Double Extortion Ransomware May Be the New Normal
Late last year, a security staffing company was hit with what was then a novel type of attack: their data was locked up and held for ransom—similar to a traditional ransomware infection—but when they failed to pay the multimillion-dollar demand, the hackers started posting data stolen from the company online.
This so-called double extortion ransomware attack threw a wrench in the conventional wisdom for how to minimize the impact of these incidents. Well-maintained backups, for example, might help an organization resume operations after falling victim to a ransomware attack, but they’re of no help if criminals threaten to expose sensitive corporate data.
Although this style of attack started with a single criminal group, other ransomware operators have adopted the technique over the last year. And according to a report released today by Recorded Future, indicators over the last several months suggest that double extortion ransomware is likely here to stay.
“Double extortion is not a flash in the pan—it’s a pretty common tactic across the board for new and existing ransomware families,” said David Carver, a manager in the company’s research team. “I don’t see it as likely that we’ll see this trend discontinue or go down.”
From July to September, a handful of new ransomware extortion websites emerged as cybercriminals embraced the tactic as a way to pressure organizations to pay demands, the report found. For example, several victims of the SunCrypt ransomware group—including a school system and hospital—had their data exposed on a website launched in August. In late September, operators associated with the Egregor ransomware family started posting samples of stolen data online giving victims three days to pay the ransom before continuing the leak. Around the same time, operators of a new ransomware dubbed MountLocker threatened to publish stolen data if victims didn’t pay a $2 million ransom, according to the report.
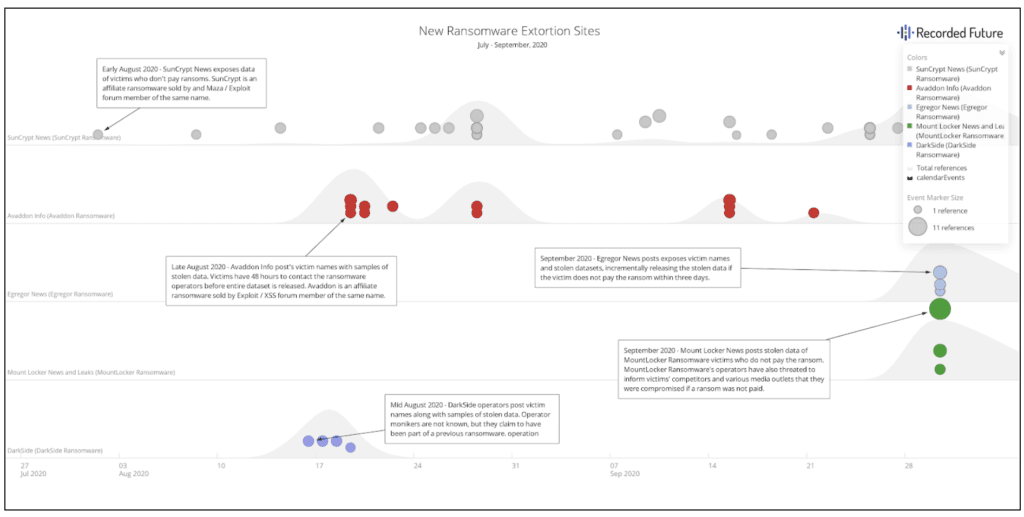
These groups are just the latest in a trend that dates back to late last year, Carver said.
“At the end of 2019, it was just the Maze ransomware group, then pretty quickly in early 2020 a couple other operators jumped on board. In the last few months, another five to ten jumped up. It’s not a trend line that’s tapering out,” he said.
Notably, the Maze group posted on its website last week that it would be shutting down, though the typo-filled statement didn’t give a clear reason for the change. One possibility is that the group will develop a new infrastructure and retrofit their tactics due in part to the attention Maze has received, Carver said.
He added that additional groups are expected to jump on the trend as they see it as a way to increase profits and raise their reputation among cybercriminals and information security specialists.
“I’m generally optimistic, but In the short term this is not something I have a lot of hope for,” he said.
Adam Janofsky
is the founding editor-in-chief of The Record from Recorded Future News. He previously was the cybersecurity and privacy reporter for Protocol, and prior to that covered cybersecurity, AI, and other emerging technology for The Wall Street Journal.



