CloudFlare says it stopped largest HTTPS DDoS attack on record last week
Internet infrastructure company Cloudflare said on Tuesday that it recently caught and mitigated the largest HTTPS distributed denial of service (DDoS) attack ever recorded.
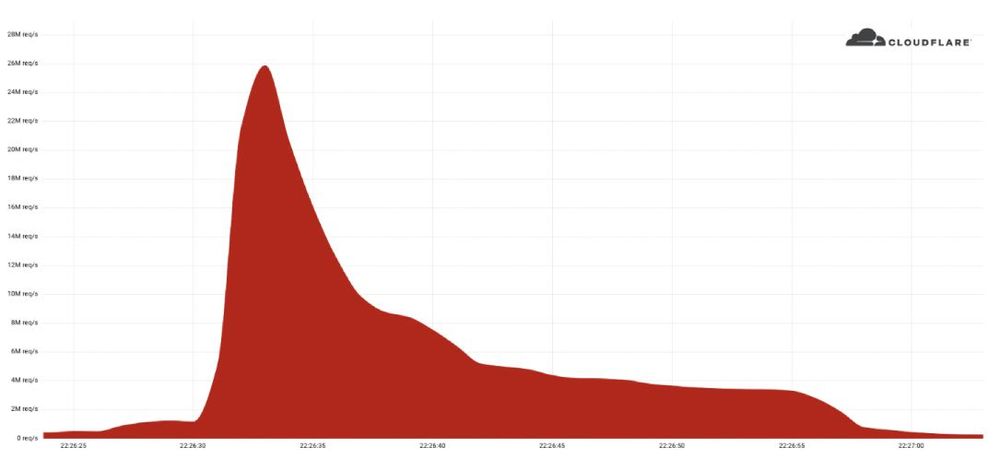
The 26 million request per second (rps) DDoS attack was launched at the website of a Cloudflare customer last week, according to a blog post from product manager Omer Yoachimik.
Yoachimik said the attack “originated mostly from Cloud Service Providers as opposed to Residential Internet Service Providers, indicating the use of hijacked virtual machines and powerful servers to generate the attack — as opposed to much weaker Internet of Things (IoT) devices.”
The company was able to trace the attack back to a powerful botnet of 5,067 devices, each of which generated approximately 5,200 rps at peak.
“To contrast the size of this botnet, we’ve been tracking another much larger but less powerful botnet of over 730,000 devices. The latter, larger botnet wasn’t able to generate more than one million requests per second, i.e. roughly 1.3 requests per second on average per device,” Yoachimik said.
“Putting it plainly, this botnet was, on average, 4,000 times stronger due to its use of virtual machines and servers.”
Volumetric DDoS attacks differ from traditional bandwidth DDoS attacks where attackers attempt to exhaust and clog up the victim’s internet connection bandwidth. Instead, attackers focus on sending as many junk HTTP requests to a victim’s server in order to take up precious server CPU and RAM and prevent legitimate users from using targeted sites.
CloudFlare noted that HTTPS DDoS are typically more costly than others because they require more computational resources and need a secure TLS encrypted connection.
Yoachimik said the attack stood out “because of the resources it required at its scale.”
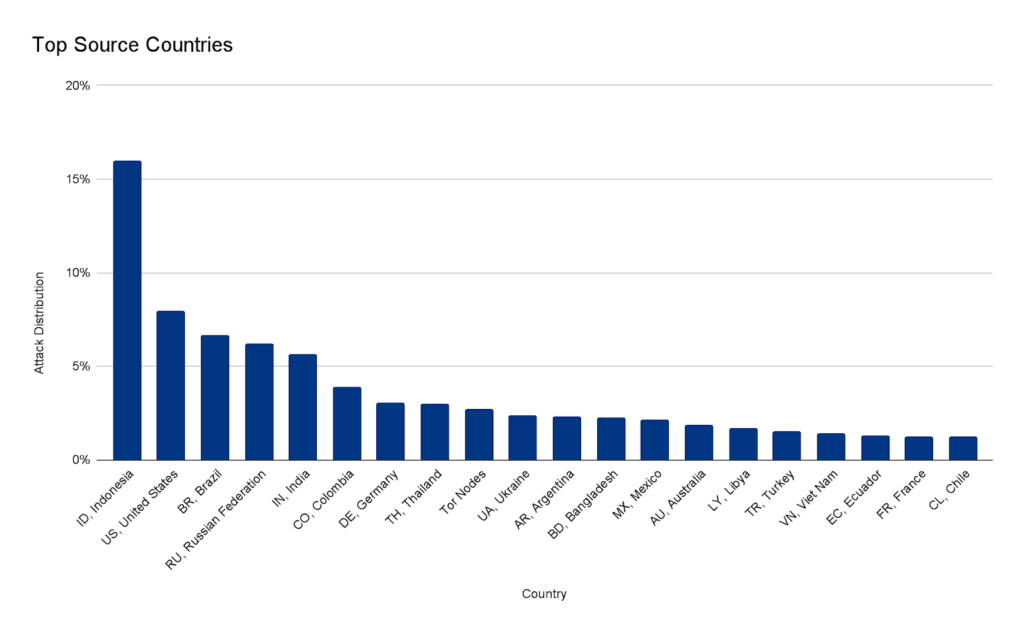
“Within less than 30 seconds, this botnet generated more than 212 million HTTPS requests from over 1,500 networks in 121 countries. The top countries were Indonesia, the United States, Brazil and Russia. About 3% of the attack came through Tor nodes,” Yoachimik said.
“The top source networks were the French-based OVH (Autonomous System Number 16276), the Indonesian Telkomnet (ASN 7713), the US-based iboss (ASN 137922) and the Libyan Ajeel (ASN 37284).”
The company has repeatedly reported that the size and scale of DDoS attacks has increased in recent years. In April, CloudFlare stopped a 15.3 million rps DDoS attack, the second largest recorded at that point.
That attack was targeting a cryptocurrency company, lasted less than 15 seconds, was launched from a botnet of approximately 6,000 unique bots and originated from 112 countries around the world. Almost 15% of the attack traffic originated from Indonesia, followed by Russia, Brazil, India, Colombia, and the United States, according to Cloudflare data.
The previous record occurred in August 2021, when they mitigated a 17.2M rps HTTP DDoS attack. That attack was almost three times larger than any previous volumetric DDoS attack that was ever reported in the public domain.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.