Microsoft attributes alleged Chinese attack on Indian power grid to ‘Boa’ IoT vulnerability
Microsoft has tied an attack on seven facilities managing the electricity grid in Northern India to a vulnerability affecting a web server discontinued in 2005 but still used widely by vendors across a variety of IoT devices and popular software development kits.
Members of Microsoft’s Defender Threat Intelligence team and researchers with the Defender for IoT unit looked into an April report from Recorded Future that said they observed “likely network intrusions targeting at least 7 Indian State Load Despatch Centres (SLDCs) responsible for carrying out real-time operations for grid control and electricity dispatch” near the disputed India-China border in Ladakh. The Record is an editorially independent unit of Recorded Future.
Microsoft researchers investigated the attack activity and identified a vulnerable component on all the IP addresses, finding evidence of a supply chain risk that may affect millions of organizations and devices.
“We assessed the vulnerable component to be the Boa web server, which is often used to access settings and management consoles and sign-in screens in devices,” the Microsoft researchers said this week in a new report.
“Despite being discontinued in 2005, the Boa web server continues to be implemented by different vendors across a variety of IoT devices and popular software development kits (SDKs). Without developers managing the Boa web server, its known vulnerabilities could allow attackers to silently gain access to networks by collecting information from files.”
The researchers added that those affected “may be unaware that their devices run services using the discontinued Boa web server, and that firmware updates and downstream patches do not address its known vulnerabilities.”
Microsoft noted that the attacks detailed in the Recorded Future report were part of a string of attacks on Indian critical infrastructure since 2020 that has continued until as recently as October 2022, when the Hive ransomware group attacked major energy provider Tata Power.
The researchers believe that Boa servers were running on the IP addresses provided by Recorded Future at the time of the attack and that the electrical grid attack targeted exposed IoT devices running Boa.
“The combination of Boa and suspicious response headers was identified on another set of IP addresses, displaying similar behavior to those found by Recorded Future. While these IP addresses are not confirmed as malicious, we recommend they be monitored to ensure no additional suspicious activity,” Microsoft said.
“Investigating the headers further indicated that over 10% of all active IP addresses returning the headers were related to critical industries, such as the petroleum industry and associated fleet services, with many of the IP addresses associated to IoT devices, such as routers, with unpatched critical vulnerabilities, highlighting an accessible attack vector for malware operators.”
Other evidence led researchers to believe that there were more intrusions and malicious activity on networks.
Since April, Microsoft researchers tracking the evidence from the Recorded Future report have found addresses compromised by a variety of attackers employing different malicious methods.
Some IP addresses were “leveraged to download a variant of the Mirai malware family shortly following the report’s release” while Microsoft researchers also found evidence of attempts to “connect with default credentials through brute force methods and attempts to run shell commands.”
“Microsoft continues to see attackers attempting to exploit Boa vulnerabilities beyond the timeframe of the released report, indicating that it is still targeted as an attack vector,” they wrote.
The Boa web server is used widely across a variety of tools, including IoT devices like routers and cameras. The tool is used to access settings and management consoles as well as sign-in screens.
Microsoft and several other experts noted how concerning the popularity of Boa web servers is considering that it was formally discontinued in 2005. Microsoft Defender Threat Intelligence platform data showed more than 1 million internet-exposed Boa server components around the world over the span of a week.
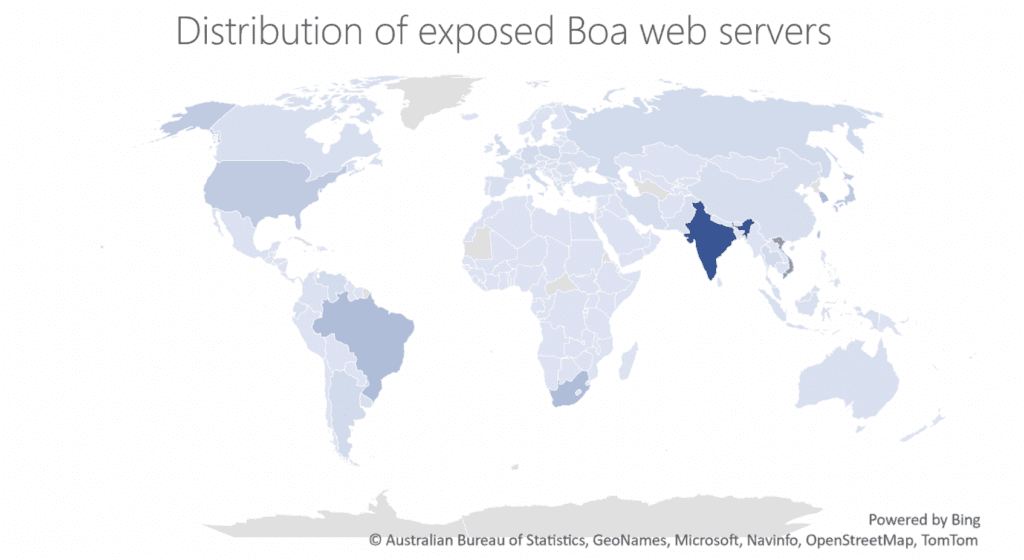
“Boa web servers remain pervasive in the development of IoT devices, one reason for this could be its inclusion in popular SDKs, which contain essential functions that operate system on chip (SOC) implemented in microchips,” the researchers explained.
“Vulnerable components like Boa and SDKs are often distributed to customers within devices, contributing to supply chain vulnerabilities. Popular SDKs like those released by RealTek, are used in SOCs provided to companies that manufacture gateway devices like routers, access points, and repeaters.”
Microsoft noted that critical bugs like CVE-2021-35395 – which affects RealTek’s SDK – and CVE-2022-27255, a zero-click overflow vulnerability, reportedly affect millions of devices globally.
These kinds of vulnerabilities allow attackers to launch code, compromise devices, deploy botnets, and move laterally on networks.
Boa servers themselves are affected by several known vulnerabilities, including arbitrary file access (CVE-2017-9833) and information disclosure (CVE-2021-33558), according to the researchers.
Both of these vulnerabilities may allow attackers to execute code remotely after gaining device access by reading the “passwd” file from the device or accessing sensitive URIs in the web server to extract a user’s credentials. Moreover, these vulnerabilities require no authentication to exploit, making them attractive targets.
“The popularity of the Boa web server displays the potential exposure risk of an insecure supply chain, even when security best practices are applied to devices in the network. Updating the firmware of IoT devices does not always patch SDKs or specific SOC components and there is limited visibility into components and whether they can be updated,” the researchers explained.
“The known CVEs impacting such components can allow an attacker to collect information about network assets before initiating attacks, and to gain access to a network undetected by obtaining valid credentials. In critical infrastructure networks, being able to collect information undetected prior to the attack allows the attackers to have much greater impact once the attack is initiated, potentially disrupting operations that can cost millions of dollars and affect millions of people.”
Several operational technology cybersecurity experts said the incident is yet another reminder of how troves of vulnerabilities exist in tools that are often used for decades without updates.
Chris Grove, a director at Nozomi Networks, told The Record that this incident should be a reminder that vulnerabilities like this could exist for decades before being discovered, and once discovered, can be hard if not impossible to hunt down and find within large, complex, global operational technology systems.
Having a detailed asset inventory down to the component level is crucial to address these types of supply chain risks, Grove said.
Additionally, it’s important that systems are fully monitored to identify attempts, even in the past, to take advantage of these types of vulnerabilities.
“We just found out about it, but did an attacker leverage it prior to that knowledge? Maybe an attacker used this years ago to gain initial access, and now they are stealthily implanted behind the defenses,” he said.
“Organizations that maintain a high level of visibility on their networks will fare better in these scenarios.”
KnowBe4’s James McQuiggan added that supervisory control and data acquisition (SCADA) systems in critical infrastructure environments are particularly susceptible because of the limited updates and downtime possible for them, making them high-value targets for cybercriminals.
While other organizations may have updated and replaced their systems utilizing the seventeen-year-old open-source application, seeing them in SCADA environments and other critical infrastructure could still be a solid possibility, he noted.
Organizations, he added, need to audit their systems and software annually to ensure they are up to date and have low to no vulnerabilities.
Sami Elhini, biometrics specialist at Cerberus Sentinel, said he is personally familiar with Boa because he was in charge of designing a handheld device in 2017. He eventually decided against selecting it because it had not been maintained for more than a decade.
But that was not the only red flag.
“One only needs to read its documentation to determine that it served one purpose: to be fast. That in and of itself cannot be the sole criteria for product selection, sadly, in so many instances it is,” he said.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



