Meet Meris, the new 250,000-strong DDoS botnet terrorizing the internet
A new botnet consisting of an estimated 250,000 malware-infected devices has been behind some of the biggest DDoS attacks over the summer, breaking the record for the largest volumetric DDoS attack twice, once in June and again this month.
Named Mēris, the Latvian word for "plague," the botnet has been primarily used as part of a DDoS extortion campaign against internet service providers and financial entities across several countries, such as Russia, the UK, the US, and New Zealand.
The group behind the botnet typically sends menacing emails to large companies asking for a ransom payment. The emails, which target companies with extensive online infrastructure and which can't afford any downtime, contain threats to take down crucial servers if the group is not paid a certain amount of cryptocurrency by a deadline.
If victims don't pay, the hackers unleash their botnet in smaller attacks at the beginning that substantially grow in size with time in order to put pressure on the victims.
Meris - "a botnet of a new kind"
Qrator Labs, a Russian DDoS mitigation service, described Meris as "a botnet of a new kind" in a blog post published earlier today, following a series of attacks against Russian companies.
"In the last couple of weeks, we have seen devastating attacks towards New Zealand, United States and Russia, which we all attribute to this botnet species," the company researchers said today.
"[Meris] can overwhelm almost any infrastructure, including some highly robust networks. All this is due to the enormous RPS power that it brings along," the company said, where RPS stands for requests per second, one of the two ways to measure the size of DDoS attacks [the other being Gbps, gigabytes per second].
The reason why Qrator Labs calls Meris one of a kind is that prior to this summer, most RPS-based DDoS attacks have been very rare and haven't been seen at this scale for the past five years.
Most botnets are typically configured to sling as much junk traffic at a target as possible in classic "bandwidth attacks," which are measured in Gbps.
Called volumetric or application-layer DDoS attacks, RPS attacks are different because attackers focus on send requests to a target server in order to overwhelm its CPU and memory. Instead of clogging its bandwidth with junk traffic, volumetric attacks focus on occupying servers' resources and eventually crashing them.
"For the last five years, there have virtually been almost no global-scale application-layer attacks," Qrator said today.
Botnet breaks DDoS records twice
But things changed this summer with the emergence of Meris, which was built on a modified version of the old Mirai DDoS malware, according to internet infrastructure company Cloudflare, which also had to deal with some of its attacks.
But instead of focusing on bandwidth attacks, like most Mirai variants, Meris focused on modules specialized in launching volumetric attacks, and, apparently, they found a sweet spot.
In the aftermath of its recent spree of attacks, Meris broke the record for the largest volumetric DDoS attack twice. It did it the first time earlier this summer, in June, when it was behind a large 17.2 million RPS DDoS attack that hit a US financial company, according to Cloudflare, which had the unpleasant task of mitigating this particular attack.
Today, Qrator Labs said Meris outdid itself again during an attack that took place this Sunday, September 5, which hit even a bigger milestone at 21.8 million RPS.
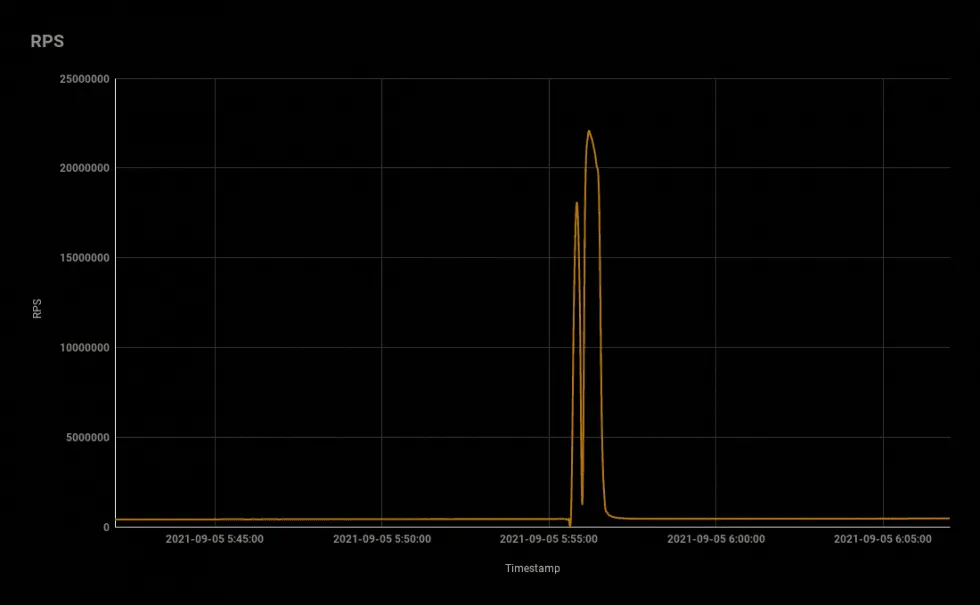
Qrator said it worked with Yandex to mitigate the attack, which was apparently hitting Yandex servers. But, a source involved in the incident told The Record that the target of the attack was actually a Russian bank that was keeping its e-banking portal on Yandex's cloud hosting service.
Botnet mostly consists of compromised MikroTik devices
Qrator says that after analyzing the source of most of the attack traffic, most of it led back to devices from MikroTik, a small Latvian company that sells networking gear such as routers, IoT gateways, WiFi access points, switches, and mobile network equipment.
The company said it wasn't able to determine if the attacker found and weaponized a zero-day in MikroTik's software or if they're just living past exploits.
Nonetheless, a zero-day appears to be in play, just by the large number of MikroTik devices that appear to have been enslaved in Mesir's gigantic 250,000-strong mesh.
A MikroTik spokesperson had the following to say when reached out for comment:
As far as we have seen, these attacks use the same routers that were compromised in 2018, when MikroTik RouterOS had a vulnerability, that was quickly patched.
Unfortunately, closing the vulnerability does not immediately protect these routers. If somebody got your password in 2018, just and upgrade will not help. You must also change password, re-check your firewall if it does not allow remote access to unknown parties, and look for scripts that you did not create.
We have tried to reach all users of RouterOS about this, but many of them have never been in contact with MikroTik and are not actively monitoring their devices. We are working on other solutions too.
There are no new vulnerabilities in these devices. RouterOS has been independently audited by several contractors, such as Leviathan security and others.
MikroTik
But besides bringing back volumetric (application layer) DDoS attacks, Meris also stands out due to its size. In recent years, DDoS botnets have rarely reached 50,000 infected devices.
This was because the code of several DDoS malware strains had been published online years ago, including Mirai, and this code was massively exploited to create numerous botnets that ended up fighting with each other over the limited number of devices they could infect, with very few botnets reaching even small figures of 15,000 over the past few years, let alone a 250,000 figure, unseen since late 2018.
All in all, what the Meris operators have achieved over the past few months can be considered impressive from a technical standpoint, but we're also talking about a cybercrime gang here, so expect a long list of technical outages in the coming months as the Meris operators continue to use their new toy for extortion and DDoS attacks.
Article updated on September 10 with comment from MikroTik.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.


