North Korean gov’t hackers targeted aerospace company in Spain
Hackers connected to a notorious group within the North Korean government launched an attack against an aerospace company in Spain, according to researchers at security company ESET.
In a report on Friday, researchers said they discovered a campaign by hackers connected to Lazarus — an infamous group that has stolen billions from cryptocurrency firms over the last two years.
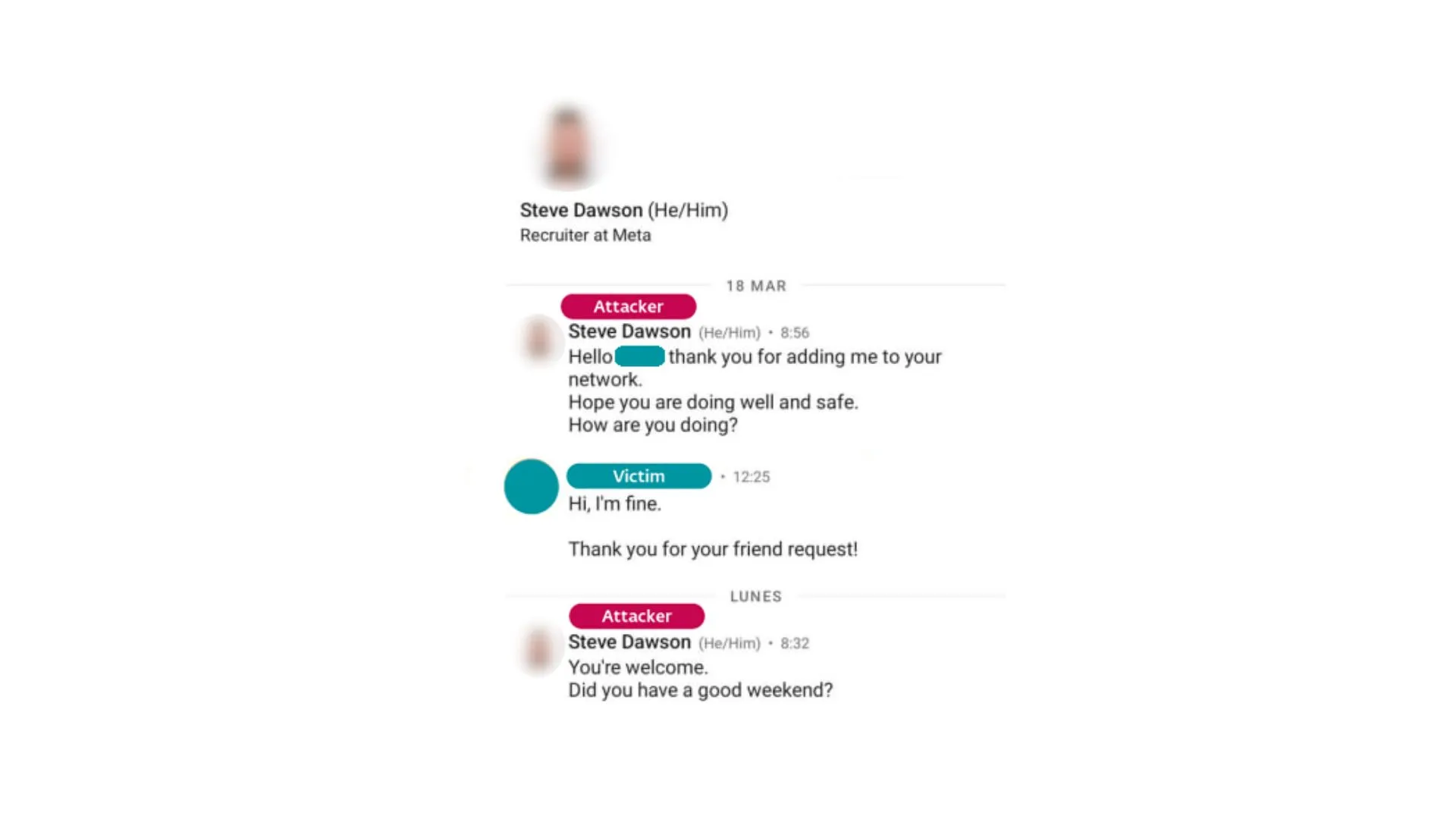
Employees of the unnamed company were sent messages on LinkedIn from a fake Meta recruiter and tricked into opening malicious files that purported to be coding quizzes or challenges.
When opened, the files infect a victim’s device with a backdoor that would allow the hackers to conduct espionage, according to ESET.
“The most worrying aspect of the attack is the new type of payload, LightlessCan, a complex and possibly evolving tool that exhibits a high level of sophistication in its design and operation, and represents a significant advancement in malicious capabilities compared to its predecessor, BlindingCan,” said ESET researcher Peter Kálnai, who made the discovery.
The hackers were successful in gaining access to the company’s network through a successful spearphishing campaign.
The fake recruiter claimed to be from Meta and offered the employees two coding challenges that they said were part of the application process. The employee, one of several contacted, downloaded the files on a company device.
The researchers noted that the campaign was sophisticated, with malware intended only for the victim’s machine.
Lazarus has existed since at least 2009 and continues to launch a range of campaigns targeting organizations important to North Korea.
“The diversity, number, and eccentricity in implementation of Lazarus campaigns define this group, which performs all three pillars of cybercriminal activities: cyberespionage, cybersabotage, and pursuit of financial gain,” ESET researchers said.
“Aerospace companies are not an unusual target for North Korea-aligned APT groups.”
Many of the country’s cyberattacks contribute to the country’s nuclear weapons program, either stealing cryptocurrency and money to fund the program or hacking into companies with technical knowledge that can support their efforts.
Job recruitment lures are a hallmark of North Korean hackers, who have used the tactic repeatedly to target a wide range of industries.
Last year, researchers from Symantec and Google published a report about a North Korean campaign where hackers posed as recruiters from Disney, Google and Oracle offering fake job opportunities to people working for chemical sector organizations in South Korea.
In July, North Korean hackers used fake U.S. military job-recruitment documents to lure people into downloading malware staged on legitimate, but compromised, South Korean e-commerce sites.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.

