FBI operation removed web shells from hacked Exchange servers across the US
The US Department of Justice announced today that a US judge granted the FBI the authority to log into web shells planted by hackers on Exchange email servers across the US and remove the malware as part of a mass-uninstall operation.
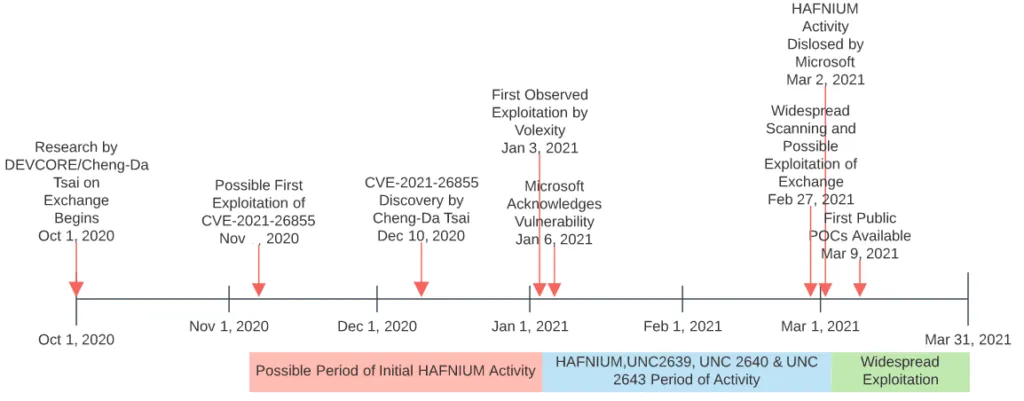
The web shells have been planted on Exchange servers by Chinese state-sponsored threat actors in a hacking campaign that took place through January and February 2021.
Multiple Chinese threat actors abused a quartet of security flaws —also commonly known as ProxyLogon— to take over Microsoft Exchange email servers, where they installed a web shell as a backdoor mechanism into corporate and government networks.
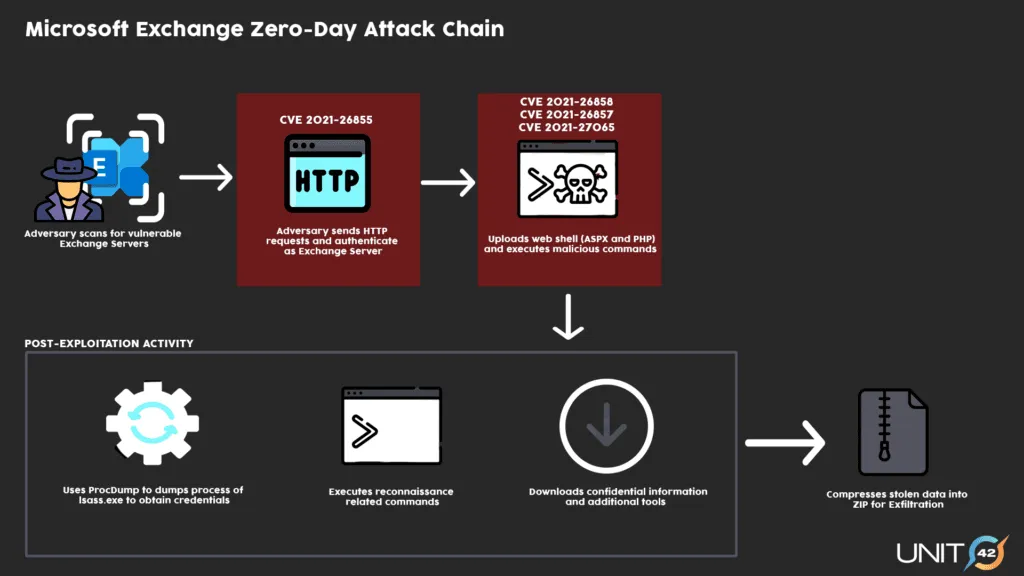
However, some of these web shells were not properly secured and reused the same password to grant the Chinese threat actors access to the hacked Exchange servers.
After Microsoft disclosed the attacks on March 2, other threat actors, such as ransomware groups (DearCry and Black Kingdom) and crypto-mining gangs (LemonDuck), also exploited this "flaw" to hijack Exchange servers and install their own set of malware.
But in a press release today, the DOJ said they used a court order to allow the FBI to access these same web shells with the same password and instruct the malware to uninstall itself.
DOJ officials said the FBI uninstalled the web shells to prevent them from being abused in future attacks.
"Today's court-authorized removal of the malicious web shells demonstrates the Department's commitment to disrupt hacking activity using all of our legal tools, not just prosecutions," said Assistant Attorney General John C. Demers for the Justice Department's National Security Division.
Officials also said the FBI did not patch Exchange servers during their recent operation, nor did they attempt to scan and remove other malware that may have been planted using the web shells.
These servers remain vulnerable to attacks using the ProxyLogon exploits, and officials encourage server owners to apply patches or mitigations as soon as possible, and then investigate and scan servers for any additional malware payloads that may have been deployed via the web shells prior to their removal.
Microsoft has released a simple one-click free tool to assist with this process.
The FBI did not say how many web shells they removed but said the operation was successful.
The Bureau is now in the process of notifying all companies where they intervened to remove web shells during its recent operation.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



