Hackers posed as reporters in attacks on North Korea experts, Google says
Government-backed hackers allegedly connected to the North Korean military targeted people with expertise in North Korea policy issues by posing as journalists, according to a new report.
Researchers from Google’s Threat Analysis Group (TAG) released the report Wednesday as a follow-up to one published last week by cybersecurity firm Mandiant — which is owned by Google. Mandiant’s report highlighted the work of APT43, a group of alleged North Korean government hackers that have spent years running espionage campaigns targeted at government and business organizations in South Korea and the U.S.
In Wednesday’s blog post, TAG researchers said they have been using the name “Archipelago” to track a subset of APT43 activity since 2012. Their team has seen the group “target individuals with expertise in North Korea policy issues such as sanctions, human rights, and non-proliferation issues.”
“These targets include Google and non-Google accounts belonging to government and military personnel, think tanks, policy makers, academics, and researchers in South Korea, the US, and elsewhere,” the researchers said, noting that they use a variety of tactics ranging from phishing emails to malicious Chrome extensions.
“ARCHIPELAGO often sends phishing emails where they pose as a representative of a media outlet or think tank and ask North Korea experts to participate in a media interview or request for information (RFI),” they said.
The phishing emails seen by TAG researchers urge victims to click on a link that will purportedly take them to the interview questions. Victims are taken to a phishing site where they are asked to enter their Google password, and the hackers can track keystrokes.
Once the password is entered, they are taken to a Google doc with questions and other information.
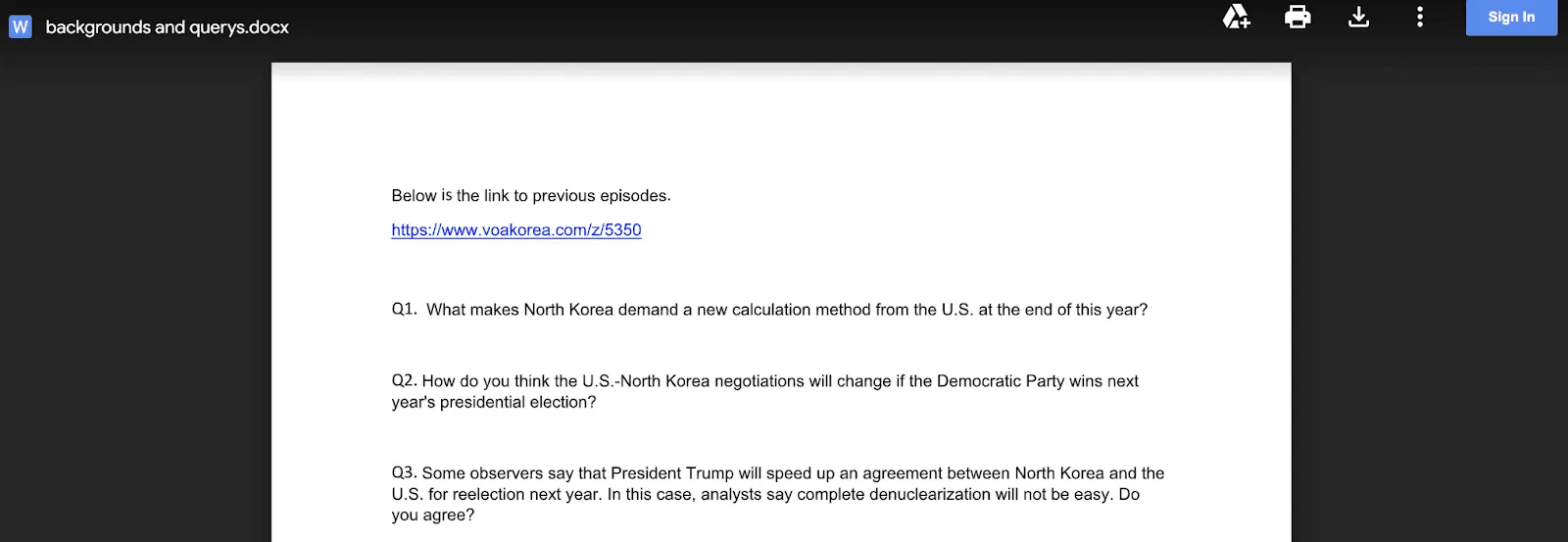
The hackers that take part in the Archipelago campaign work to build a bond with victims, spending days or weeks exchanging emails before sending the malicious link or file.
One example seen by the researchers involved a hacker posing as a journalist for a South Korean news agency that involved multiple benign emails about the search for North Korea experts.
It was only after several emails back and forth that the hackers sent a OneDrive link to a password-protected file that contained malware. TAG also found some links that involved “browser-in-the-browser” phishing pages — which present victims with a fake browser window masquerading as a real URL with a login prompt.
Victims typically enter their username and password thinking it is a legitimate login page.
Shifts over time
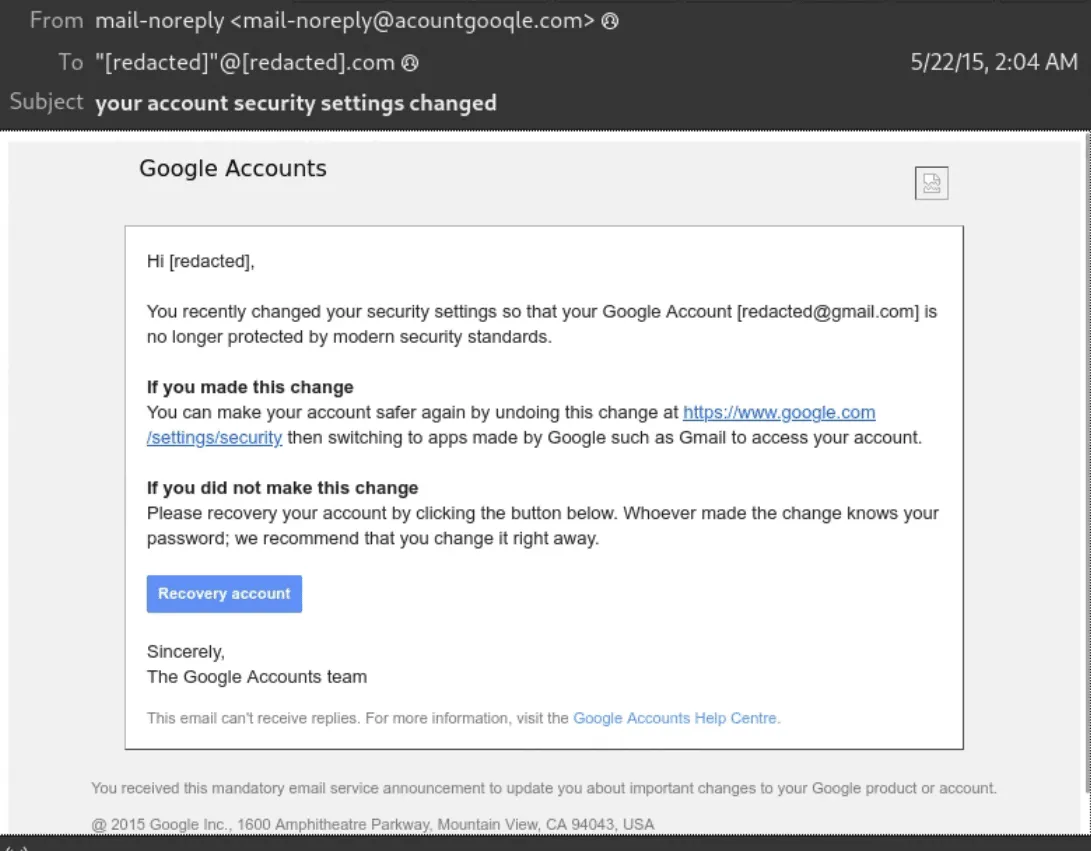
The researchers noted that Archipelago actors have evolved their phishing tactics over time, shifting from fairly standard messages that masquerade as Google account security alert emails to more sophisticated tactics.
In one 2022 campaign, the group used emails purporting to be from the State Department Federal Credit Union notifying customers of malicious logins from their Google Account.
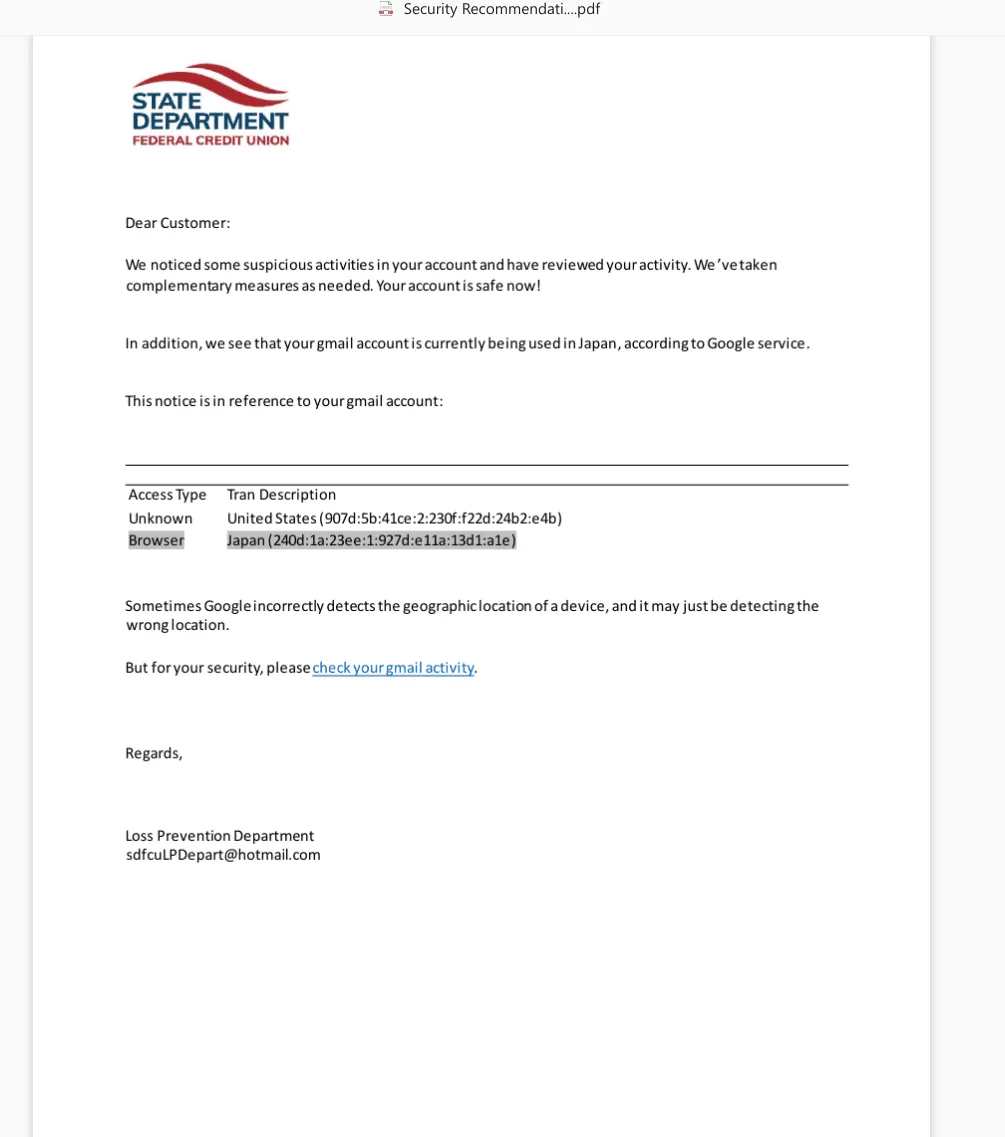
TAG said the group has been able to evade antivirus tools by password protecting its malware in files and then sharing the password with victims in phishing emails.
Archipelago continues to find different ways to deliver malware, even adopting techniques used by cybercriminals.
Malware delivered through ISO files has become incredibly popular, and ARCHIPELAGO used the technique in a recent campaign involving a phishing email with a Google Drive link to an ISO file titled “Interview_with_Voice_of_America.iso.”
Within the ISO file was a ZIP which contained a password-protected document that, when decrypted, installed a malware known as BabyShark.
Chrome extension abuse
Google said it has been forced to introduce significant changes to the Chrome extension ecosystem because of ARCHIPELAGO’s frequent abuse of them.
As far back as 2018, the group has used malicious Chrome extensions to steal usernames, passwords and browser cookies. Typically, the hackers send victims a phishing email with a link to a document that urges them to install a malicious Chrome extension.
“More recently, ARCHIPELAGO has attempted work-arounds to install a new malicious Chrome extension known publicly as SHARPEXT. If successfully installed on a user system, SHARPEXT can parse emails from active Gmail or AOL Mail tabs and exfiltrate them to an attacker-controlled system,” TAG researchers explained.
“As a result of improved security in the Chrome extension ecosystem, ARCHIPELAGO must now complete several additional steps to install the extension, including first successfully installing malware on the user system and then overwriting the Chrome Preferences and Secure Preferences files to allow the extension to run.”
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



