Researchers uncover vast cyberespionage operation targeting dozens of governments worldwide
A cyberespionage group based in Asia breached the systems of 37 governments and conducted reconnaissance in 155 countries, according to a new report from Palo Alto Networks.
Pete Renals, director of National Security Programs for the company's Unit 42, declined to attribute the campaign to a specific country but said the attacks stood out because of how widespread they are.
“When we look at the scale here, we're making an argument that this is probably the most widespread and significant compromise of global government infrastructure by a state-sponsored group since SolarWinds,” Renals told Recorded Future News.
Unit 42 tracked the compromise of at least 70 institutions across the 37 countries — with the hackers maintaining access to some victims for months. In one country, the hackers gained access to the parliament and a senior elected official.
The group successfully breached national telecommunications companies, police agencies, counterterrorism departments and many ministries and departments of interior, foreign affairs, finance, trade, economy, immigration, mining, justice and energy.
The company said that while the campaign is largely focused on espionage and data theft, its “methods, targets and scale of operations are alarming, with potential long-term consequences for national security and key services.”
Renals compared the effort to recent Chinese campaigns like Volt Typhoon and Salt Typhoon but noted that both of those efforts were focused on specific industries within certain countries.
Renals noted that several of the breaches came around newsworthy incidents, including a cyberattack on a Venezuelan institution following the U.S. operation that removed former President Nicolás Maduro.
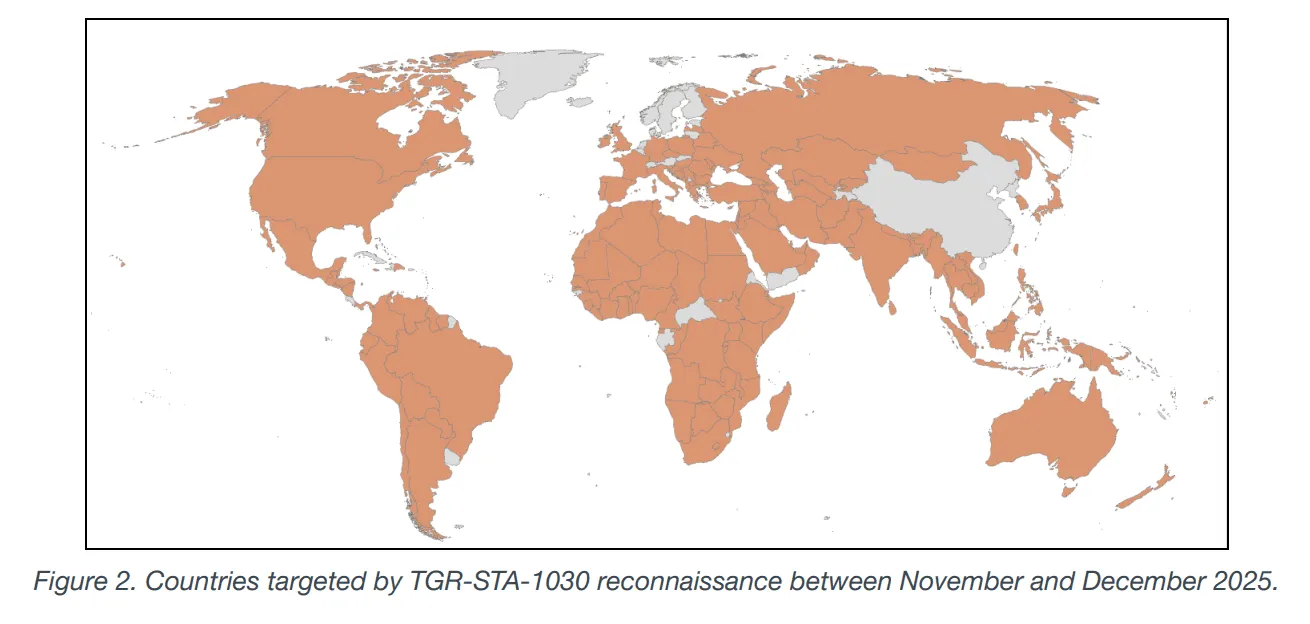
Image: Palo Alto
Diaoyu
Unit 42 researchers first discovered the campaign when it was investigating a series of phishing attacks that targeted European governments in early 2025. Further research led them to infrastructure that dates back to January 2024.
The company determined the group behind the campaign was based in Asia due to regional tools, language settings, connections to operational infrastructure based in the region and activity that aligned with the time zone or events that would be of interest to the region.
The string of phishing campaigns targeting European governments followed a similar pattern, with most involving malicious emails sent to government addresses. In one example, an Estonian official was targeted with an email that contained a zip file focused on police and border guards.
Metadata shows the file was previously named “Diaoyu” — the Chinese word for fishing or phishing in a cybersecurity context. The malware performs a series of actions that ultimately result in the installation of a Cobalt Strike payload — which is typically used by hackers to gain a foothold in a victim’s system.
In addition to the phishing campaigns, Unit 42 found that the hackers used an array of tools, exploitation kits and proof-of-concept code for vulnerabilities in products used in many regions.
Renals said they did not find any specific focus on software or hardware, with the hackers adapting to whatever the target environment was using.
“The list has been variable, from an endpoint product standpoint, depending on who they're targeting — it may be more of a European flavor versus more of an African flavor versus more of an Asian flavor,” he said.
Following the news
Unit 42 saw direct ties between certain attacks and current events. During the U.S. government shutdown in October 2025, the group shifted its scanning to organizations across North, Central and South American countries, including Brazil, Canada, Dominican Republic, Guatemala, Honduras, Jamaica, Mexico, Panama and Trinidad and Tobago.
The hackers compromised the network of a Bolivian mining entity tied to rare earth minerals — a key issue in the country’s recent presidential election. The hackers also breached Brazil’s Ministry of Mines and Energy, which has the second largest supply of rare earth mineral reserves in the world.
One day after the U.S. captured Venezuela’s president in Operation Absolute Resolve, the hackers conducted extensive reconnaissance activities targeting at least 140 Venezuelan government-owned IP addresses.
Dozens of other attacks aligned with regional hot-button issues. The hackers compromised European government agencies in Germany, Czechia, Cyprus, Greece as well as countries centered around the South China Sea, including Thailand and Vietnam.
Renals said they have been successful over the last few weeks in pushing the actors out of a subset of impacted government networks. Their goal is to watch how the hackers respond and try to regain their access going forward.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.
Martin Matishak
is the senior cybersecurity reporter for The Record. Prior to joining Recorded Future News in 2021, he spent more than five years at Politico, where he covered digital and national security developments across Capitol Hill, the Pentagon and the U.S. intelligence community. He previously was a reporter at The Hill, National Journal Group and Inside Washington Publishers.




