Don’t focus on ransomware variants, say UK’s national cyber and crime agencies
Britain’s National Cyber Security Centre (NCSC) and National Crime Agency (NCA) published a joint report on Monday detailing the ways in which the ransomware ecosystem is increasingly professionalizing “in a bid to gain efficiencies and maximize profits.”
The agencies are pushing back against what they say are frequent challenges over how they are handling individual ransomware variants.
Doing so “is akin to treating the symptoms of an illness, and is of limited use unless the underlying disease is addressed,” argue the agencies, adding that taking “a more holistic view by understanding the elements of the wider ecosystem allows us to better target the threat actors further upstream.”
The paper examines the entire attack path of the cybercriminal system, from the initial access vectors through to exploiting that access and then to deploy ransomware through to attempting to monetise it and then convert the cryptocurrency payment into hard cash.
“Our joint report reveals the complexities of the cybercrime ecosystem, with its different platforms, affiliates, enabling services and distributors, which all contribute to the devastating outcomes of ransomware attacks on the UK’s organizations,” said the NCSC’s chief executive Lindy Cameron.
“The deployment of ransomware attacks relies on a complex supply chain, so focussing on specific ransomware strains can be confusing at best, and unhelpful at worst,” said Cameron, adding that the white paper was intended to shine a light on “the motivations of the threat actors further upstream, who are ultimately driving the monetisation of ransomware as a service, and other extortion attacks.”
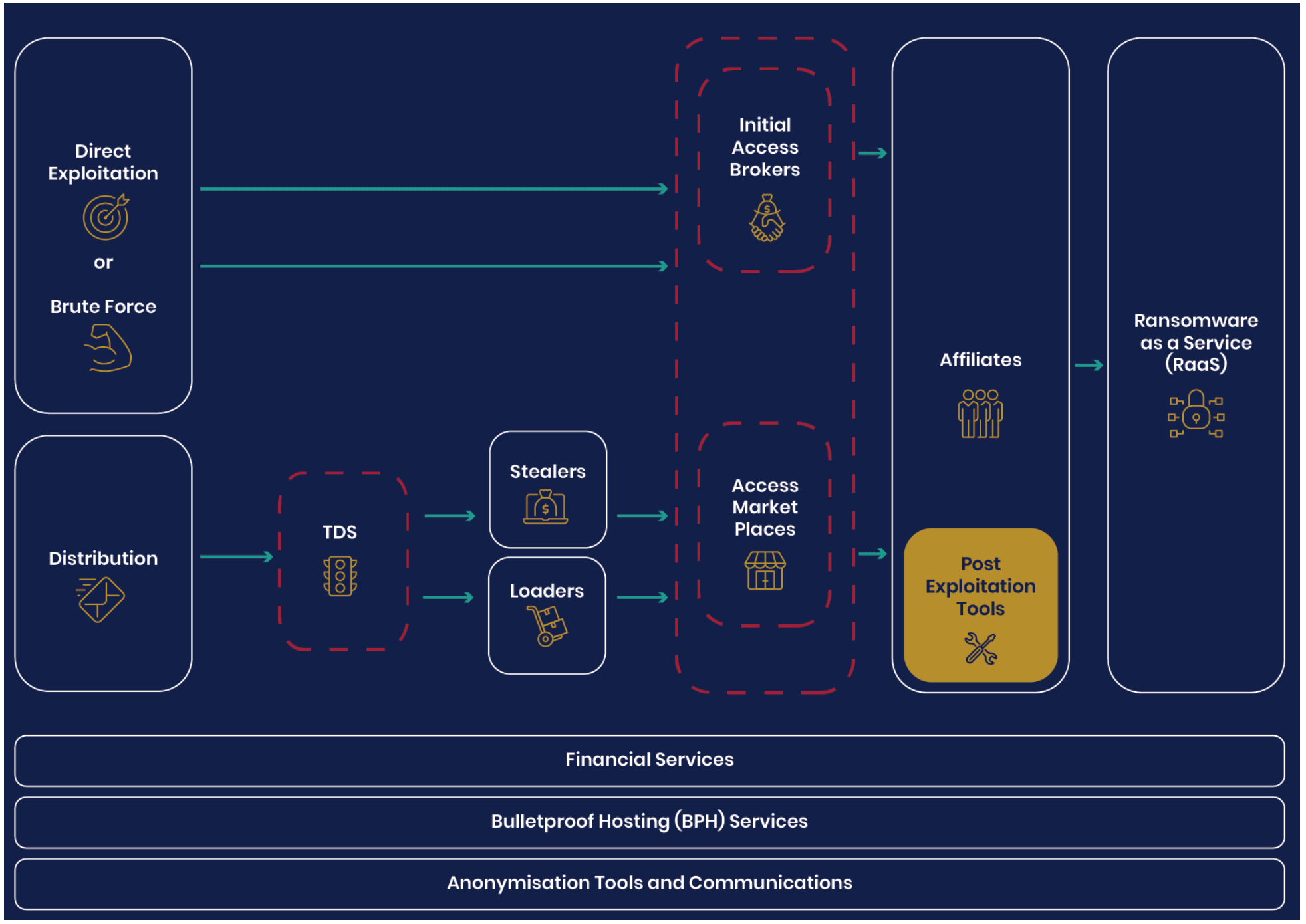
Ransomware gangs have evolved and adapted to survive what was described as “a climate of heightened pressure from government and law enforcement agencies.
“While individual groups have had to cease operation, as a whole the criminal industry is effective at amending its activities and business models dynamically to efficiently extract funds from victims,” said James Babbage, the director general of threats at the NCA — and up until recently the commander of the National Cyber Force.
“The proliferation of capable cybercrime tools and services, and subsequent lowering of the barrier of entry, means that ransomware, especially ransomware-as-a-service, will continue to be a significant threat to UK individuals, businesses and organizations,” he added.
“Ransomware is fundamentally about criminal monetisation of cyber vulnerabilities. The most effective systemic response is preventing future attacks by investing in increased resilience and better protected systems,” Babbage said.
“The UK is a top target for cybercriminals. Their attempts to shut down hospitals, schools and businesses have played havoc with people’s lives and cost the taxpayer millions,” said security minister Tom Tugendhat, adding: “Sadly, we’ve seen an increase in attacks.”
Alexander Martin
is the UK Editor for Recorded Future News. He was previously a technology reporter for Sky News and a fellow at the European Cyber Conflict Research Initiative, now Virtual Routes. He can be reached securely using Signal on: AlexanderMartin.79



