FBI, CISA investigating cyberattack on Puerto Rico’s water authority
The agency that manages Puerto Rico’s water supply has called in the FBI to investigate a cyberattack that occurred last week.
The investigation into the attack on the Puerto Rico Aqueduct and Sewer Authority (PRASA), which was announced on March 19, found that customer and employee information was compromised in the incident. But officials noted that the authority’s critical infrastructure was not affected by the incident due to network segmentation.
Doriel Pagán, executive president of PRASA's office of innovation and technology, said the agency had activated “security protocols” following the attack.
“It should be noted that once the incident was detected and from the first moment we have been working with the relevant authorities, the FBI and CISA [Cybersecurity and Infrastructure Security Agency], specifically,” he said.
Pagán, alongside executive director of Puerto Rico Innovation and Technology Service (PRITS) Nannette Martínez, added that the investigation is focusing on how the attackers got access, the scope of the breach and more.
PRASA did not respond to questions about what group was behind the attack but in a statement they said it was perpetrated by a “criminal organization [that] has already been identified at the national level.”
“Because this is an ongoing investigation, we are unable to comment further. However, we assure all our clients that the services offered by the Authority are still valid and we continue working to provide a quality and efficient service," Pagán said, noting that affected customers and employees will get more information in breach notification letters.
Officials urged customers to change their passwords, not just for their accounts with the authority but also on any platform where they may have used the same password.
On Friday, the Vice Society ransomware group added the authority to its list of victims, sharing samples of stolen documents that included passports, driver’s licenses and more.
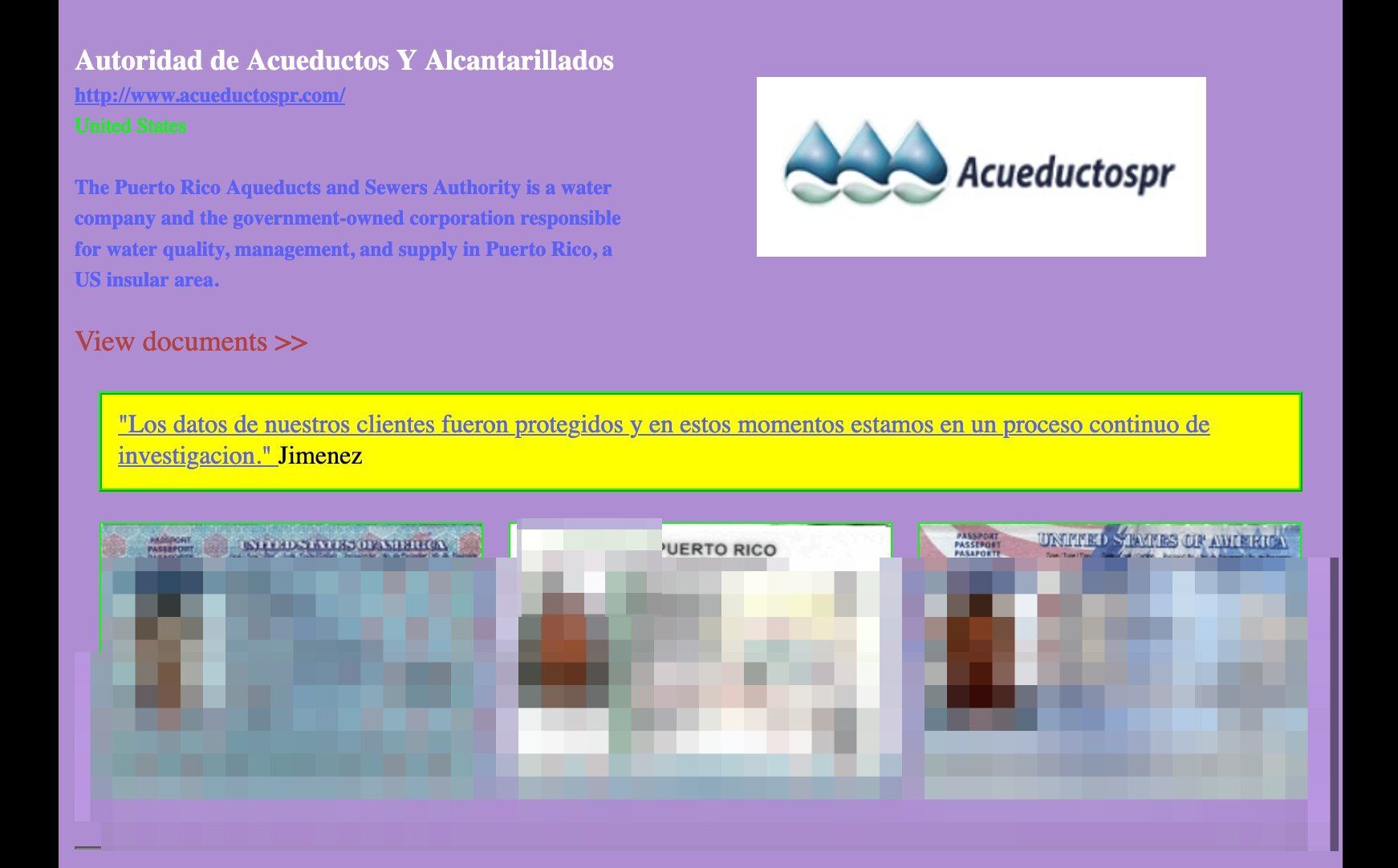 An image from Vice Society's post on its leak society. Credit: BetterCyber
An image from Vice Society's post on its leak society. Credit: BetterCyber
Vice Society has drawn headlines for dozens of attacks on K-12 schools and universities around the world since emerging in June 2021. But the group also “continues to focus on organizations where there are weaker security controls and a higher likelihood of compromise and ransom payout,” according to a Microsoft report released in October.
The attack comes just two weeks after the White House and U.S. Environmental Protection Agency (EPA) handed down new rules that order states and territories to assess the cybersecurity of drinking water systems.
“Cyberattacks against critical infrastructure facilities, including drinking water systems, are increasing, and public water systems are vulnerable. Cyberattacks have the potential to contaminate drinking water, which threatens public health,” EPA Assistant Administrator Radhika Fox said on a press call about the rules.
During the call, EPA officials said voluntary cybersecurity rules had “yielded minimal progress.”
Cyberattacks, they explained, have previously “shut down critical treatment processes, locked up control system networks behind ransomware, and disabled communications used to monitor and control distribution system infrastructure like pumping stations.”
“Including cybersecurity in PWS [public water systems] sanitary surveys, or equivalent alternate programs, is an essential tool to address vulnerabilities and mitigate consequences, which can reduce the risk of a successful cyberattack on a PWS and improve recovery if a cyber incident occurs,” they said.
U.S. law enforcement agencies said ransomware gangs hit five U.S. water and wastewater treatment facilities from 2019 to 2021 — and those figures did not include three other widely-reported cyberattacks on water utilities.
Correction: An earlier version of this story misattributed quotes made by PRASA's Doriel Pagán to Nannette Martínez.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



