Police plan week of LockBit revelations after capturing ‘unprecedented’ intelligence from gang’s infrastructure
LONDON, UNITED KINGDOM — An international coalition of law enforcement agencies led by Britain’s National Crime Agency (NCA) have garnered so much intelligence after hacking LockBit’s infrastructure they are set to release more insights over the rest of this week, officials have said.
The ransomware gang’s website was replaced by a splashpage on Monday evening. During a press conference in London on Tuesday morning, the NCA’s director general, Graeme Biggar, announced his agency had “gained unprecedented and comprehensive access to LockBit’s systems.”
Officials said that while some fragmentary remnants of peripheral infrastructure might remain accessible to the criminals — prompting counter-claims by LockBit that the operation had simply exploited a PHP vulnerability — it was the position of the NCA, FBI and Europol that the LockBit service was completely destroyed by their operation.
 Officials hold a briefing February 20, 2024, in London about the takedown of the LockBit ransomware gang. Image: Alexander Martin / Recorded Future News
Officials hold a briefing February 20, 2024, in London about the takedown of the LockBit ransomware gang. Image: Alexander Martin / Recorded Future News
The NCA hailed the “unprecedented technical access” that enabled the operation, which follows law enforcement hacks headed by the FBI in the United States as well as agencies in France and the Netherlands. Officials declined to go into technical details, but highlighted that information on LockBit’s backend infrastructure was now posted on the gang’s website.
Biggar said the international coalition collected decryption keys, as well as intelligence about who was using LockBit and the specific crimes they had committed. While two arrests had taken place on Tuesday morning — one in Ukraine and one in Poland — more were being planned for the future, Biggar said: “We are tenacious, and we will not stop in our efforts to target and pursue them in the months and the years to come.”
It is not clear whether those arrested were part of the core LockBit gang or if they were affiliates. Europol’s deputy executive director for operations, Jean-Philippe Lecouffe, said: “I don’t want to be too specific this morning. We need to investigate. We have seized a lot of material that we need to go through before we can really qualify that.”
“We have not arrested everyone in relation to LockBit, neither in the core or affiliates. This is a long-term process. We have now gathered an awful lot of information, we’ll be closing in on those individuals, particularly when they’re in jurisdictions that we can reach. But now all of them know that we’re on to them, and we’re looking for them, and they will be forever now looking over their shoulder.”
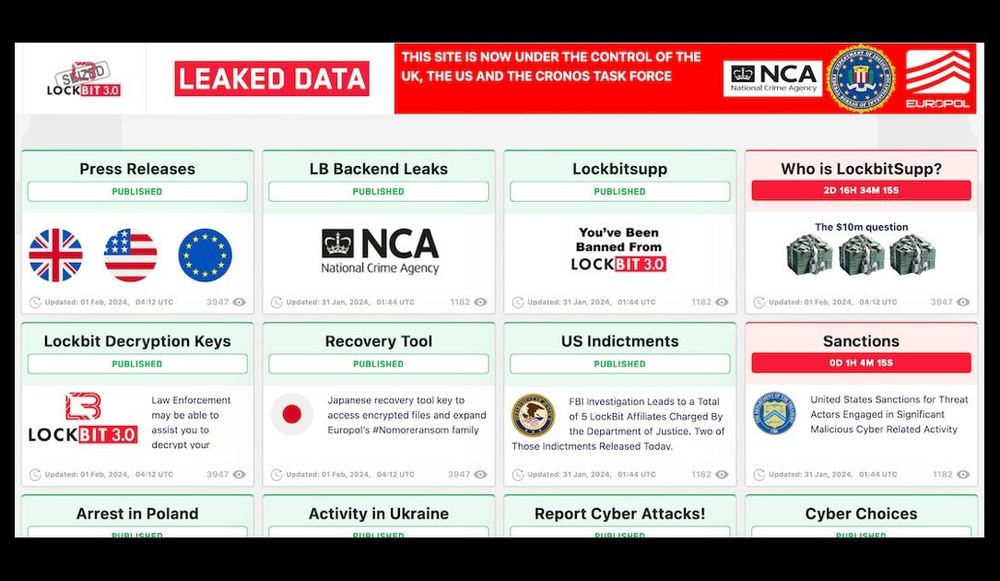
Paul Foster, the head of the NCA’s national cybercrime unit, said the agency would be using the gang’s seized website as a way to publish daily updates on a range of insights that his team had discovered buried within the gang’s digital infrastructure, where such insights didn’t interfere with ongoing investigations.
The LockBit site had previously listed the gang's victims in a series of panels, some with countdowns to pressurize the victims into paying, but now uses the same format to list information produced by the operation, including details and screenshots about LockBit’s backend and — with a countdown mimicking the gang’s own extortion tactics — about the group’s mysterious administrator known as Lockbitsupp.
Prolific and costly
LockBit operated as one of many ransomware-as-a-service gangs that — similar to software-as-a-service companies — provide a platform to customers. The LockBit platform offered a mechanism for these hackers (known as “affiliates” within the ransomware ecosystem) to encrypt the devices on a network and/or steal data and threaten to publish it on the gang’s darknet site, unless an extortion fee was paid.
While there are no objective measures of how prolific each ransomware-as-a-service operation is, LockBit has consistently published more victims who refused to pay a ransom to its darknet extortion site than any other outfit, over 2,000 according to the latest count — more than its closest three competitors (Conti, AlphV, Clop) combined — although there is some evidence that the true number of ransomware victims is orders of magnitudes larger than the numbers that appear on these sites.
Officials on Tuesday said they believed the gang accounted for 25% of all ransomware attacks.
 Screenshot of the "Affiliate Rules" page on the LockBit site.
Screenshot of the "Affiliate Rules" page on the LockBit site.
According to a page setting out its rules for affiliates, the LockBit gang itself received 20% of the final extortion fee. Over its four-year lifespan, the gang received at least $120 million, according to officials — although it is not clear if this is before or after the commission. The officials added that at least 200 cryptocurrency accounts had also been frozen in the operation, although their contents have not yet been disclosed.
Although LockBit’s rules purported to prohibit encryption against “institutions where damage to the files could lead to death, such as cardiology centers, neurosurgical departments, maternity hospitals and the like,” it permitted the theft of data from these targets — and any form of incident response to a cyberattack will cause disruption for network operators.
Read More: US indicts two Russian nationals in LockBit ransomware case
LockBit-linked cyberattacks had repeatedly sought to profit by risking lives, including by forcing two major hospitals in upstate New York to divert ambulances, and, just days before Christmas, attacking Toronto’s Hospital for Sick Children, causing diagnostic and treatment delays for its patients — as well as extraordinary distress for the families affected — because clinical teams were struggling to receive lab reports and imaging results.
On Tuesday, Brett Leatherman, the deputy assistant director for cyber operations at the FBI, said “the LockBit criminal enterprise has caused significant harm to thousands of victims” and has been “indiscriminate in their targeting, exploiting organizations affiliated with government agencies, hospitals and schools.”
“Through this operation we have access to nearly 1,000 potential decryption tools, and the NCA, FBI, and Europol will be conducting victim engagement with over 2,000 known victims in the days and weeks to come,” added Leatherman.
Alexander Martin
is the UK Editor for Recorded Future News. He was previously a technology reporter for Sky News and a fellow at the European Cyber Conflict Research Initiative, now Virtual Routes. He can be reached securely using Signal on: AlexanderMartin.79