‘Mustang Panda’ hacking group exploiting Ukraine invasion, COVID-19 to spread malware
Cybersecurity researchers have uncovered a new campaign by advanced persistent threat (APT) group Mustang Panda to spread a variant of the Korplug malware by exploiting the invasion of Ukraine, COVID-19 and other timely topics.
Slovak security firm ESET published a report this week detailing the campaign, which targeted research entities, internet service providers and European diplomatic missions located in East and Southeast Asia.
“Based on code similarities and the many commonalities in Tactics, Techniques, and Procedures, ESET researchers attribute this campaign with high confidence to Mustang Panda, also known as TA416, RedDelta, or PKPLUG. It is a cyberespionage group mainly targeting governmental entities and NGOs,” explains ESET malware researcher Alexandre Côté Cyr.
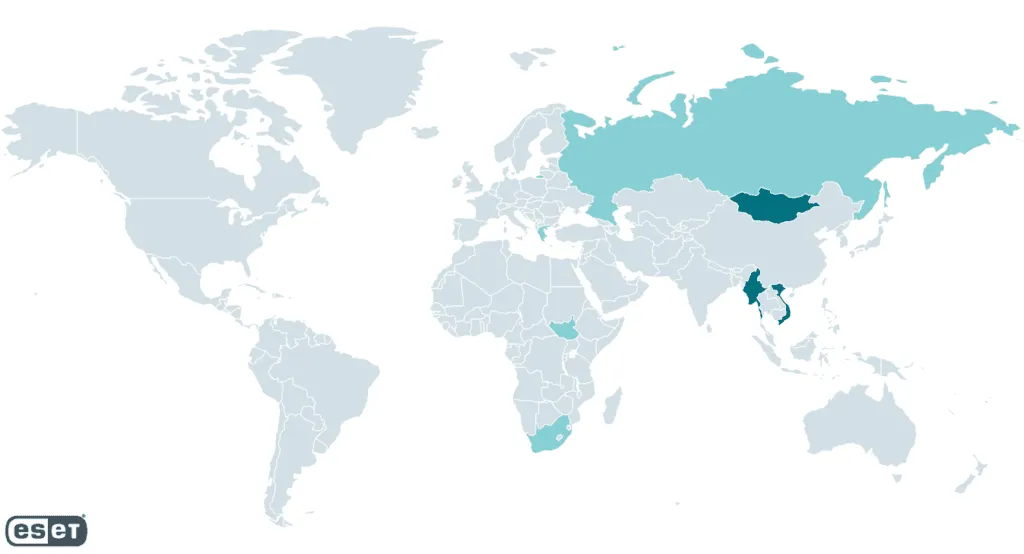
A map of the hacking group's victims. Image: ESET
ESET Research called the Korplug variant “Hodur” because it was similar to another variant called “Thor.” In Norse mythology Hodur was Thor’s blind half-brother.
Côté Cyr discovered Hodur during his research and found lures like files named “Situation at the EU borders with Ukraine.exe.”
Other lures included files about changing COVID-19 travel restrictions, regional aid maps for Greece and new regulations from the European Parliament. Some of the documents used in the campaign are referencing actions taken within the last month.
Côté Cyr noted that the victims of the campaign are located across Asia but noted that there was a particular focus on Mongolia, Vietnam and Myanmar. Other victims of the latest campaign are located across Greece, Cyprus, Russia, South Sudan, and South Africa.
The group made waves in 2020 for a cyberattack on The Vatican and the group typically uses custom loaders for shared malware including Cobalt Strike, Poison Ivy, and Korplug, ESET Research explained. The group has previously created several Korplug variants.
“Compared to other campaigns using Korplug, every stage of the deployment process utilizes anti-analysis techniques and control-flow obfuscation, to make the investigation more difficult for us malware researchers,” Côté Cyr said.
“What sets this campaign apart is the heavy use of control-flow obfuscation and anti-analysis techniques at every stage of the deployment process. We haven’t been able to observe the initial deployment vector, but our analysis points to phishing and watering hole attacks as likely vectors. In instances where we saw a downloader, the filenames used suggest a document with an interesting subject for the target.”
The report says the campaign dates back to at least August 2021 and is still ongoing as of March 2022.
ESET Research said Korplug – which is sometimes known as PlugX – has been used previously by other APT groups.

Palo Alto Networks previously released a lengthy report about PlugX and Thor in 2021, which they said was first discovered in 2008 and is a second-stage implant that’s been used by Chinese cyberespionage group PKPLUG – an alternate name for Mustang Panda – and other groups.
Côté Cyr noted that even though it is popular among APT groups, very little information is available about its commands and the data it exfiltrates.
“Its functionality is not constant between variants, but there does seem to exist a significant overlap in the list of commands between the version we analyzed and other sources such as the Avira report from January 2020 and the plugxdecoder project on GitHub,” Côté Cyr said.
“The RAT functionality of the Hodur variant used in this campaign mostly lines up with other Korplug variants, with some additional commands and characteristics.”
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



