Chinese hackers target European embassies with HTML smuggling technique
Chinese cyber spies have been targeting the foreign affairs ministries and embassies of European states in recent months, according to new research.
The espionage campaign “represents a larger trend within the Chinese ecosystem, pointing to a shift to targeting European entities, with a focus on their foreign policy,” researchers from Check Point said Monday.
The hackers were spotted using a new delivery method to deploy the modular PlugX malware implant, effectively smuggling it inside HTML documents, something which Check Point warned had “until recently helped the campaign fly under the radar.”
Samples of lures posted to the VirusTotal malware repository had filenames that “strongly suggest that the intended victims were diplomats and government entities,” according to Check Point, while the lure material itself “contained diplomatic-related content,” which “in more than one case … was directly related to China.”
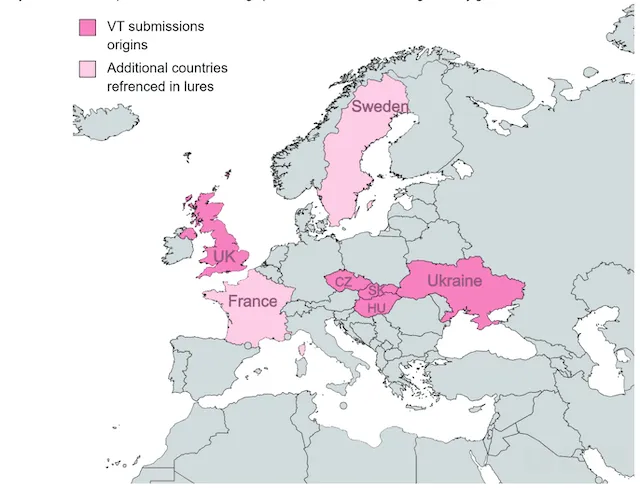
These lures included a letter allegedly originating from the Serbian Embassy in Budapest, a document stating the priorities of the Swedish presidency of the Council of the European Union, and an article about two Chinese human rights lawyers sentenced to more than a decade in prison.
HTML smuggling is a hacking technique that has been used in various forms for years, exploiting HTML features to conceal data and files from automated content filters by including them as JavaScript blobs that get reassembled on the target’s machine.
The PlugX malware itself remained a recognizable variant of the tool, which has previously been used by multiple suspected Chinese threat groups, including to target the Vatican in 2020, an Indonesian intelligence service in 2021 and Ukraine in 2022.
PlugX has also been discovered on USB drives being used to target people in Mongolia, Papua New Guinea, Ghana, Zimbabwe, and Nigeria.
Palo Alto Networks released a lengthy report on the malware in 2021.
Check Point said it was tracking the campaign as SmugX and said it “overlaps with previously reported activity by Chinese APT actors RedDelta and Mustang Panda.”
“While none of the techniques observed in this campaign is new or unique, the combination of the different tactics, and the variety of infection chains resulting in low detection rates, enabled the threat actors to stay under the radar for quite a while,” warned Check Point.
Alexander Martin
is the UK Editor for Recorded Future News. He was previously a technology reporter for Sky News and a fellow at the European Cyber Conflict Research Initiative, now Virtual Routes. He can be reached securely using Signal on: AlexanderMartin.79



