In a rare step, Activision warns CoD players of malware hidden in cheat apps
In a rare step for a company that seldomly issues security warnings, gaming giant Activision published research yesterday detailing how cybercriminals are hiding malware inside Call of Duty: Warzone cheats, warning users to stay away from such offers.
The Activision report [PDF] walks users through a step-by-step scenario of how these cheats start out as tutorials on hacking forums (screenshot #1), how the cheat software is mass-built, malware is added, and then the final package is advertised on gaming forums (screenshot #2) and via YouTube videos (screenshot #3) to players looking to get an edge.
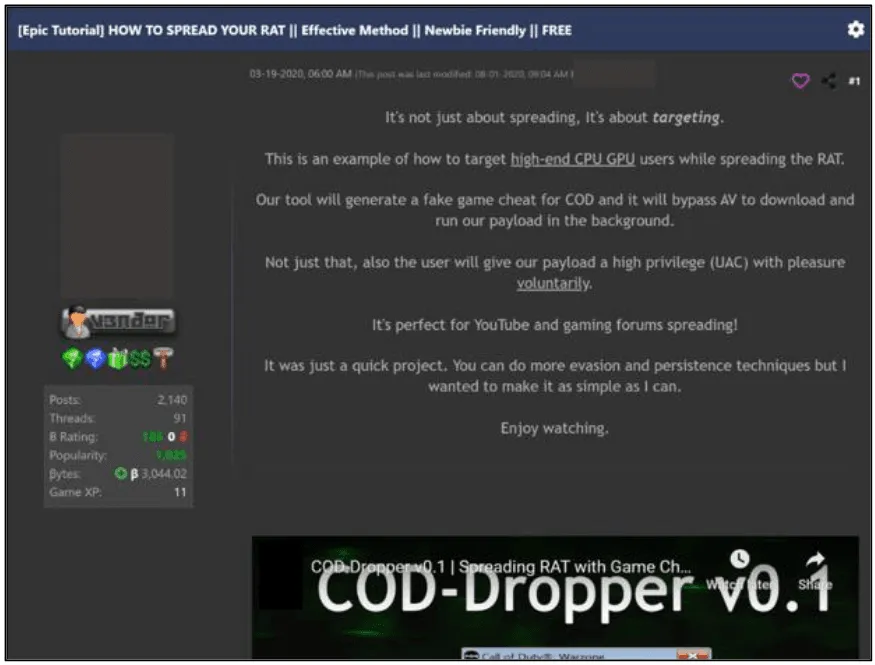
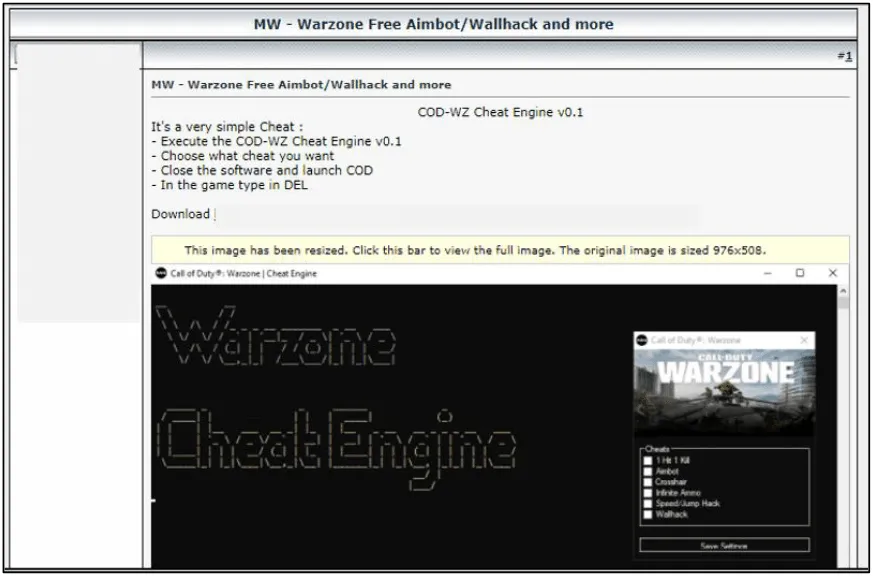
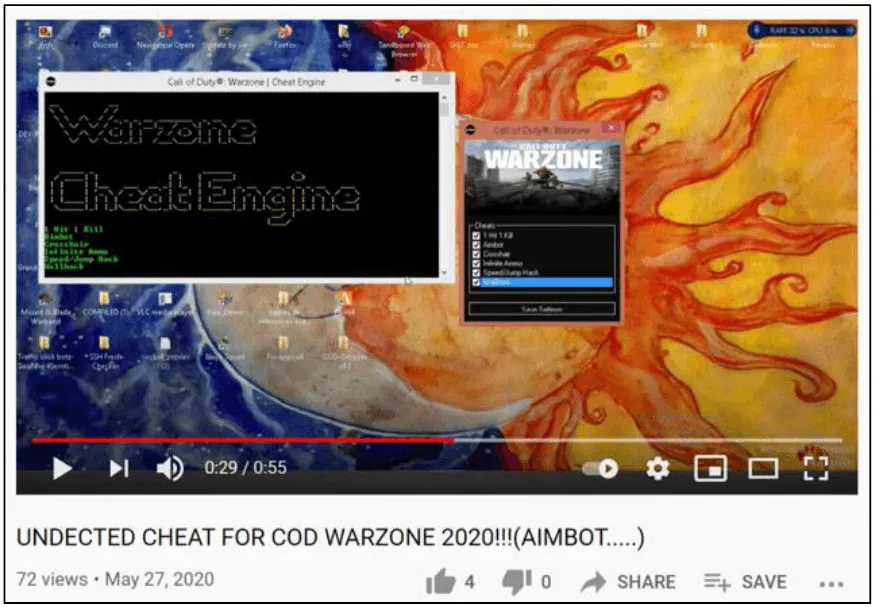
The game maker warns users against downloading or even testing such tools, as they will likely get infected with malware the first time they run the cheat.
This malware, usually called a dropper, is then used as a way to download and install additional malware that could be used to steal the user's passwords or install ransomware.
Furthermore, Activision also warns against installing any type of cheat software, even if malware has not yet been discovered in that particular tool, as this could leave users vulnerable to attacks from other threats in the future.
"When it comes down to it, the dependencies for a 'genuine' cheat to work are the same as those needed by most malware tools to successfully execute," Activision said.
"System protections need to be bypassed or disabled, and privileges need to be escalated to allow the program to run correctly and/or establish persistence. While this method is rather simplistic, it is ultimately a social engineering technique that leverages the willingness of its target (players that want to cheat) to voluntarily lower their security protections and ignore warnings about running potentially malicious software," the game maker said.
Activision has been swamped by cheaters
Motherboard, which first reported on the Activision research, pointed out that the company's report comes after the game maker has been fighting a wave of cheaters active in its primary product, the Call of Duty: Warzone multiplayer game.
In September 2020, the company banned 20,000 Warzone players for cheating and banned another 60,000 in February this year.
The Activision report also comes on the same day that Cisco's Talos division also released its own report on malware hidden in video game cheats.
But what Activision is dealing with is in no way unique. Every time a popular game comes out, malware operators rush to offer malware-laced cheats or early access apps.
This has happened before with games such as PUBG (PlayerUnknown's BattleGrounds), Counter-Strike: Global Offensive (CS:GO), Apex Legends, Fortnite, and more.
You deserved to be infected with a malware when you want to cheat. Pics taken by the attacker. #malwaremustdie #fortnite #cheater pic.twitter.com/5IJ1Rde0Gz
— .sS.! (@sS55752750) February 13, 2018
Luckily, when some of these malware-in-cheats operations grow too large, authorities usually intervene to break up criminal rings.
After 15 suspects were arrested in China in 2018 for developing PUBG cheats, Chinese authorities arrested another ten suspects this week for running the "world's biggest' video-game-cheat operation," and making more than $76 million from selling Call of Duty Mobile cheats.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



