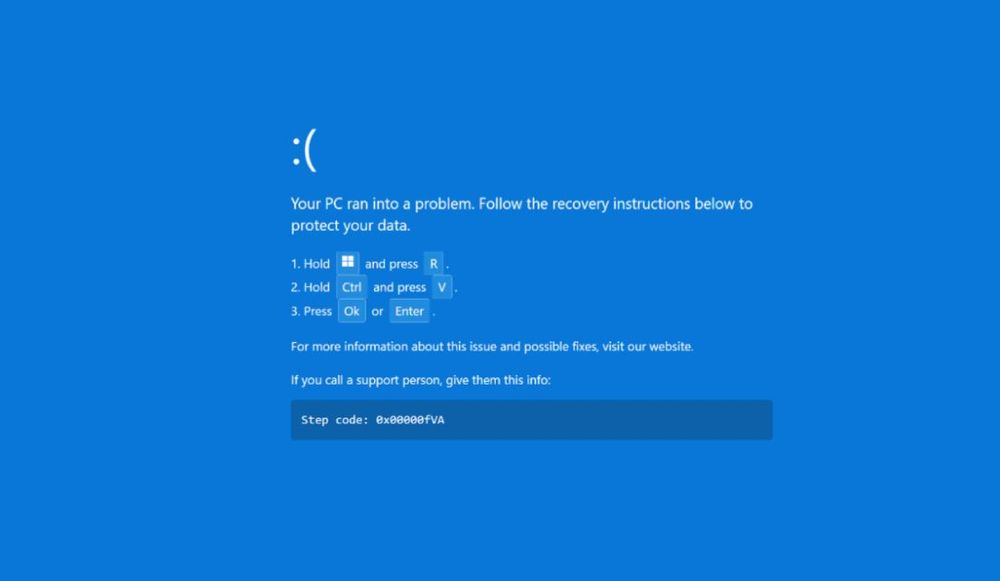
The scheme starts with a fake reservation cancellation that impersonates a popular booking site, and eventually prompts victims with an error message and “Blue Screen of Death” page.
In order to get out of the page, victims are asked to take a series of actions that eventually lead to the download of a strain of malware called DCRat, which enables threat actors to track a victim's key strokes and take other actions on an infected device.
Securonix said the campaign is yet another version of the “ClickFix” technique where hackers try to take advantage of human problem-solving tendencies by displaying fake error messages or prompts that instruct target users to fix issues by copying, pasting and launching commands that eventually result in the download of malware.
Shikha Sangwan, senior threat researcher at Securonix, said that there are several indicators suggesting Russian connection, including the use of MS Build project files containing native Russian debug strings and commands.
Additionally, technical telemetry showed that infrastructure and other tools used by the group were geolocated to Russia. DCRat is sold widely within Russian underground forums.
‘Reservation cancellation’
Securonix said the hackers were targeting the hospitality sector throughout the fall because it is one of the busiest times of the year for the industry.
The phishing emails, most of which are titled “Reservation Cancellation,” featured room charge details in Euros, indicating they intended to target European hotels, hostels and inns. The emails prominently feature charges over €1,000 ($1,170) to create a sense of urgency and panic, the researchers said.
The emails have a “See Details” button that takes them to a fake hotel booking page with the fake browser error message stating, “Loading is taking too long.” The error message includes a prominent “Refresh page” button that when clicked, takes a victim to the fake “Blue Screen of Death.”
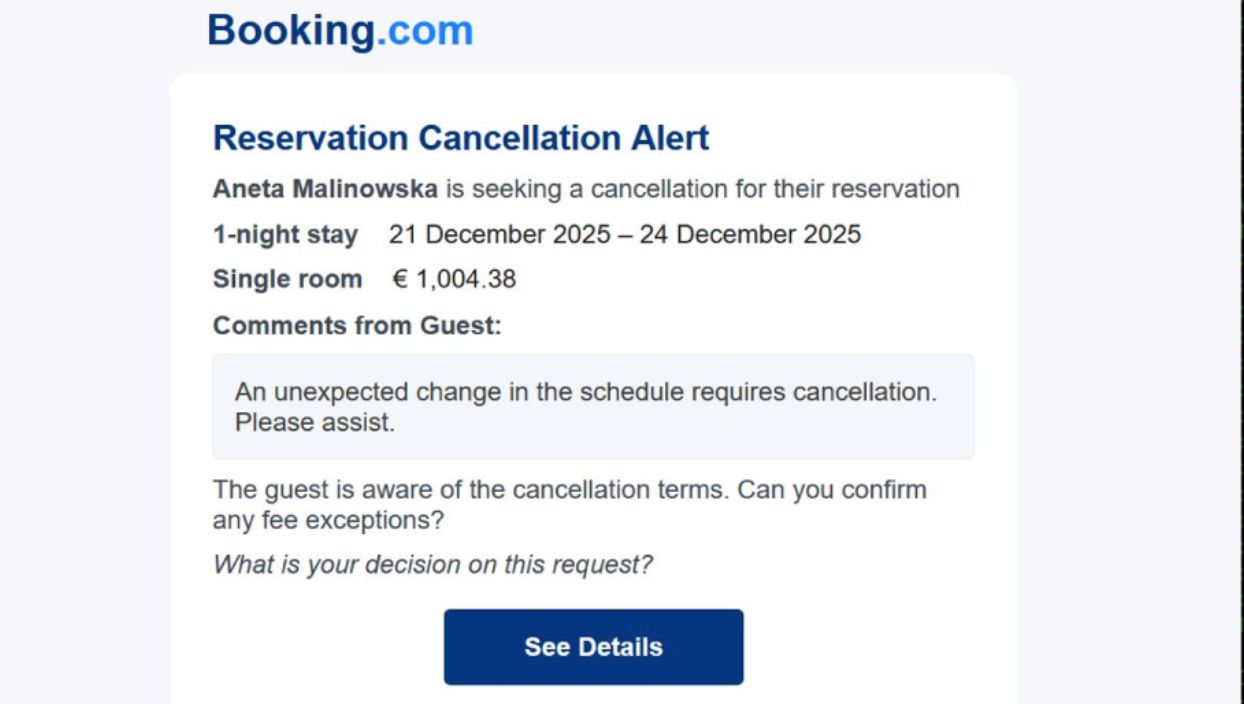
An example of a fake cancellation alert. Image: Securonix
Once a victim sees the fake “Blue Screen of Death” animation, they are directed to fix the issue by pasting a malicious script into the Windows Run dialog.
The pasted script sets off a chain of events that enables the malware to disable Windows Defender. As a decoy, a real booking page is opened while the malware works in the background.
The malware then takes a series of actions including disabling defenses, stealthily downloading other tools and allowing the hackers to maintain their access to the device. The malware steals passwords, clipboard data and other information.
Securonix warned that the campaign “represents a sophisticated evolution in commodity malware delivery.”
“The psychological manipulation, combined with the abuse of trusted system binaries like 'MSBuild.exe', allows the infection to establish a foothold deep within the victim’s system before traditional defenses can react,” the researchers said.
“The technical complexity of the infection chain reveals a clear intent to evade detection and maintain long-term persistence.”
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.