Google: Nation-state phishing campaigns expanding to target Eastern Europe orgs
Wide-ranging phishing campaigns targeting Eastern European countries are continuing to expand, according to a new report from Google’s Threat Analysis Group (TAG).
Cyber actors from Russia, Belarus and China are using a variety of email-based attack methods to steal credentials and gain access to organizations in Ukraine, Lithuania, Central Asia, countries in the Baltics and even Russia itself.
“APT28 or Fancy Bear, a threat actor attributed to Russia GRU, was observed targeting users in Ukraine with a new variant of malware,” TAG’s Billy Leonard wrote.
“The malware, distributed via email attachments inside of password protected zip files (ua_report.zip), is a .Net executable that when executed steals cookies and saved passwords from Chrome, Edge and Firefox browsers. The data is then exfiltrated via email to a compromised email account.”
Other Russian groups – including the FSB’s Turla and another Russian-based threat actor named COLDRIVER – were implicated in several attacks targeting defense and cybersecurity organizations in the Baltics as well as government and defense officials, politicians, NGOs and think tanks, and journalists.
COLDRIVER was previously accused by Google of targeting several U.S.-based NGOs, think tanks, the military of a Balkans country and a Ukrainian defense contractor with credential phishing campaigns. It also went after the military of multiple Eastern European countries and a NATO Centre of Excellence, which trains and educates military leaders and specialists.
Turla used unique links in emails that took victims to DOCX files hosted on attacker-controlled infrastructure while COLDRIVER used Gmail accounts to send credential phishing emails.
Leonard noted that the group has shifted tactics in recent weeks, moving from including phishing links in emails to attaching malicious PDFs of DOC files.
Attackers attached to Belarusian group Ghostwriter have continued to target high-risk individuals in Ukraine with credential phishing attacks launched through Gmail accounts.
The emails contained links to compromised sites that took victims to sites that collected their credentials.
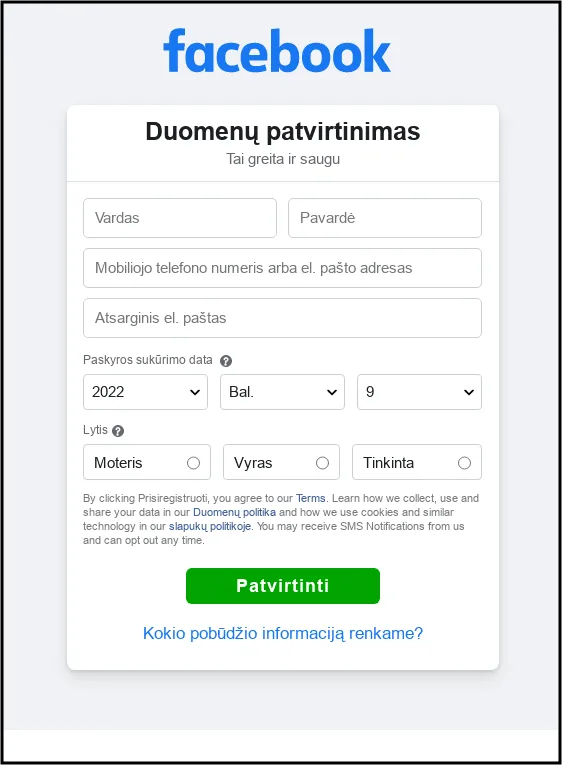
Ghostwriter also launched a phishing campaign in April targeting Facebook users primarily based in Lithuania. The attacker sent links to domains pretending to be from Facebook’s security team.
In March, Ghostwriter was seen using the ‘Browser in the Browser’ phishing technique.
Google also found that a group connected to China's PLA SSF — named Curious Gorge — was found targeting government, military, logistics and manufacturing organizations in Ukraine, Central Asia and even Russia.
“In Russia, long running campaigns against multiple government organizations have continued, including the Ministry of Foreign Affairs,” Leonard said. “Over the past week, TAG identified additional compromises impacting multiple Russian defense contractors and manufacturers and a Russian logistics company.”
Curious Gorge was previously seen targeting government and military organizations in Ukraine, Kazakhstan and Mongolia.
The blog post from Google includes recently observed IPs and credential phishing domains seen in the attacks by these groups.
Google’s TAG has released several blog posts about the threats they’re seeing in relation to the conflict in Ukraine, previously highlighting the work of groups like FancyBear/APT28, Ghostwriter and Mustang Panda.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



