N. Korea-linked operation combines US military lures, S. Korean e-commerce sites
Hackers allegedly connected to the North Korean government are using fake U.S. military job-recruitment documents to lure people into downloading malware staged on legitimate — but compromised — South Korean e-commerce sites.
Oleg Kolesnikov, vice president of threat research at Securonix, told Recorded Future News that what stands out the most about the campaign is the use of legitimate websites as a staging ground for malware.
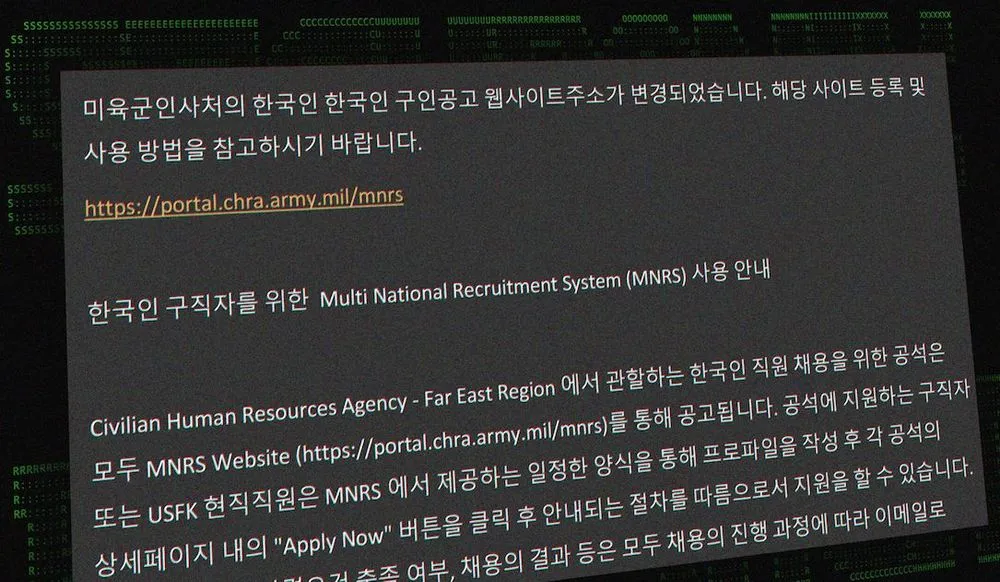
“We’re seeing the attackers use targeted phishing e-mails to drop authentic looking lure documents in a zip archive,” Kolesnikov said. “Among other things, there are references to U.S. Army recruitment and MNRS resources included within these documents.” MNRS refers to the Multi National Recruitment System that the Pentagon uses to fill civilian jobs overseas.
In research published Friday, Securonix is calling the group STARKMULE. Due to the targets and type of attack, the researchers believe the group labeled APT37 — a North Korean hacking outfit — or other similar teams may be behind the campaign. APT37 is linked to the Ministry of State Security and focuses on attacking South Korean targets.
“Based on our experience and some of the current indicators we have seen, there is a good chance that the threat originates from North Korea. However, the work on final attribution is still in progress,” Kolesnikov said about STARKMULE.
The Securonix report says the campaign is targeted at Korean speakers. The zip files attached to the phishing emails are typically given titles that translate to things like “U.S. Army job posting website address and how to use it.” When opened, the zip file has three documents, one of which is titled “Multi National Recruitment System Templete.pdf.zip.”
The goal is to get the victims to open the attached documents. The files open malware that allows the hackers to establish persistence on a victim’s machine and communicate with the compromised device.
The researchers did not say how many people have been compromised or if the attacks have been successful.
Compromised South Korean sites
The malware is held on legitimate websites, allowing the hackers to “blend in with normal traffic to evade detection when it comes to delivering malware stagers and managing full on command and control to the victim’s machine.”
“The threat actors' infrastructure appears to be solely based on two compromised websites that appear to be legitimate businesses. It’s possible that there could be more compromised websites that the threat actors are using, however in this attack chain we only observed communication between the two: hxxp://www.jkmusic.co[.]kr (182.162.94[.]42) hxxp://www.notebooksell[.]kr (183.111.169[.]84),” the researchers said.
“Both websites are registered in Korea and at the time of publication are not flagged as malicious by blacklisting websites including Virustotal. Both are ecommerce sites which only utilize the HTTP protocol.”
North Korean groups have a long history of spoofing a wide variety of organizations in an effort to get victims to open documents and download malware.
Over the last week, several campaigns by North Korean hackers have been uncovered, including one exploiting GitHub to target the personal accounts of employees of technology firms and another supply-chain attack targeting cryptocurrency companies through software company JumpCloud.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.