REvil gang asks for $70 million to decrypt systems locked in Kaseya attack
The REvil ransomware gang is asking for a $70 million ransom payment to publish a universal decryptor that can unlock all computers locked during the Kaseya incident that took place this past Friday, The Record has learned.
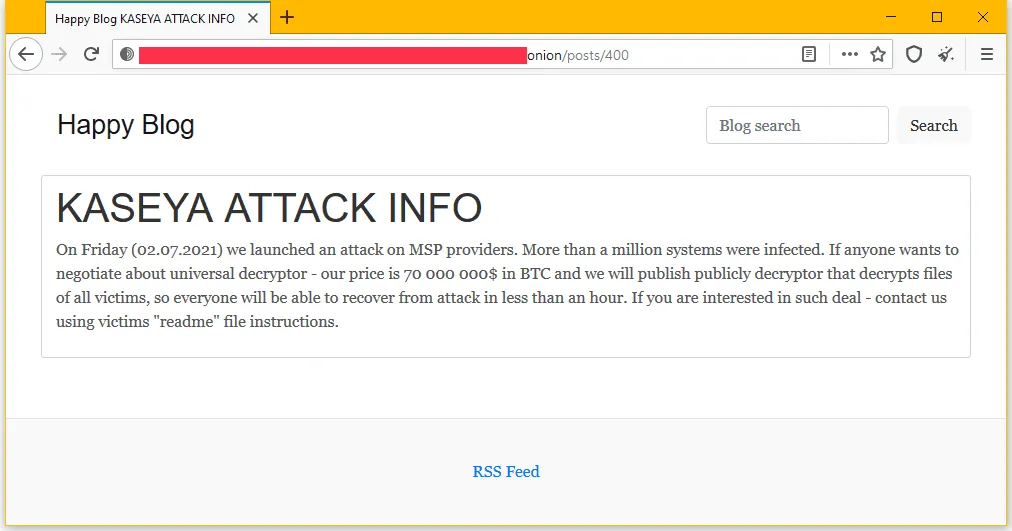
In a message posted on their dark web blog, the REvil gang officially took credit for the attack for the first time and claimed they locked more than one million systems during the Kaseya incident.
On Friday (02.07.2021) we launched an attack on MSP providers. More than a million systems were infected. If anyone wants to negotiate about universal decryptor - our price is 70 000 000$ in BTC and we will publish publicly decryptor that decrypts files of all victims, so everyone will be able to recover from attack in less than an hour. If you are interested in such deal - contact us using victims "readme" file instructions.
If honored, the demand would become the highest ransomware payment ever made.
A Kaseya spokesperson was not on hand to comment if the company would be considering paying the REvil gang's ransom demand.
At the time of writing, the Kaseya ransomware incident is believed to have impacted thousands of companies across the world.
The attack took place on late Friday afternoon, just before the extended July 4 US weekend, when the REvil gang (or one of its collaborators) is believed to have used an exploit in the Kaseya VSA server to gain access to VSA appliances installed on customer premises.
VSA appliances are web-based platforms typically used by large corporations or managed service providers (MSPs) to manage remote computer fleets.
The REvil gang pivoted from the compromised VSA servers to all connected workstations and corporate networks to install their payload and encrypt customer files in one of the largest ransomware outbreaks in recent years.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



