Maza Cybercrime Forum Hacked, User Data Dumped Online
A hacker has breached Maza Faka, one of the oldest underground cybercrime forums active today, shut down its Tor-based website, and leaked the details of around 3,000 users in a PDF file posted on the forum's front page.
The security breach, which took place yesterday, on March 3, 2021, resulted in the leak of sensitive details about the forum's registered users.
According to a copy of the leaked PDF file obtained by The Record, details such as usernames, emails, account passwords, and social media IDs (ICQ, Skype, AIM, MSN, and Yahoo) were posted online.
Additionally, the PDF file also contained information about each user's certificate file and certificate password, which the Maza forum was using as a form of a two-step verification process.
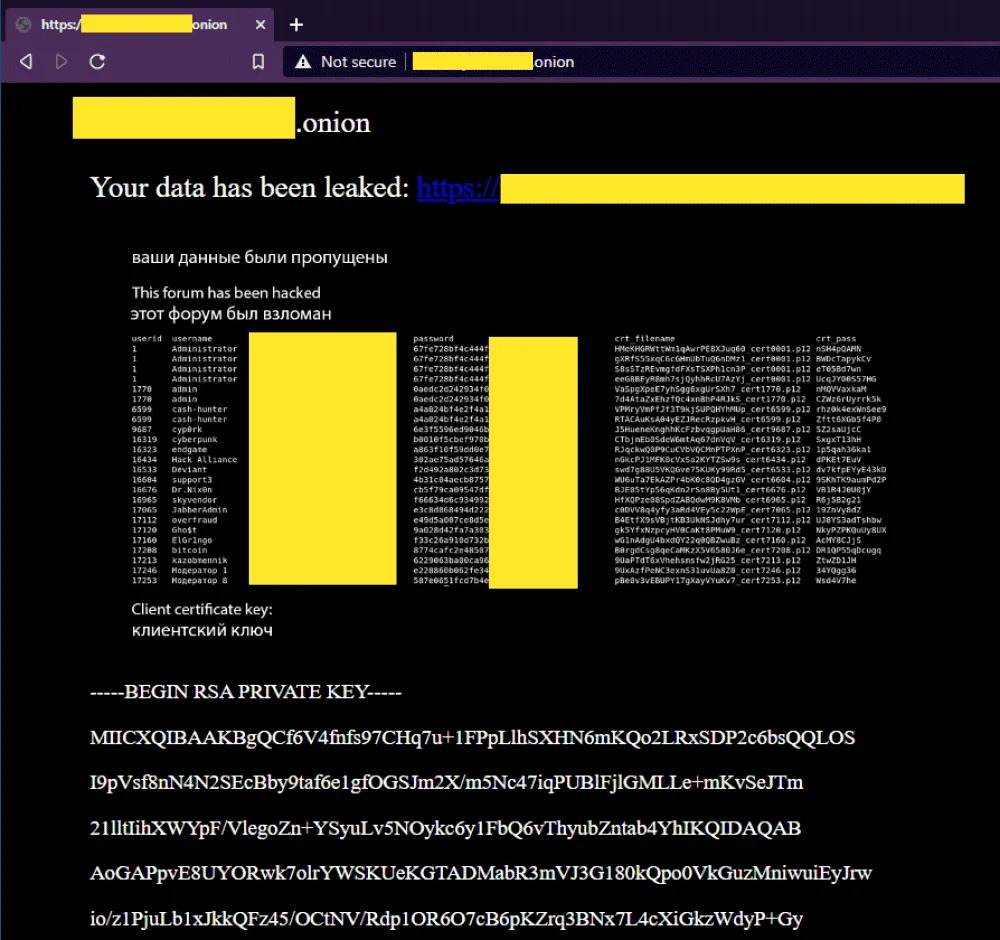
But while the Maza leak is small in size compared to other data breaches this year, it is likely one of the most important security incidents of 2021, as it has led to the broad exposure of data that may aid law enforcement agencies in tracking down former or current cybercriminals.
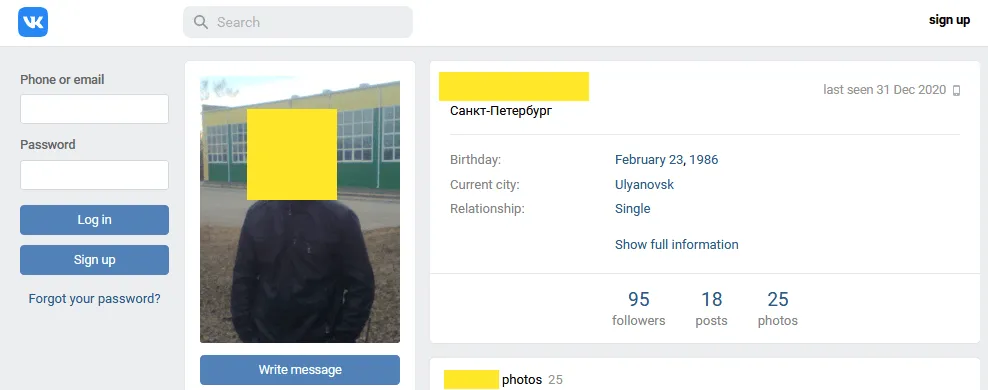
Dmitry Smilyanets, a threat intelligence analyst at Recorded Future who helped The Record analyze the Maza data, said the PDF file contains authentic information, which he was able to use to link several Maza users to public social media profiles.
End of the "forum era"
Threat intelligence firm Flashpoint, which also spotted the Maza hack earlier today, said in a blog post that multiple members of the underground cybercrime community are now discussing moving away from using emails as a means to register profiles, as these can be easily tracked back to their real-world identities.
Furthermore, Smilyanets told The Record that in Telegram channels, several respectable threat actors are now calling for an end to the "forum era."
These calls come after several major underground forums had suffered similar security breaches over the past few months. This includes:
- Joker's Stash - has recently shut down after the FBI and Interpol seized four of its proxy servers in December 2020.
- Verified - was temporarily hacked and shut down after hackers tricked the forum's domain registrar into handing over control over the site's domain to a threat actor.
- Exploit - suffered a security breach this week after hackers hijacked one of its DDoS mitigation solutions.
But among all these, Maza stands head and shoulders above the others, mainly due to the severity of its breach but also due to its long-standing reputation in the Russian-speaking cybercrime underground.
One of the most reputable cybercrime forums today
While unknown to the general reader, the Maza Faka forum is one of the oldest, if not the oldest, cybercrime portals active today.
The forum, which launched way back in 2003, has served for almost two decades as a place to trade stolen card details (an activity called "carding"), but also functioned as a marketplace to advertise other services like e-commerce fraud, bank fraud, and cash-out services.
Access to the forum has always been limited to a selected few.
"Registering on the forum requires a significant upfront fee, as well as several vouchers from current members who are in good standing on the forum and become financially responsible for the invited person in the case of disputes," Smilyanets told The Record.
"Primarily attributed to such a strict registration policy, monetary disputes are rare compared with most other forums. As a result, only senior and established members of the hacking underworld are capable of gaining access."
But, according to a Recorded Future threat intel bulletin, the forum's activity has waned in recent years, and new card breaches or POS malware strains were rarely posted on the site anymore.
Today, the Maza forum primarily serves as a reputation index for the top dogs of the cybercrime underground, many of whom use their Maza profiles to vouch for their reputations.
As a result, any information on Maza users leaked this week might help uncover years-worth of cybercrime campaigns and some of the oldest and long-standing threat actors today.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.


